StormWall operates scrubbing centers in the United States, Europe, Southeast Asia, and the Middle East, with over 5 Tbps of total filtering capacity. This global infrastructure allows us to handle massive attack traffic every day, giving us a unique view of worldwide DDoS trends.
In the following sections, we’ll explore key attack patterns, their sources, and notable changes observed across APAC during Q2 2025.

The Big Picture
In Q2 2025, DDoS attacks in the Asia-Pacific region surged 137% year over year, with hacktivist activity driving much of this growth. Attacks linked to known hacktivist groups rose 93%, spiking over 356% in India and Pakistan following the onset of regional conflict.
Financial services, entertainment platforms, and retail businesses were among the hardest-hit industries. API-based attacks over HTTP/HTTPS grew by 86% year over year, highlighting attackers’ focus on disrupting modern web services.
We also observed a staggering 5,000x increase in short probing attacks lasting up to 15 minutes. These reconnaissance attacks are designed to identify vulnerabilities and test defenses before launching larger campaigns.
Let’s break down these trends in more detail:
DDoS Attacks Up 137% Year-over-Year
In Q2 2025, StormWall mitigated 3.5 million DDoS attacks across the APAC region—a 137% increase compared to the previous year. Around 60% of these attacks were carried out by hacktivist groups, reflecting the surge in politically motivated activity in the region.
Among the incidents, 30 were hyper-volumetric floods exceeding 800 Gbps, capable of crippling unprotected infrastructure in seconds.
API Attacks Up 86%
In Q2 2025, API-targeted DDoS attacks surged by 86%, becoming one of the most challenging threats to mitigate due to their ability to mimic legitimate traffic.
StormWall observed that over 80% of these attacks were launched via botnets, with the average botnet size reaching 120,000 devices—a 60% increase since Q1 2025.
Unlike traditional volumetric floods, smaller, targeted API attacks can take down a service with just 10% of the traffic volume required for a generic DDoS campaign, making them both stealthy and highly disruptive.
Probing Attacks Surge Massively
In Q2 2025, probing attacks skyrocketed 5,000x, marking an unprecedented surge in reconnaissance activity. These attacks are designed to scan networks for open ports, services, and vulnerabilities, allowing adversaries to prepare for more damaging follow-up attacks.
What is probing? Probing involves sending short bursts of traffic to identify vulnerabilities in a network. It’s commonly used by APTs (Advanced Persistent Threats) during the reconnaissance phase, but its widespread deployment this quarter signals a shift toward more organized and strategic DDoS campaigns.
Key insights from Q2 2025 probing campaigns:
- Duration: Most lasted under 15 minutes, averaging 2.8 minutes.
- Traffic volume: Each probe generated ~1.2 KB of traffic per target.
- Speed: A single port could be scanned in just 0.5 seconds.
This massive spike in probing means attackers are mapping networks faster and more efficiently than ever, increasing the risk of highly targeted, multi-vector DDoS attacks.
Industry Breakdown
Let’s take a closer look at how DDoS attacks were distributed across different sectors in APAC during Q2 2025:
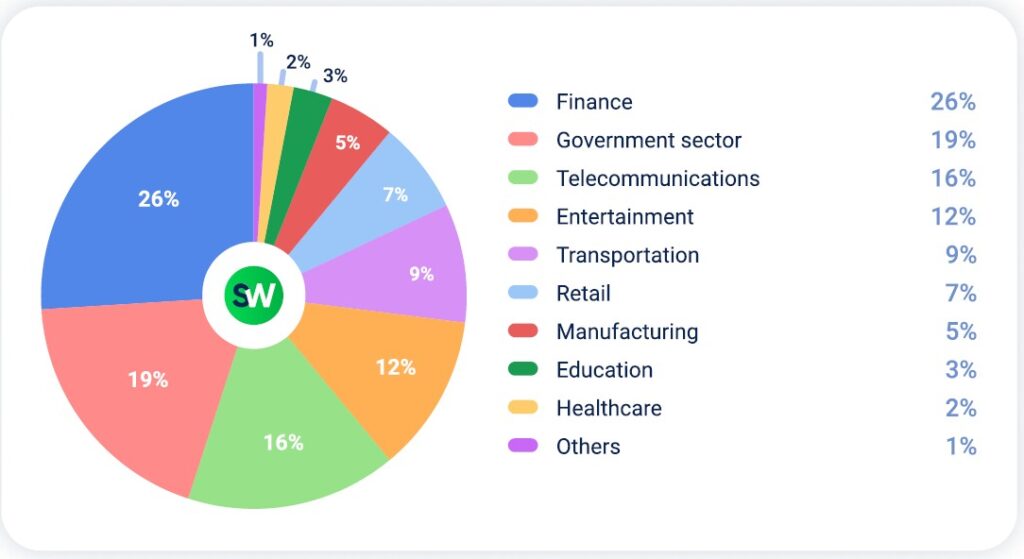
Industries with the highest YoY growth in DDoS attacks in APAC in Q2 2025:
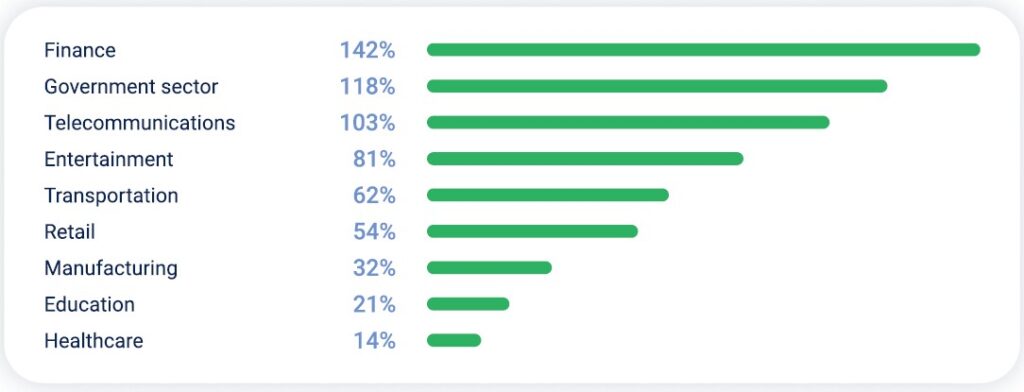
Four industries experienced over a twofold year-over-year increase in DDoS attacks. Attack distribution was heavily concentrated in the top three sectors, with a steep drop-off in other industries. Here are other trends worth highlighting:
- In Q2 2025, the finance sector was the most targeted industry for DDoS attacks in APAC, more than tripling its share from 8% to 26% compared to the previous quarter.
- Attacks on the government sector increased by 58% quarter-over-quarter and by 118% year-over-year.
- Telecommunications fell from first to third place, with its attack share nearly halving from 31% to 16%. Despite this decline, the sector still recorded 103% year-over-year growth.
- Entertainment attacks decreased by 33% quarter-over-quarter, dropping from 18% to 12% of total attacks. However, year-over-year growth was 81%.
- The share of attacks on the transportation industry is stable at 9% of attacks, down slightly from 10% in Q1.
- Attacks on manufacturing and retail business increased marginally from 4% to 5% and 6% to 7% respectively.
The share of DDoS attacks on healthcare and education verticals remains in the 2-3% range, which has been a persistent baseline for several quarters.
Who Is at Most Risk for a DDoS Attack?
Which industries are most and least likely to be targeted by DDoS attacks? The table below shows the relative risk by sector:
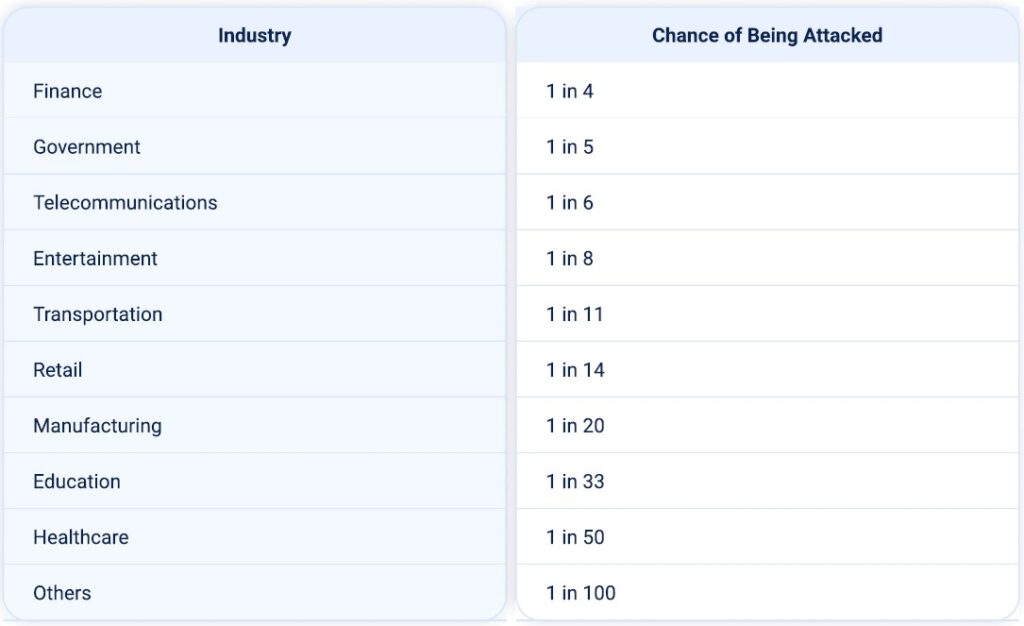
Note: These figures reflect the relative risk within the APAC region based on the observed distribution of attacks. Actual risk exposure depends on multiple factors, including attack surface, security posture, and threat actor interest.
Under a Magnifying Glass: Top 3 Most Attacked Verticals
Finance

Financial services were the top target for DDoS attacks in Q2 2025, with roughly 72% of incidents aimed at payment gateways. Attackers primarily focused on API endpoints, disrupting transaction processing and authentication services.
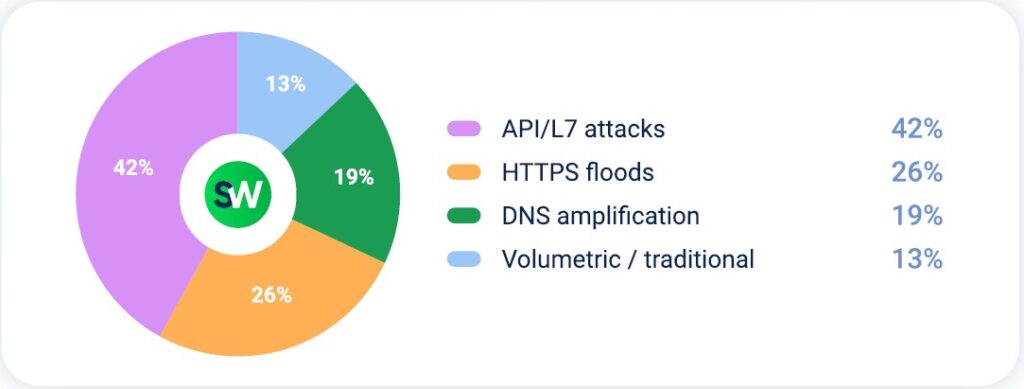
The largest attack against the financial sector in Q2 2025 peaked at 1.2 Tbps, targeting a client in Singapore. The longest campaign sustained roughly 350 Gbps for eight days, while the average attack lasted just 10 minutes, highlighting the rapid and volatile nature of modern DDoS campaigns.
Government Sector

Government infrastructure remained the second most targeted vertical. Attacks focused on public-facing services:
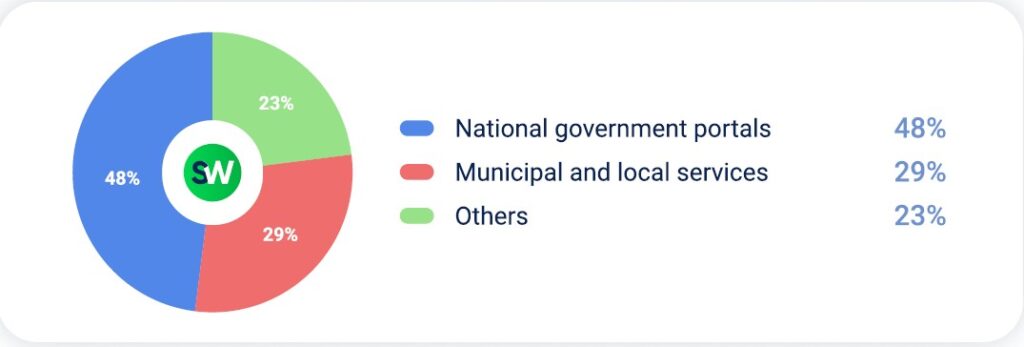
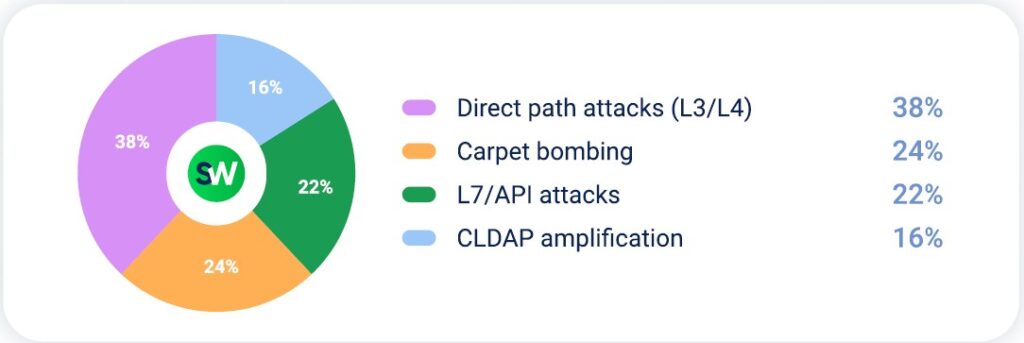
Direct path attacks were the most common method, often combined with newer amplification techniques:
Telecommunications

In Q1 2025, telecom operators were the most attacked group. In Q2, this vertical dropped to third place but continued to face significant attack volumes. Within the telecommunications sector, mobile network operators were targeted the most, followed by ISPs.
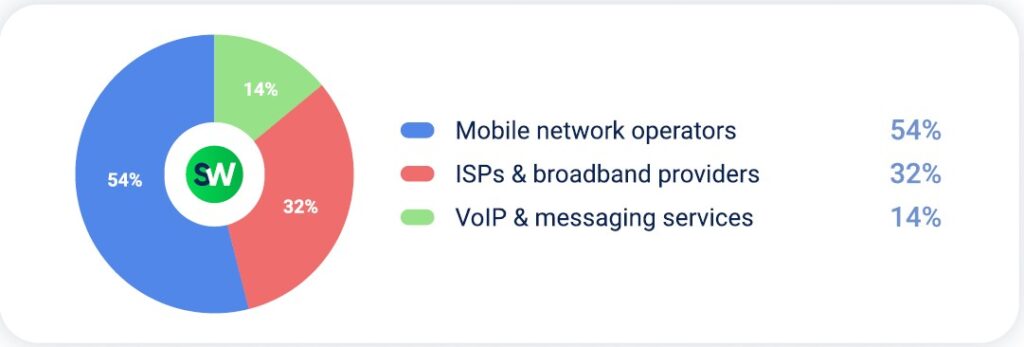
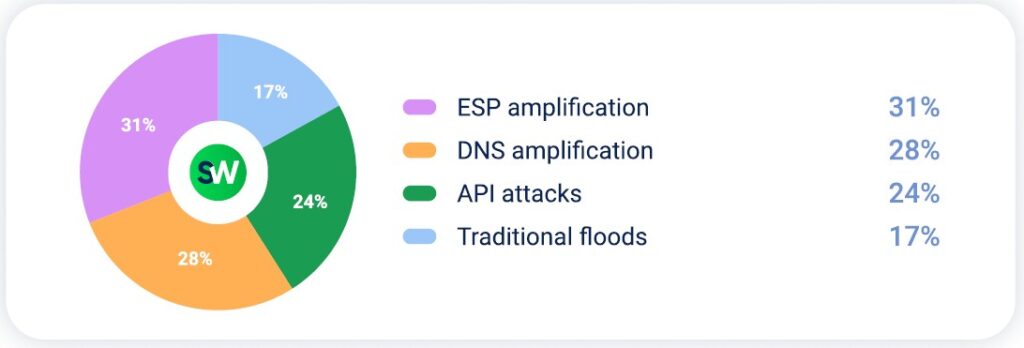
ESP amplification was the most common attack vector against telecom infrastructure:
DDoS Attacks by Country
Let’s break down how DDoS attacks were distributed by country in Q2 2025:
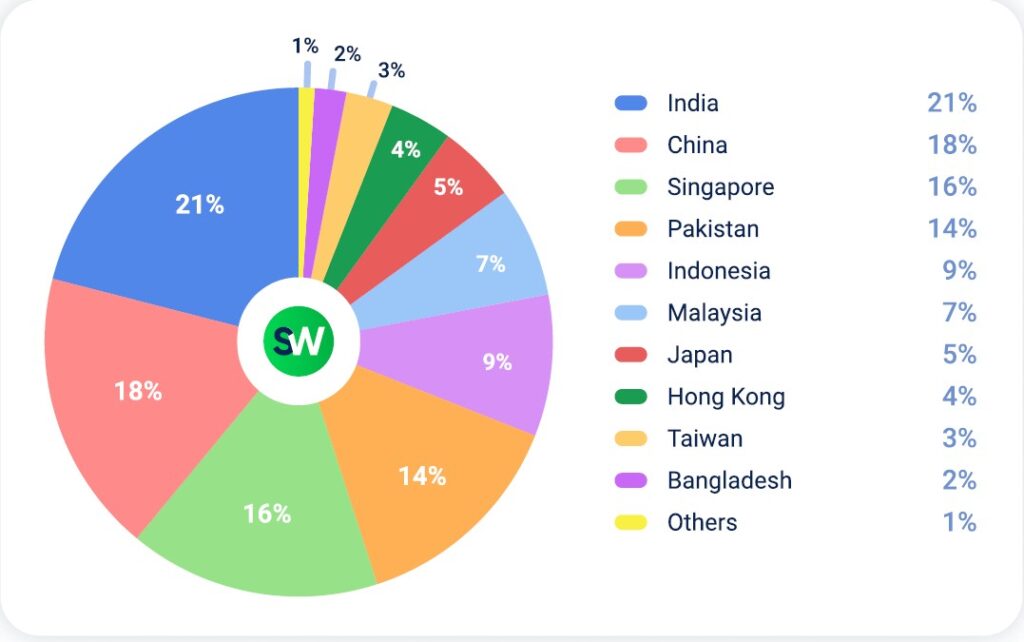
When comparing Q2 2025 to the first quarter, India reclaimed the top spot among DDoS targets in APAC, with its share rising from 18% to 21%. China fell to second place, dropping from 22% to 18%, while Pakistan emerged as a major target, jumping to 14% from minimal activity in Q1. In contrast, Taiwan saw a steep decline, falling from 14% to just 3% of all attacks.
Other notable shifts include:
- Singapore’s attack share rose from 12% to 16%
- Indonesia saw a rise from 5% to 9%
- Japan’s share of DDoS incidents declined from 9% to 5%
- Attacks on Hong Kong dropped from 6% to 4%
South Korea dropped out of the top 10, while DDoS activity targeting Malaysia and Bangladesh held steady at 7% and 2%, respectively.
Quick Highlights
- DDoS activity across the Asia-Pacific region surged 137% year-over-year in Q2 2025. Finance, government, and telecom were the top three targeted sectors, with finance alone jumping from 8% to 26% of all attacks.
- API-layer attacks grew 86% YoY, and probing campaigns exploded by 5,000x, typically lasting under 15 minutes and generating just 1.2 KB per target. Botnets also became larger and more sophisticated, averaging 120,000 devices—a 60% increase over the previous quarter.
- By geography, India (21%), China (18%), and Singapore (16%) led the region in attack volume. Pakistan (14%) emerged as a major new target, while Taiwan dropped sharply from 14% to 3%.
- Traditional volumetric floods are declining, replaced by multi-vector campaigns and stealthy API or probing attacks. Building strong DDoS defenses now requires API-layer protection and proactive detection of low-volume threats.
- Hacktivist groups drove 60% of the 3.5 million attacks mitigated by StormWall in APAC. With attack methods evolving rapidly, organizations should review and update their DDoS protection quarterly to stay ahead of emerging threats.
The number of DDoS attacks in the APAC region continues to grow, and the attacks themselves are becoming increasingly sophisticated. To help you stay aware of these threats and respond quickly, we closely monitor developments both regionally and globally. Follow our blog to stay updated—we’ll keep you informed.

DDoS Protection for Websites
- Activate protection in 10 minutes
- 24/7 technical support




















