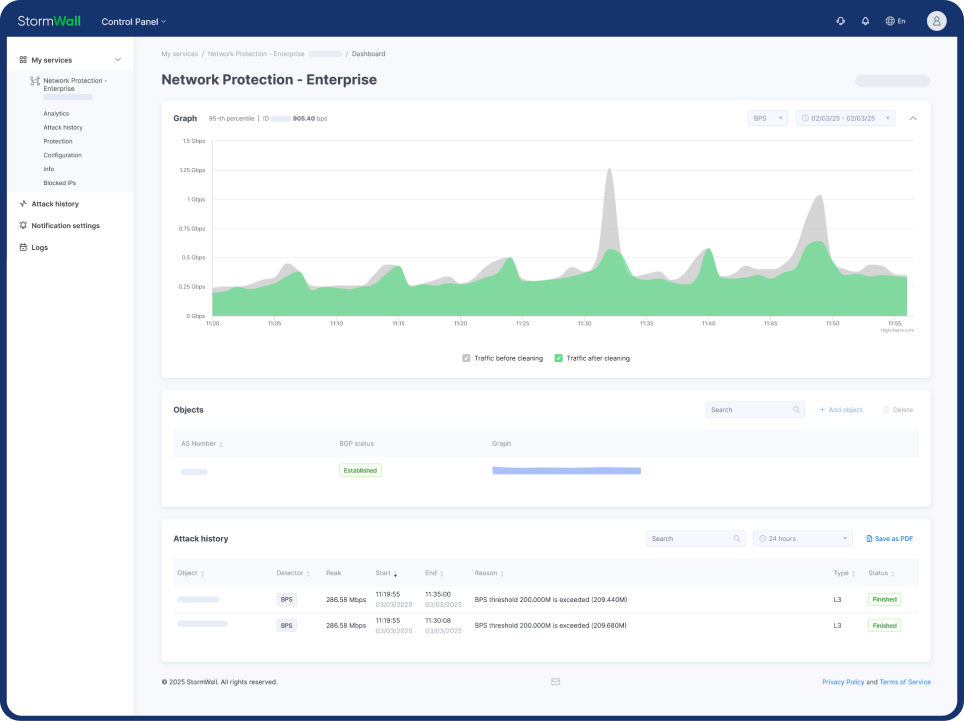
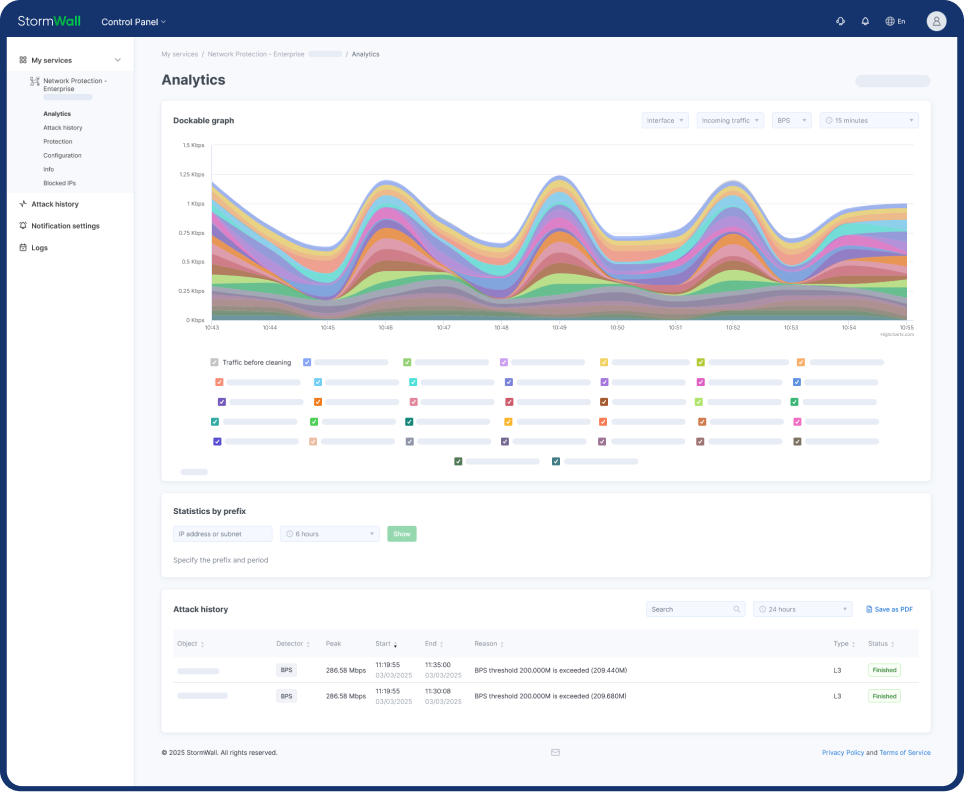
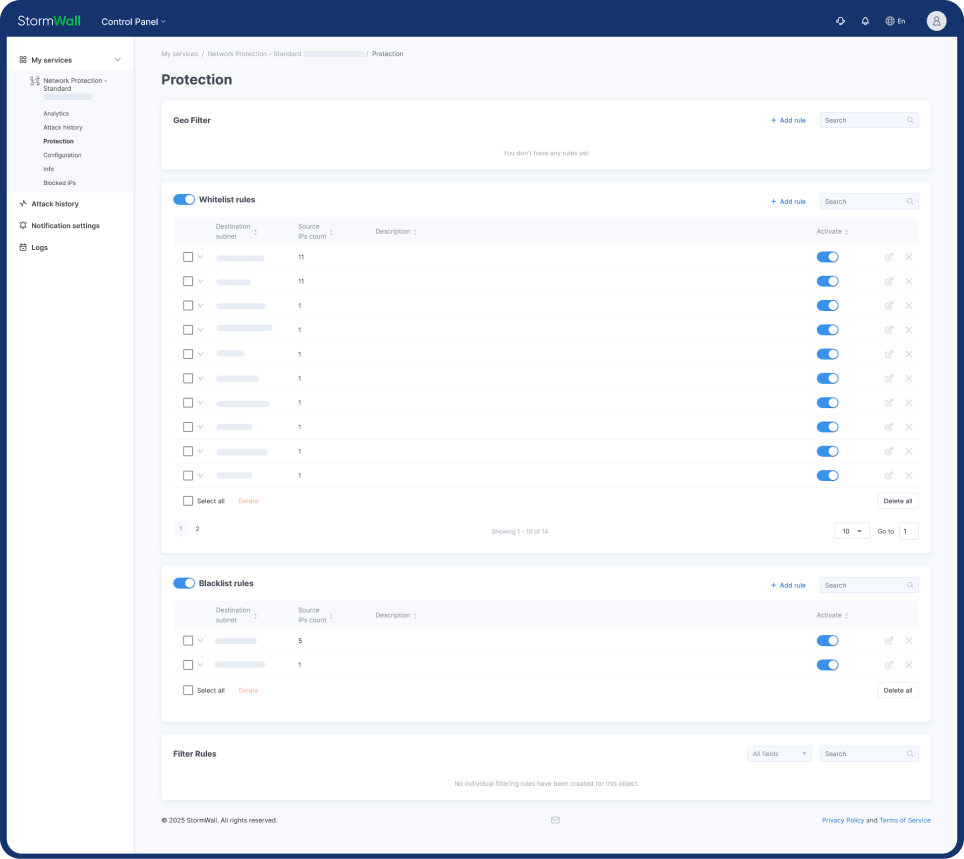
DDoS Protection for TCP/UDP Services
StormWall for Servers
TCP/UDP




















StormWall for Web
WAF and DDoS protection for web applications

StormWall for Networks
DDoS protection for networks via BGP

StormWall for Servers
DDoS protection for TCP/UDP services

Antibot
Reliable protection of web applications from bots

Enterprise-Grade WAF
Protecting web applications with a cloud‑based security tool

Content Delivery Network (CDN)
CDN service to speed up content loading

Blog
Company and industry news, educational articles

How StormWall Works
Explore how our services can protect infrastructure from any type of attack

User Guide
Detailed guide on using the Client Portal

Success Stories
Articles with customer case studies

Technology
How StormWall DDoS protection works

API
Automate management of StormWall DDoS protection

Knowledge Base
Cybersecurity terms and definitions

StormWall Partner Program
For resellers and service providers

White Label
Use StormWall DDoS protection under your brand

Affiliates
Attract clients to protect sites from DDoS - and increase your income

About StormWall
Learn more about our company, see contact details and terms of service

Our Clients
Companies protected by us over the years

Media
Articles featuring our company

Why StormWall
Our benefits

















