April-May 2025 saw a record 236% spike in DDoS attacks across the MENA region—with Saudi Arabia topping the list of most targeted countries. Explore this and other key insights in our DDoS attack report.

Key Trends
DDoS attacks in the MENA region surged to record highs in Q2 2025, driven by a series of major developments:
- Geopolitical tensions in the Middle East escalated sharply due to two major conflicts: Israel–Palestine and Iran–Israel.
- The most frequently targeted industries in MENA were finance, government, and telecommunications.
- API attacks over HTTP/HTTPS spiked 162% year-over-year.
- Hackers also adopted a new technique—probing—using short bursts of low-volume DDoS traffic to search for vulnerabilities. The number of these attacks increased by nine times.
Let’s take a closer look at these trends.
New DDoS Attack Playbook
APIs Under Fire
In the second quarter of 2025, API-targeted DDoS attacks rose by 162% year-over-year. These attacks are especially difficult to defend against because they closely mimic legitimate traffic patterns, making them harder to detect and block.
Over 80% of these attacks were launched using botnets made up of hacked devices. The average size of a botnet tracked in the region has grown to about 140,000 devices.
Unlike traditional DDoS attacks that rely on overwhelming a system with large volumes of traffic, API attacks exploit the way APIs function—causing disruption to critical services with far less data. On average, an API attack generated just 4.7 Gbps of traffic. Still, that was enough to take down a target using only 12% of the volume typically needed for a standard flood.
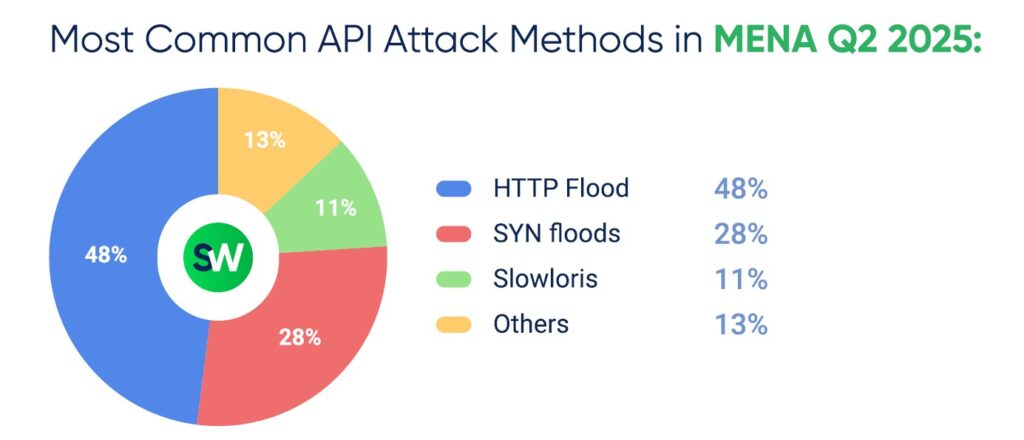
Read more: How to Protect Your API from DDoS Attacks
DDoS Prep: Probing Spikes
In Q2 2025, the number of probing (reconnaissance) attacks in the MENA region increased 9 times, signaling a major tactical shift in how DDoS campaigns are prepared.
These attacks involve scanning networks to detect open ports and services, identify weak points, and test defenses—all before launching a full-scale assault. Typically low in volume, such bursts of DDoS traffic are designed to blend in with legitimate activity and often go unnoticed by traditional security systems.
This change in tactics makes DDoS attacks more targeted, harder to detect in advance, and far more dangerous for organizations across the Middle East and North Africa.
Attacks by Industry
Now, let’s break down the distribution of DDoS attacks by industry in MENA in Q2 2025:
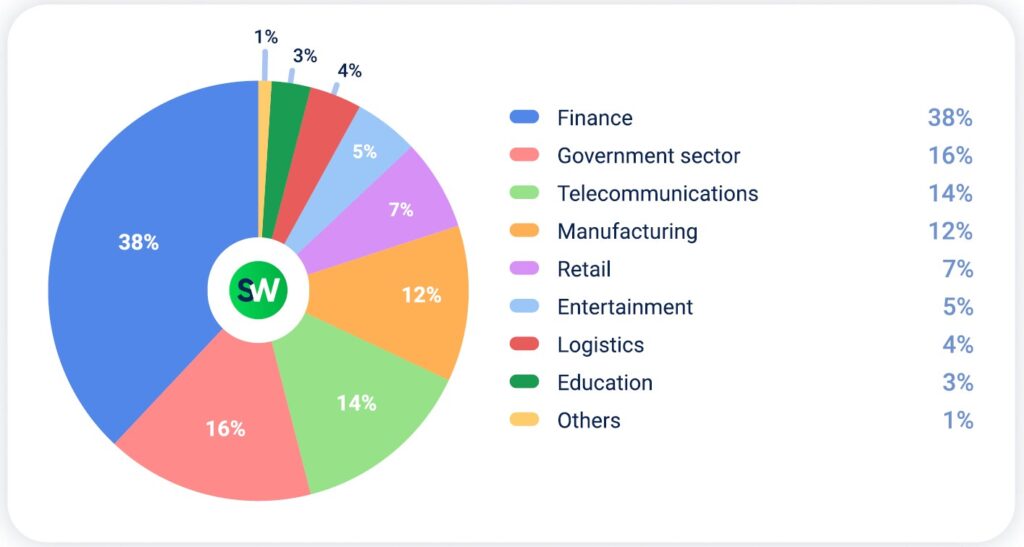
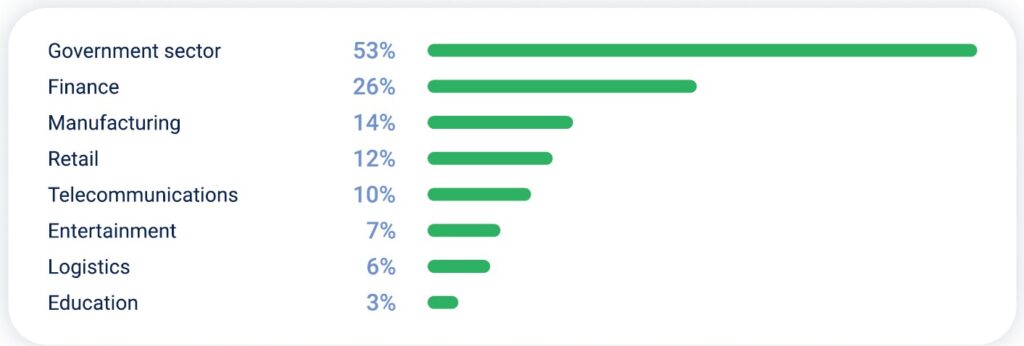
Industries with highest YoY growth in DDoS attacks in MENA in Q2 2025:
Who Is at Most Risk for a DDoS Attack?
What vertical is most likely to be attacked and what vertical is least likely to be attacked? The table below shows the relative likelihood by sector:
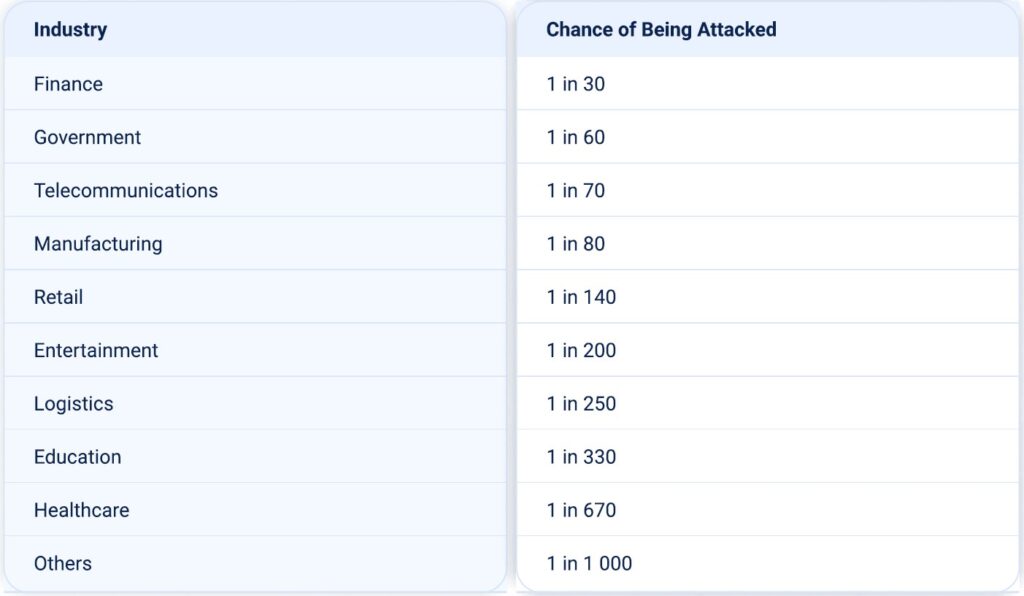
Note: This reflects the relative risk within the MENA region, based solely on the observed distribution of DDoS attacks. Actual risk may vary depending on factors like exposure surface, security posture, and threat actor interest.
In the Crosshairs: Top 3 Most Targeted Industries
1. Finance

In Q2 2025, financial services were the most heavily targeted sector in MENA. Roughly 79% of cyberattacks focused on banking APIs and payment processing systems.
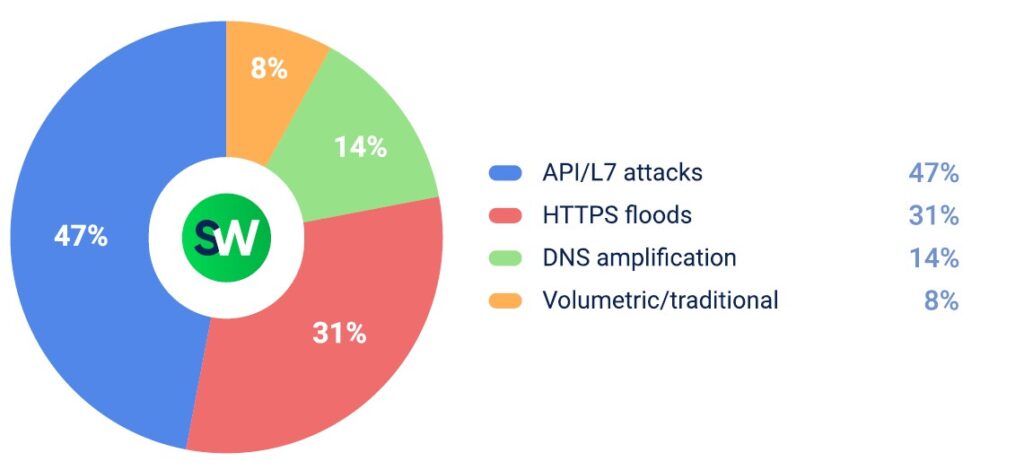
The largest attack in this vertical reached 1.8 Tbps and hit a bank in the UAE. The longest-lasting campaign ran for 6 days at around 380 Gbps, while the average attack duration was 14 minutes.
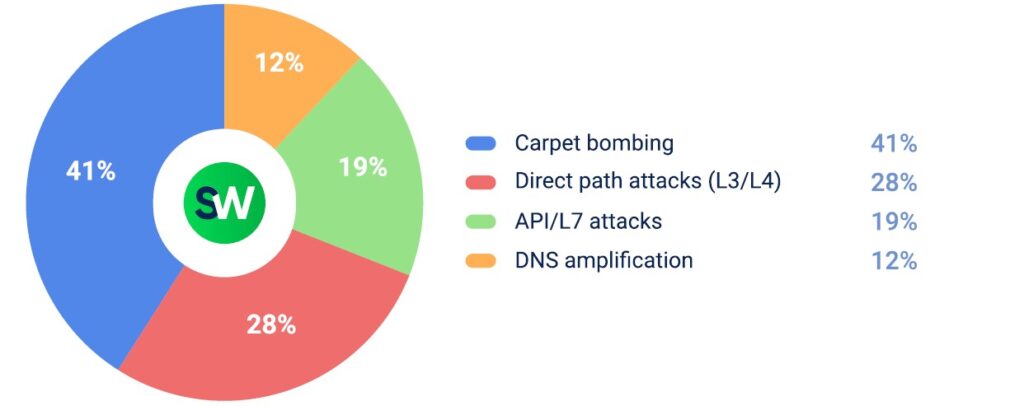
2. Government

Government infrastructure came under the second-highest volume of attacks in Q2. Escalating tensions between Iran and Israel led to a sharp increase in targeting of public-sector systems. Within this vertical, 68% of attacks were directed at national government websites.
The most frequently used method was carpet bombing—a tactic involving widespread, low-volume attacks to overwhelm multiple targets at once.
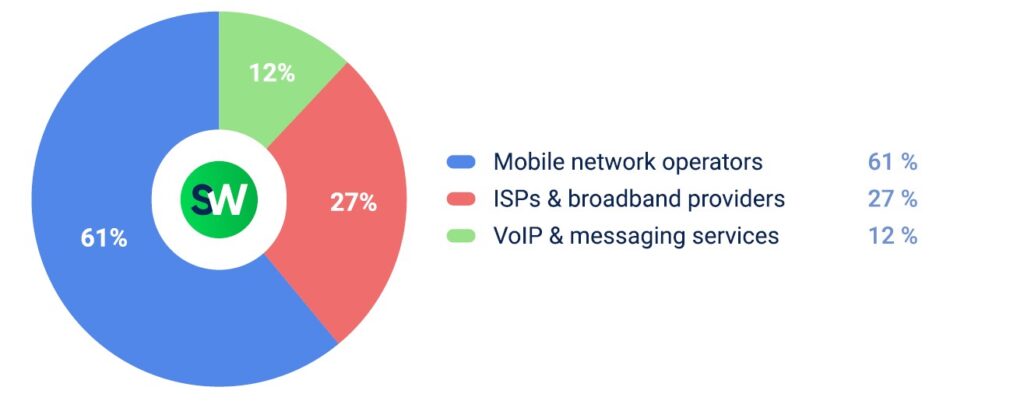
3. Telecommunications

Telecom companies, especially mobile network operators, were another top target.
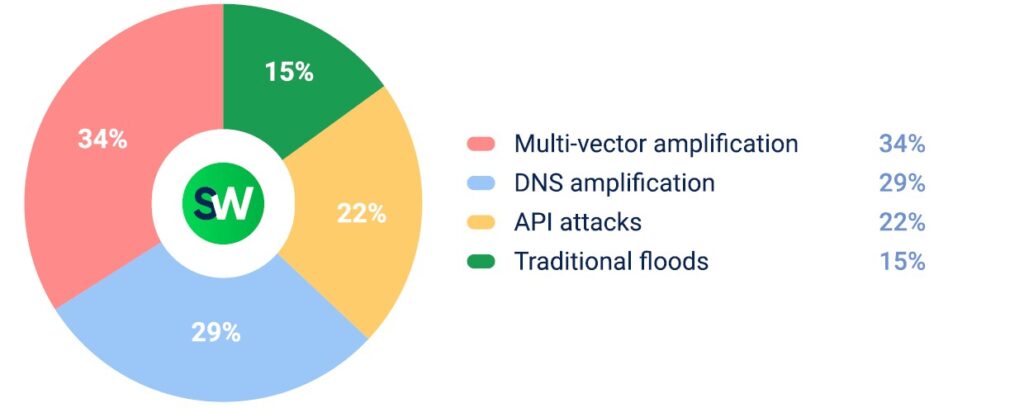
Multi-vector amplification attacks dominated in this sector, exploiting the telecom industry’s critical role in maintaining regional connectivity and communications:
DDoS Attacks by Country
Let’s take a closer look at the distribution of DDoS attacks by country in MENA in Q2 2025:
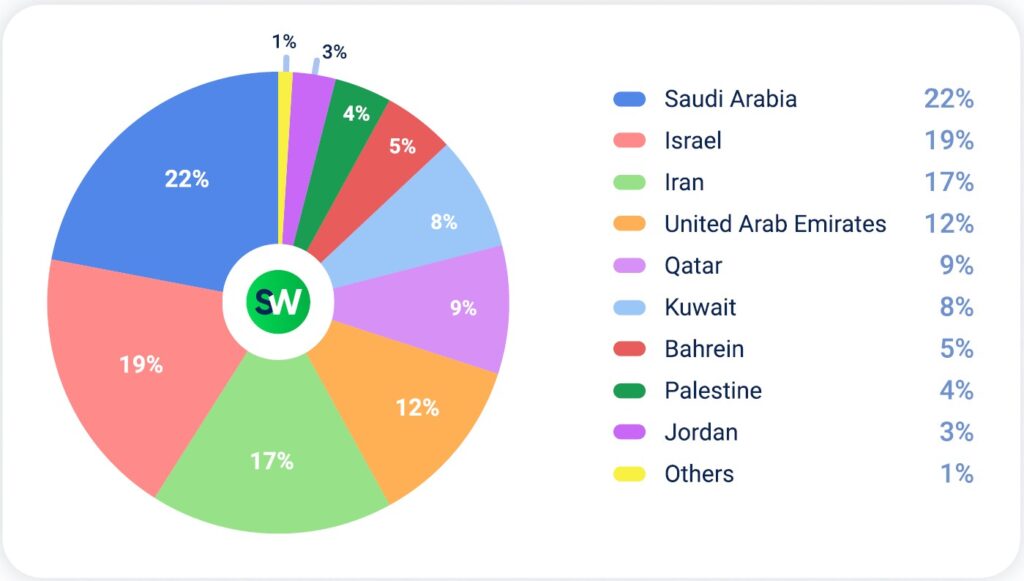
Saudi Arabia remained the most targeted country, although its share of attacks dropped from 28% in Q1 to 22% in Q2.
Iran’s share held steady, rising slightly from 16% to 17%. On June 18, 2025, a pro-China hacker group launched a devastating attack on Nobitex, Iran’s largest crypto exchange. The attackers destroyed over $90 million worth of digital assets in cryptocurrencies such as Bitcoin, Ethereum, and Dogecoin. Instead of stealing the funds for profit, the hackers transferred them to “vanity addresses” containing anti-Iranian messages—effectively burning the assets. This pointed to a politically motivated campaign of destruction.
The same group also claimed responsibility for a June 17 cyberattack on Iran’s state-owned Bank Sepah, allegedly wiping data tied to the Islamic Revolutionary Guard Corps (IRGC) and causing widespread ATM outages across the country.
Israel saw a 73% increase in attacks quarter-over-quarter, rising from 11% to 19%. This surge was directly linked to escalating conflict with Iran.
Iran reportedly used GPS spoofing to disrupt Israeli infrastructure. In June 2025, nearly 1,000 ships in the Persian Gulf experienced GPS interference. Iranian operatives also compromised thousands of Israeli surveillance cameras to collect real-time intelligence and assess the impact of missile strikes. These breaches exploited vulnerabilities in Chinese-made camera equipment. Israeli cybersecurity officials warned that around 66,000 personal cameras in Israel were protected by easily guessable passwords and were highly vulnerable to compromise.
Other notable shifts from Q1 to Q2 2025:
- Palestine: 2% → 4%
- Qatar: 8% → 9%
- Bahrain: 7% → 5%
- Kuwait: 6% → 8%
During Q2 2025, a total of 8.2 million DDoS attacks targeted Israel’s digital infrastructure—over four times the number recorded in Q1. Most of these (6.1 million incidents) were multi-vector attacks, including carpet bombing campaigns, API attacks, and state-sponsored flooding operations.
Most incidents lasted less than 8 minutes, with the most severe attacks occurring during the first two weeks of May, coinciding with intensified military action.
Summary
Given the current political situation in the MENA region, hacktivists now account for 73% of all malicious traffic. The explosive growth of probing attacks highlights a major shift in tactics. Instead of relying on brute force and raw power, attackers are now acting with greater precision and focus.
In this environment, operating without professional protection is extremely risky. We recommend looking into security solutions designed with regional specifics in mind. StormWall is one of them.

DDoS Protection for Websites
- Activate protection in 10 minutes
- 24/7 technical support




















