Q2 2025 saw a sharp rise in DDoS attacks worldwide—up 108% year-over-year. What’s driving this surge? Which countries and industries are being hit the hardest? And which attack methods are cybercriminals using most often now? Find all answers in our report.

Key DDoS Trends in Q2 2025
Before we dive into the full analysis, here’s a quick look at what defined Q2 2025:
- Geopolitical conflicts fueled record levels of hacktivist activity. Rising tensions between India and Pakistan added to ongoing conflicts like Russia–Ukraine and Israel–Iran, triggering waves of coordinated attacks on government systems.
- Government services, financial institutions, and transportation were the hardest hit. These three sectors alone absorbed 63% of all global DDoS attacks.
- API attacks rose by 74% year-over-year. Attackers increasingly shifted from high-volume floods to precise strikes on API endpoints.
- Probing attacks skyrocketed—up 5,000x compared to Q2 2024. Threat actors are now systematically scanning networks before launching full-scale campaigns. Notably, 92% of large DDoS attacks on government infrastructure were preceded by probing activity.
Let’s explore these patterns in more detail.
Cybercriminals Shift Tactics
API Attacks Surge 74% Year-over-Year
API attacks rose by 74% YoY in Q2 2025, as threat actors continued shifting toward high-impact, low-effort tactics.
Geopolitical groups increasingly weaponized these attacks, especially targeting government services in regions affected by conflict. On a technical level, these attacks remain difficult to detect and mitigate, as they closely mimic legitimate traffic. The sophistication of these attacks has also noticeably increased since the previous quarter.
Some key insights from Q2:
- 68% of attacks used HTTPS, up from 63% in Q1—making it harder to inspect and filter packets using traditional tools.
- 81% of HTTP-based DDoS traffic came from botnets, a jump from 70% last quarter.
- Average attack size dropped to 3.7 Gbps, down from 5.2 Gbps in Q1. Smaller, targeted floods are proving more effective than traditional volumetric attacks, which tend to be more brute-force in nature.
Attackers also enhanced the tactic first seen in Q1—rotating user-agent strings and cookies to make malicious requests appear like real browser traffic.
The result: API-layer attacks caused service outages that lasted 4.2× longer than those from traditional network-layer attacks—while using up to 90% less bandwidth.
Read more: How to Protect Your API from DDoS Attacks
Probing Attacks Up 5000x
Probing attacks—where attackers send low-volume DDoS traffic to scan defenses before launching a full-scale campaign—skyrocketed 5,000 times year-over-year in Q2 2025.
Both geopolitical and cybercriminal groups increasingly used probing to identify weak spots in high-value targets. Unlike traditional “smash-and-grab” DDoS attacks, probing gives attackers a strategic edge by:
- Uncovering firewall misconfigurations and rate-limit gaps
- Exposing reliance on outdated or misconfigured DDoS protection
- Allowing faster, more effective bypass of defenses
In practice, this means that if a well-equipped DDoS group sets its sights on a company still using legacy protection, that company is now six times more likely to suffer a successful breach due to exposed vulnerabilities.
Botnets Are Growing in Size Fast
In Q2 2025, botnets expanded rapidly. The average botnet now consists of around 120,000 to 150,000 infected devices—up from 80,000 to 90,000 in Q1. That’s an increase of about 87% in just three months.
The United States led the surge with a 180% rise in compromised devices. Russia followed with 36% growth, and Turkey entered the top three for the first time.
Why does this matter? Larger botnets mean stronger attacks. A botnet with 150,000 devices can generate 15–30 Gbps of DDoS traffic—enough to overwhelm systems with brute force alone.
Key points to know:
- Botnet attack power has nearly doubled.
- Attacks are now more distributed, often coming from multiple regions at once.
- Companies still relying on Q1-level protection may now be under-protected by as much as 50%.
Read more: What Are Botnets and How Are They Used in DDoS Attacks?
Hackers’ Hit List: Top Targeted Industries
Now, let’s break down the distribution of DDoS attacks by industry in Q2 2025:
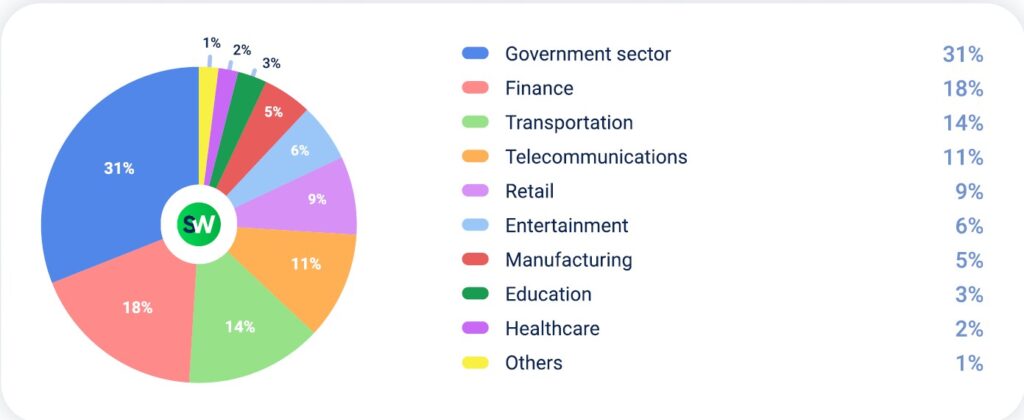
Sectors with highest YoY growth in DDoS attacks in Q2 2025:
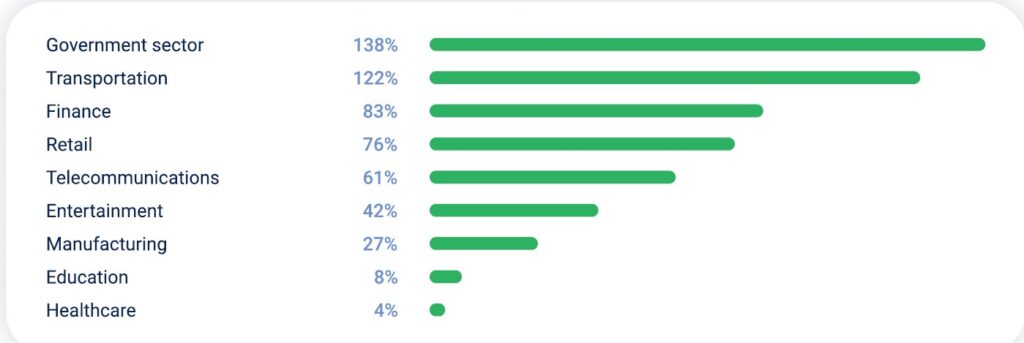
Let’s break down the biggest trends in more detail.
1. Government Sector
Government agencies and critical infrastructure were the top targets for DDoS attacks in Q2 2025, accounting for 31% of all incidents—a 138% year-over-year increase.
As geopolitical tensions escalated—particularly the Russia–Ukraine, Israel–Iran, and India–Pakistan conflicts—hacktivist groups turned DDoS attacks into a weapon of digital warfare. Unsurprisingly, government websites and services were hit hardest.
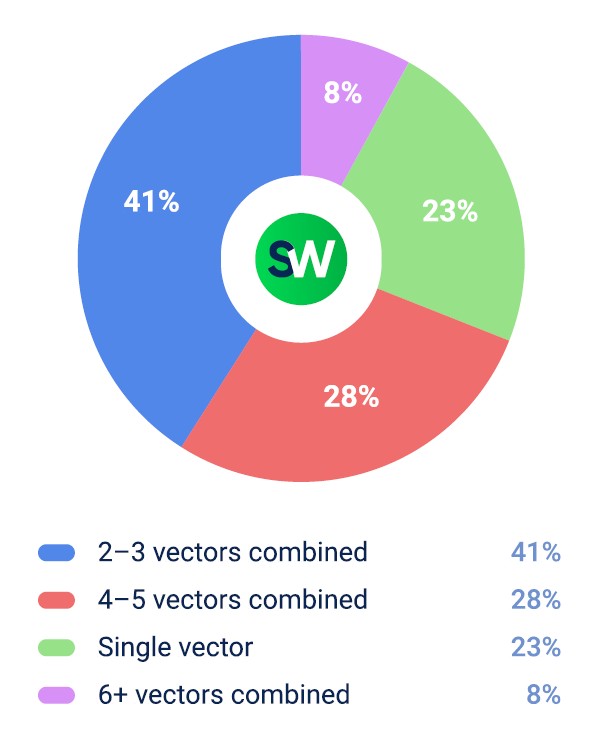
These state-sponsored and politically motivated groups are among the most sophisticated threat actors. As a result, there was a noticeable shift from simple volumetric floods to complex multi-vector campaigns, many of which began with low-volume reconnaissance to map out vulnerabilities.
StormWall analysts observed a 5,000-fold increase in probing DDoS attacks across all sectors. When isolating just the government sector, that number spikes to 8,000x, underscoring the intense focus on public infrastructure.
In Q2 2025, multi-vector DDoS attacks against government entities followed a structured and deliberate approach. The most common pattern looked like this:
- Initial probing: Attackers began by sending low-volume traffic to test DNS infrastructure for weaknesses.
- Application mapping: Next, they scanned government web portals to gather information about exposed services and APIs.
- Main attack phase: Once reconnaissance was complete, they launched highly targeted API-layer attacks designed to disrupt critical operations.
These campaigns typically unfolded in five distinct phases over a period of 48 to 72 hours. This measured pacing allowed attackers to observe how defenses responded at each stage, adjust their tactics in real time, and identify the most vulnerable entry points before executing the full-scale attack.
2. Finance
In Q2 2025, the share of DDoS attacks targeting financial services rose to 18%, up from 8% in Q1. Overall, attack volume in this sector grew by 83% year-over-year.
The primary targets were API endpoints, followed by mobile banking APIs and trading platforms. Unlike traditional volumetric DDoS attacks, API-layer attacks mimic legitimate traffic, making them significantly harder to detect and block.
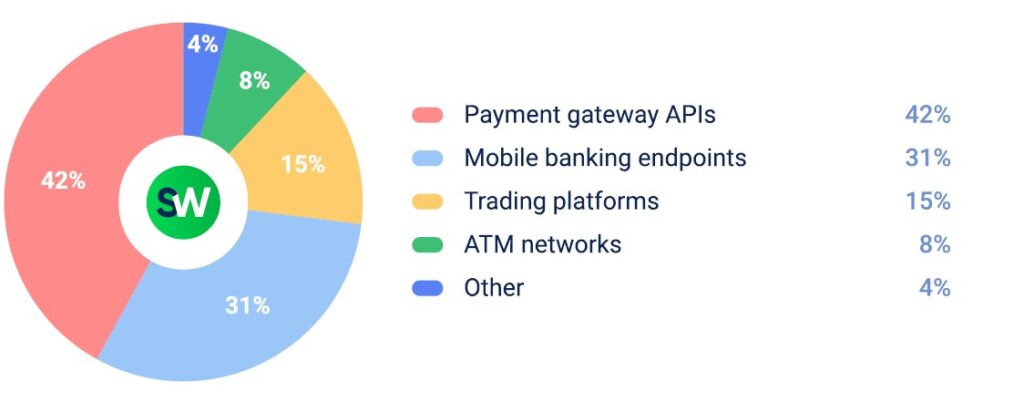
A real-world example occurred on April 21, when attackers targeted Adyen’s payment processing API during peak hours in Europe. The attack disrupted services across several countries. Hackers launched an HTTPS flood disguised as real payment requests, overwhelming backend systems while bypassing standard DDoS protections.
3. Transportation
In Q2 2025, attacks on the transportation sector rose sharply, accounting for 14% of all DDoS incidents—up from 9% in Q1. That’s a 122% year-over-year increase, making it the second-fastest growing targeted industry.
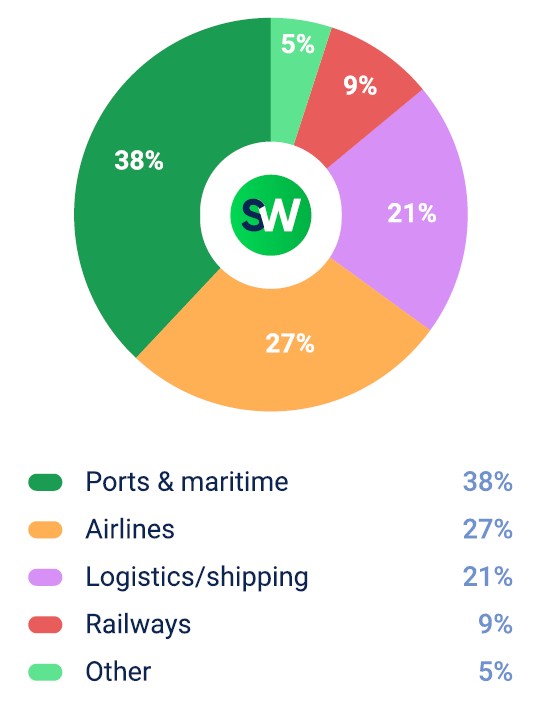
Why transportation? Because disruption here hits hard. When critical systems go down, it affects everything—deliveries stop, flights are grounded, and travel chaos unfolds. That kind of impact makes transportation infrastructure a high-value target for state-sponsored and politically motivated attackers who want to make headlines.
In contrast, attacks on the entertainment industry dropped noticeably in Q2—a clear indication that hacktivists shifted focus toward more disruptive sectors.
What’s changed? Attackers are now leveraging much larger botnets—averaging 120,000–150,000 devices. This expanded capacity means even smaller regional hubs can be hit with the same intensity once reserved for national-level targets.
DDoS Attacks Breakdown by Country
Let’s break down how DDoS attacks were distributed by country in Q2 2025:
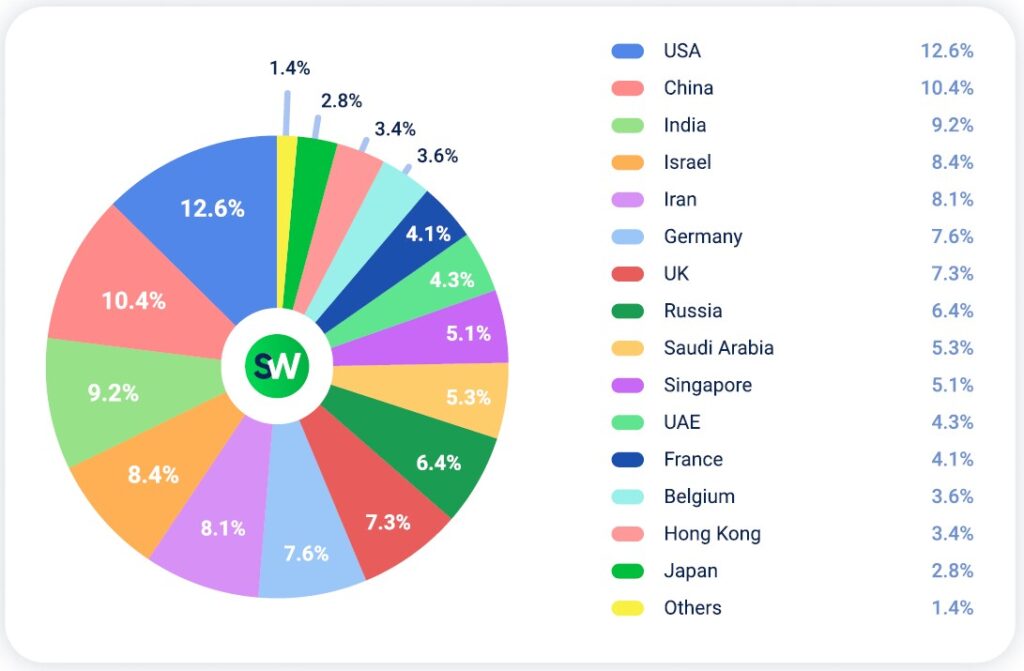
In the second quarter of 2025, DDoS attacks became significantly more geographically dispersed. No single country accounted for more than 12.6% of global attacks, whereas India alone absorbed 18.1% in Q1. This shift indicates that threat actors expanded their target range to include a broader set of countries. Most of this activity was driven by hacktivist campaigns.
Geopolitical tensions heavily influenced which countries were targeted. Both Israel and Iran moved into the top five, with attack shares of 8.4% and 8.1% respectively, reflecting their ongoing regional conflict. Each escalation in diplomatic hostilities triggered waves of attacks against their government and financial infrastructure.
The United States took the top spot, accounting for 12.6% of attacks—a familiar trend. The US, China, and India remain the three most frequently targeted economies, with attack volumes fluctuating between them each quarter depending on the geopolitical climate.
Another notable development this quarter was the rise in attacks on Western Europe. Germany saw a sharp increase, followed by similar campaigns aimed at the UK and France, where threat actors focused on government systems and critical national infrastructure.
Meanwhile, targets in the Asia-Pacific region experienced a significant drop in attack volume. Japan, for example, fell from 12.3% in Q1 to just 2.8% in Q2, and Taiwan dropped out of the top 15 altogether. This indicates a shift in attacker focus away from economic hubs toward active conflict zones.
Singapore was a notable exception. The country absorbed 5.1% of attacks, largely due to its status as a key financial center. As attacks on Western financial institutions ramped up, their Asian branches—including those in Singapore—were increasingly targeted. The same pattern was observed in the UAE and Hong Kong, where financial services and retail platforms drew most of the malicious traffic
Wrapping Up
The most important trend in Q2 2025 is that even non-state actors are now using APT-level tactics—such as multi-vector probing campaigns and massive botnets—as part of their DDoS arsenal.
Just three months ago, many companies could still rely on five-year-old defense technologies. But that’s no longer the case. Outdated protection won’t stand up against either large-scale volumetric floods or sophisticated Layer 7 attacks.
If there’s a weakness in your infrastructure, attackers will find it—and they will exploit it. That’s why it’s critical to prioritize API security and assume that if your systems are being probed, a major attack is likely just around the corner.
In today’s threat landscape, hesitation can be costly. Now is the time to upgrade your defenses, close security gaps, and protect your critical infrastructure before the next wave hits. With the right solutions—like those offered by StormWall—you can face these threats head-on.

DDoS Protection for Websites
- Activate protection in 10 minutes
- 24/7 technical support




















