How to Configure a Protection Object: IP Addresses, Load Balancing, SSL, and Caching
In the left-hand menu, select Protected Object.
On the page that opens, you’ll see configurable parameters that you can adjust to fit your needs or preferences:
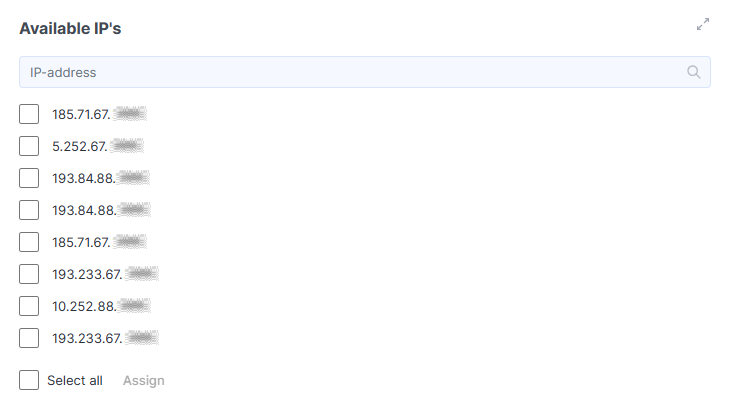
Available IP’s
On the page that opens, you will find configurable parameters, including Available IPs. To assign an IP address from the list, check the box at the beginning of the row and click Assign. We will provide you with several IP addresses, and you can assign them to your domains yourself.
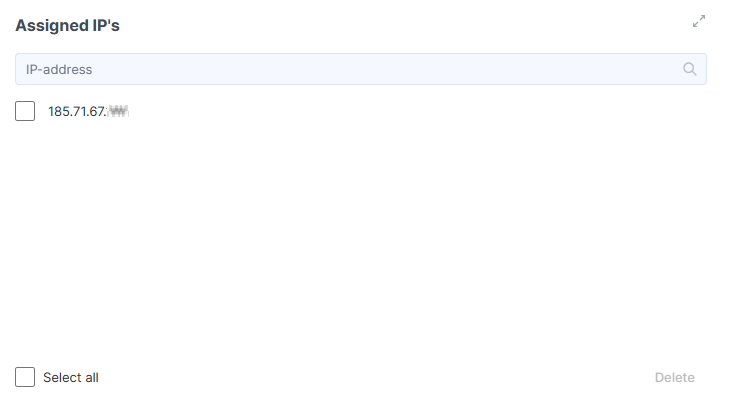
Assigned IP’s
You can remove IP addresses from the list of assigned ones. To do this, select the address you no longer need by checking the box at the beginning of its row, then click Delete.
Backend servers
The service provides load balancing across multiple backend servers.
A backend is your server located behind the protection system. It processes user requests that have been filtered for attacks and generates responses.
How It Works
- Users send requests over the internet.
- The protection system intercepts and filters the traffic.
- The filtered requests are forwarded to your backend servers.
- The server processes the requests and returns responses to the users.
You can also specify the protocol used to access the backend servers: HTTP (port 80) or HTTPS (port 443).
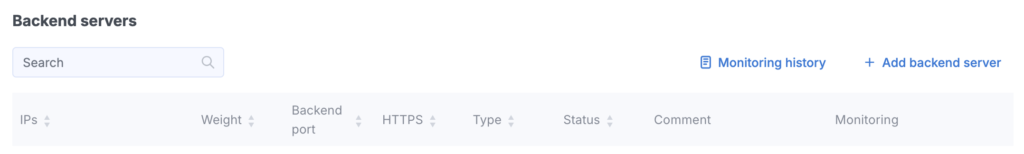
To add a backend server, click the Add Backend button and fill out the form:
IP Address – The backend server address that will receive the filtered traffic.
Domain Port – The port where user traffic is initially received.
Backend Port – The port where filtered traffic is forwarded (may match or differ from the domain port).
Type – Select one of the following:
- Balance – For load-balanced servers (default).
- Backup – For failover servers (used only if the primary servers are unavailable).
Weight – Defines how traffic is distributed (higher weight = more requests).
Example:
With three servers weighted 5, 1, and 1, out of seven requests:
- 5 requests go to the first server
- 1 request goes to the second
- 1 request goes to the third
Toggle HTTPS to ON if using port 443.
After completing the form, click Add. You can later modify backend settings using the Settings button.
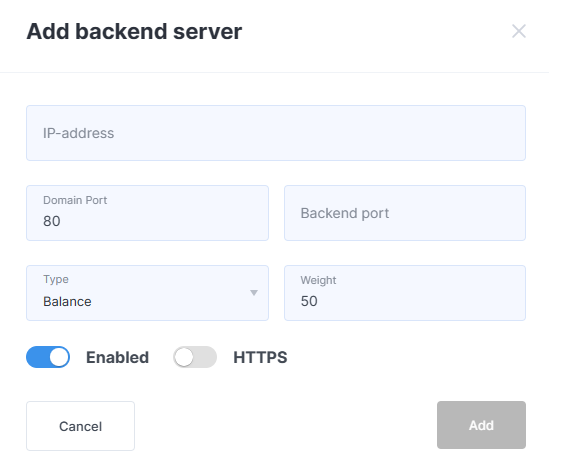
Added objects will appear in the table. Using the buttons on the right side of each row, you can modify or delete a backend server.
If you have three backend servers with weights 3, 1, and 1, then out of 5 requests:
To change the primary backend for a domain protected by the WAF, please contact technical support. Our specialists will apply the change as quickly as possible.
In the Monitoring column, the backend status is displayed:
- A red exclamation mark indicates a problem with the backend (hover over the icon to see a description of the issue).
- A green check mark means the backend is being monitored and no issues have been detected.
- No icon means the backend is not set up for monitoring.
The edit form is identical to the backend addition form. A warning will appear when attempting to delete an enabled backend.
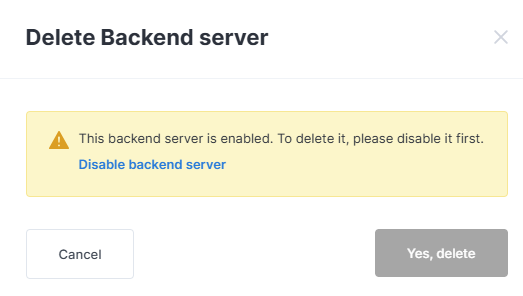
Click the Disable backend server button, then confirm its deletion.
Click the Settings button to proceed to the monitoring settings.
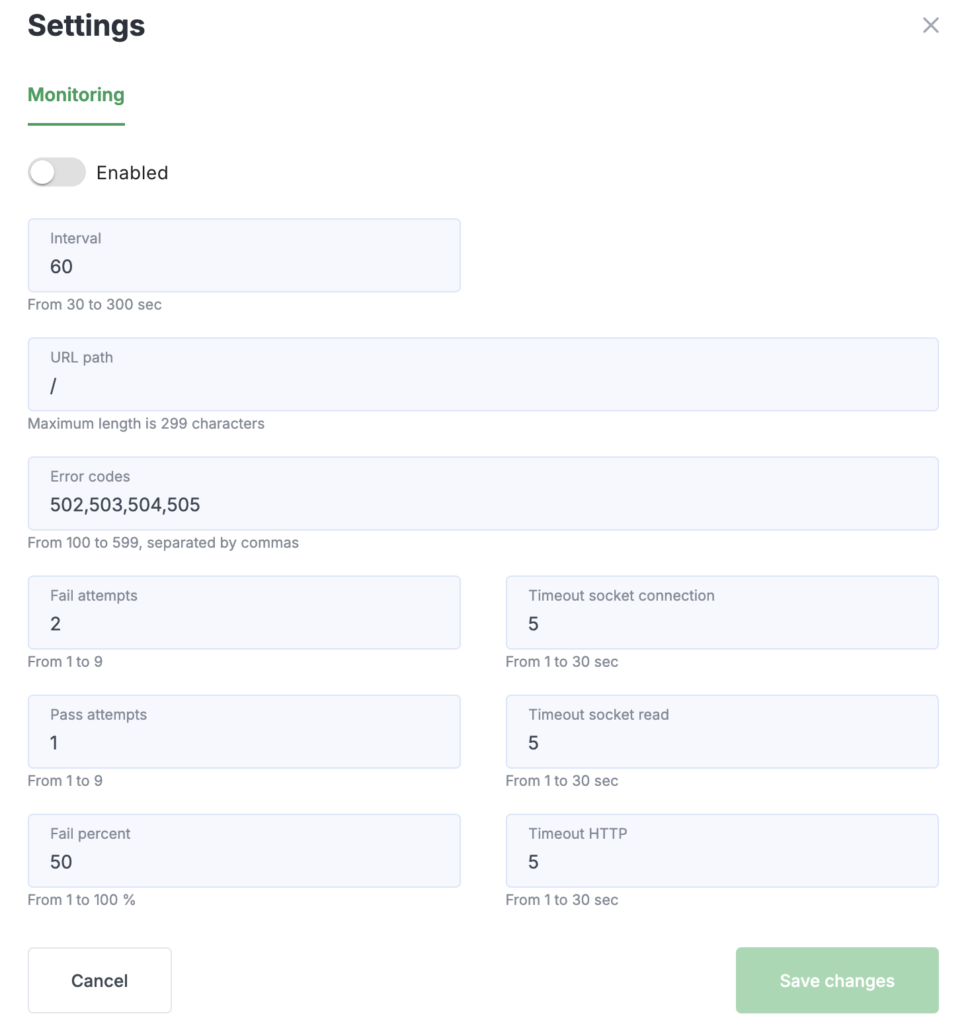
In the window that opens, you can use the toggle to enable or disable monitoring for backends, as well as configure the following parameters:
- Interval — frequency of backend health checks (in seconds);
- URL Path — the endpoint for monitoring, where HTTP requests are sent;
- Error codes — list of HTTP status codes considered indicative of unavailability;
- Fail attempts — how many consecutive failed attempts will mark a backend as unavailable;
- Pass attempts — how many consecutive successful attempts will mark a backend as available;
- Fail percent — the percentage of failed checks from the total number required to declare a backend unavailable (this parameter helps avoid removing a backend from load balancing if it is unreachable from only one of several monitoring locations);
- Timeout socket connection — timeout for establishing a TCP connection;
- Timeout socket read — timeout for reading data from a socket;
- Timeout HTTP — overall timeout for the HTTP request execution.
WebSocket Ports
Configure the settings to protect your website from DDoS attacks targeting WebSocket protocol vulnerabilities.
If your site uses the standard WebSocket ports (80 and 443), no special server protection settings are required.
If non-standard ports are used, you must create a special configuration by specifying those ports. If needed, you can also configure load balancing between backend servers.
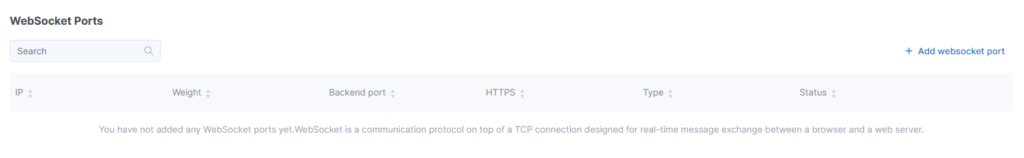
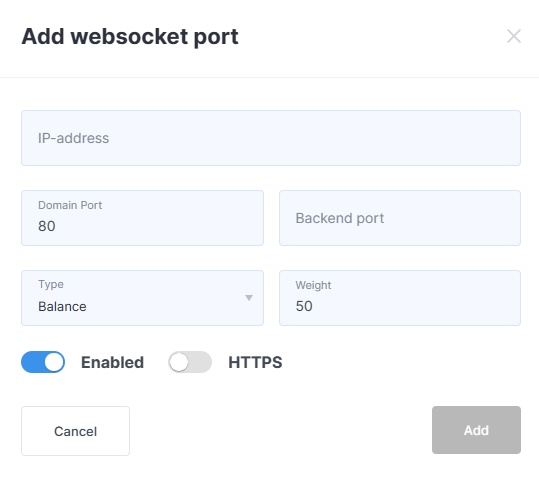
Click the Add WebSocket Port button. Fill out the form, then click Add to complete the process. If the Add WebSocket Port button is inactive, it means the maximum number of ports has been reached.
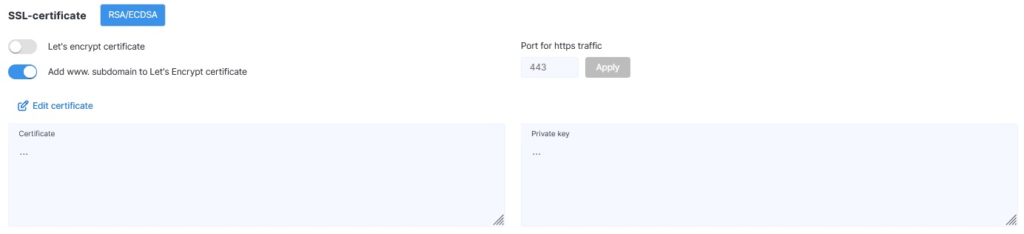
SSL certificate
You can obtain a free SSL certificate (from Let’s Encrypt) or install your own. You can also enable or disable redirection from HTTP to HTTPS (or vice versa) to help reduce the load on the origin server.
- Own Certificate
To inspect SSL traffic, you need to specify both the public key certificate and the private key. On the screen, these will be displayed in truncated form (to prevent copying). You must also provide the root and intermediate CA certificates (if applicable).
If you are using your own certificate, you will need to update it manually when it expires.
Note: All SSL certificates must begin with “BEGIN CERTIFICATE” and end with “END CERTIFICATE”. The certificate authority typically provides this set of files marked “For Apache/Nginx”. The domain’s private key must start with the header “BEGIN RSA PRIVATE KEY”.
Before pasting the certificate into the form field, make sure the Let’s Encrypt Certificate toggle is set to OFF.
If you receive a certificate validity error, check the following:
- Verify the certificate fields (Common Name, SANs, Validity period).
- Use openssl to compare the hashes of the certificate and key.
- Check the entire certificate chain to ensure it validates correctly.
- Free New Certificate
If you don’t have a certificate or prefer not to enter its data into your personal account, you can enable the Let’s Encrypt Certificate option. In this case, client keys will be generated and a public key certificate will be issued for the protected server. The certificate and key will be automatically regenerated and replaced ten days before they expire.
To use this type of certificate, the domain’s primary A record, as well as its www.\* record, must point to the assigned protected IP address.
The certificate will be installed automatically within a few minutes. If you receive a DNS record mismatch error, please wait — domain zone updates may take anywhere from 15 minutes to several hours, depending on the TTL value previously set in the domain’s A record and your internet provider’s DNS update frequency.
Cache
Thanks to caching, your website will become not only more reliable but also faster.
Static content is cached in the RAM of StormWall’s scrubbing center servers, which significantly reduces the load on the origin server.
You can set the cache lifetime and choose which file types to cache. If you need additional parameters (such as geographic restrictions), please contact technical support.
To enable caching, select the cache lifetime and file extensions, then switch the Cache toggle to the ON position.
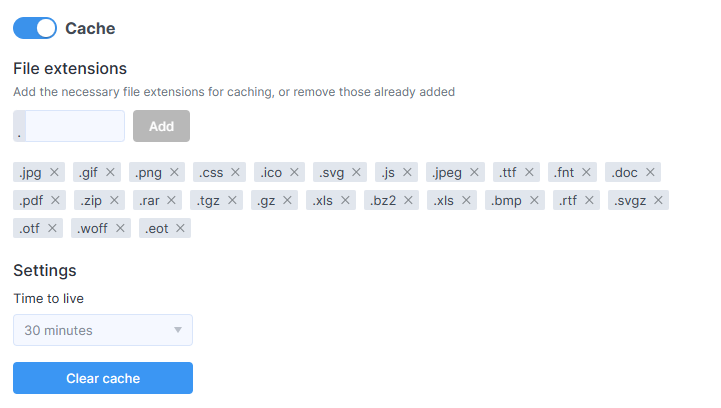
When you press the Clear cache button, all data will be reloaded from the resources anew.
Redirects
Configure the rules for redirecting traffic between different addresses.
For example, here you can set up a redirect from “http” to “https”.