A DDoS attack is carried out simultaneously from a vast number of devices that attackers have taken control over, gaining the ability to send commands to generate floods of bogus requests. An attack of this kind can cause a denial of service to systems owned by a large enterprise or to an entire network. This article explains in detail how attacks work and how to ensure comprehensive DDoS protection.

DDoS Attacks: Definition, Reasons, Classification
A distributed denial-of-service (DDoS) attack is a malicious attempt to disrupt the normal functioning of a targeted server, service, or network by overwhelming it with a flood of internet traffic from multiple sources. Attackers typically use a network of compromised computers, known as a botnet, to flood the target with an overwhelming amount of traffic, rendering it inaccessible to legitimate users.
The purpose of a DDoS attack is to achieve denial of service for devices connected to the Internet: network equipment and infrastructure, various Internet services, websites and web applications, IoT infrastructure.
How does a DDoS attack work?
The vast majority of attacks develop in the following sequence:
- Collecting data about the victim and further analysis in order to identify obvious and potential vulnerabilities, the choice of the attack method;
- Preparing for an attack by deploying malicious code on computers and Internet-connected devices that have been intercepted;
- Generating a stream of malicious requests from multiple devices controlled by the attacker;
- Analysis of the effectiveness of the attack: if the objectives of the attack were not achieved, the attacker can conduct a more thorough analysis of the data and perform a second search for the methods of attack (go to step 1).
In case of a successful attack, the attacked resource will demonstrate a significant decrease in performance or will not be able to process legitimate requests from users and other services at all. Depending on what exactly the victim resource is, the consequences of a successful DDoS attack can be a sharp drop in performance or inaccessibility of the network, server, Internet service, website, application. As a result, the Internet resource “freezes”, legal users cannot access it at the right time, the network or server becomes temporarily “cut off” from the Internet, the Internet resource stops working correctly, etc.
Read also: Signs of a DDoS Attack (how to check if you’re being DDoSed)
Motivations for DDoS attacks
Attackers may have different motivations. The most common occurrences are unfair competition, attempts at blackmail, conflicts of interest or beliefs, and social or political protest. Revenge attacks, a desire to “practice” the criminal hacking craft, and vanity are also common. However, in recent years, the desire of DDoS attackers to earn extra money has come to the fore. And if the order for an attack is generously paid, it can be quite intense, last for many hours, modified and repeated over and over again.
Further reading: Why DDoS Attacks Happen. Psychology Behind DDoS
Damage from attacks
The damage from a successful DDoS attack primarily lies in financial and reputational costs: lost profits, termination of contracts and loss of users, numerous complaints from customers, a wave of negativity in the media and social networks and, as a result, the decline in popularity of the Internet resource and its owner. Often, a DDoS attack is used as a cover for the main malicious impact in targeted attacks: while cybersecurity specialists focus on DDoS mitigation and system recovery, attackers strengthen the main attack vector – for example, hacking a service, stealing confidential data, or installing malicious codes.
Further reading: Consequences of DDoS Attacks for Business
Companies targeted by DDoS attacks
Attackers can target any company with an online presence, but they are most commonly directed at government, financial institutions, gaming services, and e-commerce companies.
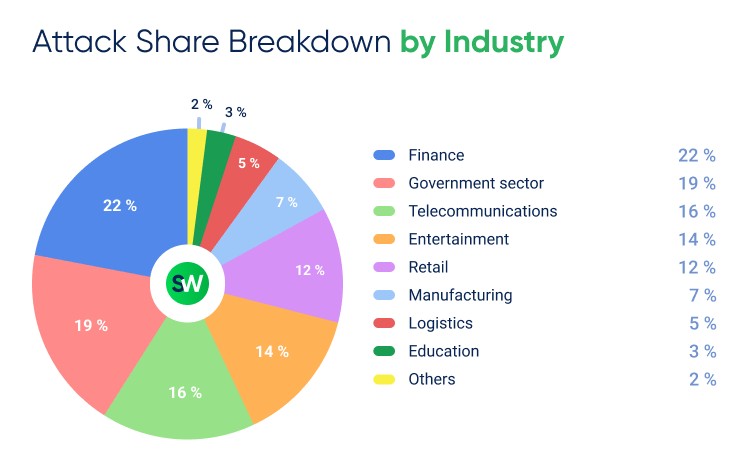
According to our DDoS Attacks Report 2024, government and finance remained the most targeted sectors. The entertainment industry saw the highest growth in attacks, rising from 8% in 2023 to 14% in 2024. Telecommunications followed, increasing from 11% to 16%.
Explore our regular reports on DDoS attacks with statistics for different industries and countries.
DDoS attack classification
The most commonly used method of classifying attacks is by the OSI layer at which they occurred. Let’s list the most common types of DDoS attacks:
- Network layer (L3): DDoS attacks of this layer “work” over IP, DVMRP, ICMP, IGMP, PIM-SM, IPsec, IPX, RIP, DDP, OSPF, OSPF protocols. The targets of attacks are primarily network devices – switches (switches) and routers (routers).
- Transport layer (L4): the impact is made via the TCP and UDP protocols, as well as the DCCP, RUDP, SCTP, UDP Lite subprotocols. The targets of attacks of this level are usually servers and some Internet services, such as gaming.
- Application layer (L7): The attack is carried out at the application protocol layer. Most often, attackers use HTTP, HTTPS and DNS. Attacks of this level target both popular network services and various websites and web applications.
Another common method of classification is by the method of exposure:
- exploitation of protocol vulnerabilities: they allow to achieve denial of service by influencing the attacked resource with incorrect requests, as a result of which the victim “goes into a stupor”, trying to process them;
- traffic overflow with a powerful stream of requests, which the victim is unable to “digest”;
- impact on weaknesses in the architecture and logic of application operation, which can severely disrupt the performance of a software complex connected to the Internet, especially if it has a weak level of security.

StormWall for Web:
DDoS Protection for Web Applications
DDoS Attack Protection
Before taking on the use of means of protection against DDoS attacks, you should take care of increasing the degree of security of the Internet service – its ability to effectively repel attacks with a minimum waste of resources (we call it DDoS protectability). Otherwise, in order to secure the Internet service from influences, you will have to spend a lot of effort and money. Shortly, to increase security you need:
- provide as little information as possible to the attacker;
- provide as much information as possible to the DDoS defender;
- provide clear attack filtering capabilities;
- ensure the reliability of the service under attack.
Learn more: 5 Steps to Prepare for DDoS Attacks
DDoS protectability should be planned at the stage of planning the IT infrastructure and architecture: good design will increase the availability and reduce further costs of protection from attacks.
DDoS protection methods and tools
As for the protection tools, they can be divided:
- by type of solution: deployed locally (on-premise), cloud, hybrid;
- by protection level: packet (at the L3 and L4 levels) or at the application level (L7);
- by connection mode: symmetric or asymmetric filtering.
Learn more: DDoS Protection Tools and Methods
On-premise solutions
On-premise solutions and anti-DDoS tools come in both software and hardware (specialized network devices) and can be installed by both customers themselves and their providers. The main users of local anti-DDoS solutions are large telecom operators (cloud and Internet providers) and data centers that can afford to have their own response service, are able to cope with powerful (hundreds of gigabits) attacks and offer anti-DDoS service to their customers.
Cloud solutions
Cloud solutions implement almost the same security functionality as on-premise solutions. In addition to packet protection, anti-DDoS cloud service providers often offer services to protect sites from attacks made by bots (attackers use the HTTP protocol in them), as well as technical support and support during a DDoS attack. Cloud solutions seem to be the best option for most companies.
Learn more: Cloud-Based DDoS Protection Solutions
Hybrid solutions
A hybrid solution is a set of an on-premise solution and a subscription to an anti-DDoS cloud service that is automatically connected when an attack starts. A hybrid approach removes the attack volume limitations of on-premise solutions and takes advantage of both cloud and on-premise solutions. Hybrid solutions can be recommended for large enterprises with an emphasis on interacting with customers through online channels, as well as small service providers.
Protection from DDoS attacks at L3, L4 and L7 OSI layers
Depending on what kind of Internet resources need to be protected, anti-DDoS tools and services are chosen that have one or another range of protection functions:
- protection against packet flooding based on filtering packets of the transport and network layer (L3 and L4) – this is enough to protect network devices;
- protection against both packet flooding and flooding at the application level (L3 – L7) – this is necessary, in particular, to ensure the operability of sites, since most attacks on them are carried out precisely at the L7 level;
- protection not only against flooding at the L3 – L7 level, but also against “intelligent” DDoS attacks using “smart” bots that attack those parts of web applications that are most resource-intensive when processing incoming requests, using the functions of the Web Application Firewall (WAF) – this is necessary to protect critical Internet resources.
L7 DDoS Protection Guide: How to Stop Application Layer Attacks
Symmetric and asymmetric DDoS filtering
The connection format distinguishes between symmetric and asymmetric DDoS protection. The first option implies installing the filter in a symmetric mode: both incoming and outgoing traffic of the protected server (or service information about this traffic) always passes through the filter. Asymmetric algorithms analyze only incoming traffic. In general, symmetrical protectors are more effective, but the cost of ownership is higher and the signal latency is higher. Asymmetric tools are often more complex, but because they do not analyze outbound traffic, some attacks are not fully filtered in asymmetric mode.
Conclusion
In addition, special care should be taken to ensure that DDoS protection is properly deployed: it is necessary to reduce to zero the number of vulnerabilities that an attacker could exploit.
And of course, you need to pay close attention to the choice of a protection provider, since the real quality of their services, as well as the level of his competence in anti-DDoS matters, can extend over a wide range.
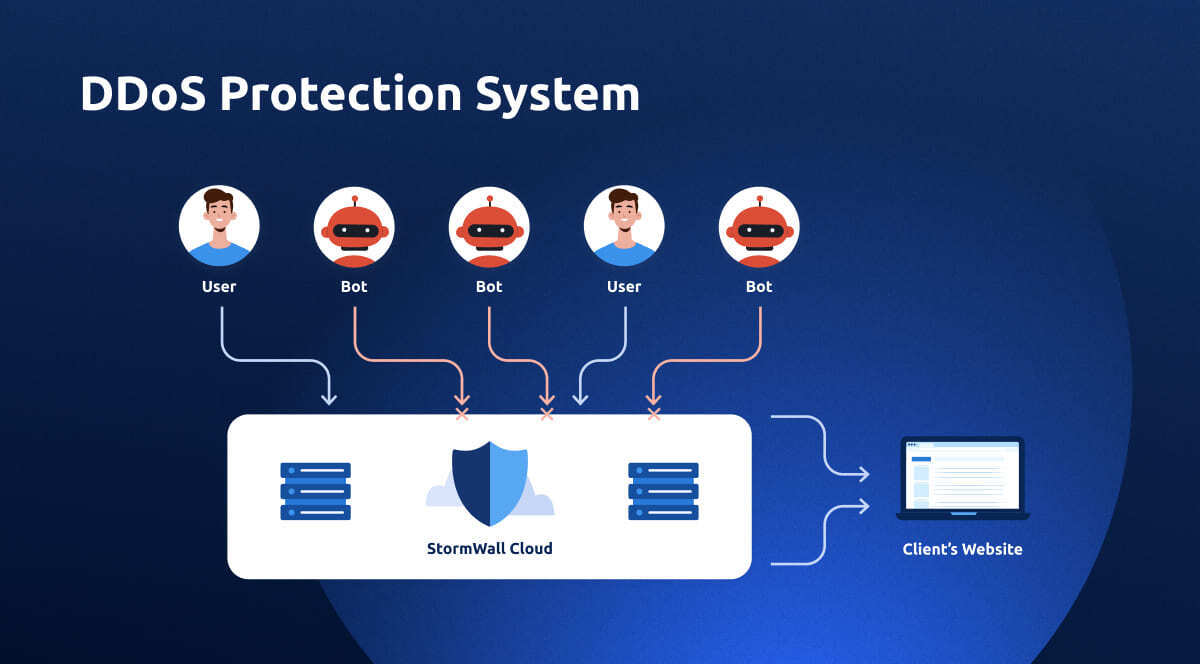
StormWall provides comprehensive protection for projects of all sizes for websites, networks, and IT infrastructures. Leave a request with our managers, and we will provide all the details, as well as an individual approach to organizing protection for your company.

DDoS Protection for Websites
- Activate protection in 10 minutes
- 24/7 technical support




















