Our analysts continue to monitor the DDoS situation across Asia and share key trends in our regular reports. This is our Q1 2025 overview, where we highlight the most targeted industries, emerging techniques used by cybercriminals, and top insights based on data from our global scrubbing centers.

Key Trends
In Q1 2025, two previously observed DDoS trends intensified across Asia. Let’s take a closer look.
Carpet Bombing Attacks Rose by 96%
This trend accelerated in late 2024, with multi-destination attacks accounting for 30% of mitigated incidents—double the share recorded just two years earlier.
Carpet bombing campaigns often combine multiple vectors, hitting large IP ranges and prefixes with different types of floods (UDP, TCP, HTTP, etc.) in rapid succession—a method known as the “everything, everywhere, all at once” approach.
Breakdown of Flood Types in Carpet Bombing Attacks in APAC, Q1 2025:

It’s important to note that carpet bombing attacks keep traffic volume per IP below conventional DDoS thresholds, making them highly stealthy. Legacy defenses designed for single-destination floods often fail to detect these attacks until critical infrastructure (routers, firewalls) collapses.
API Attacks Surged by 74%
StormWall data showed that L7 web DDoS attacks grew by 95% in Q1 2025, while API-targeted incidents rose by nearly three-quarters year over year. Many of these attacks in APAC were aimed at banks and critical infrastructure.
API DDoS attacks mimic legitimate requests, making them difficult to detect or stop using rate limits or IP filtering. Attackers often target resource-intensive endpoints—like authentication or search—to overload CPU or memory on backend servers, potentially causing the entire application to crash.
Most Targeted Industries
Now, let’s break down the distribution of DDoS attacks by verticals in APAC in Q1 2025:
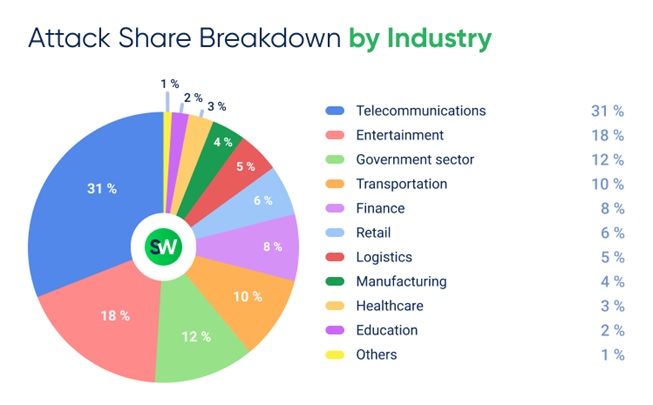
Attacks by Industry: Who’s at Risk?
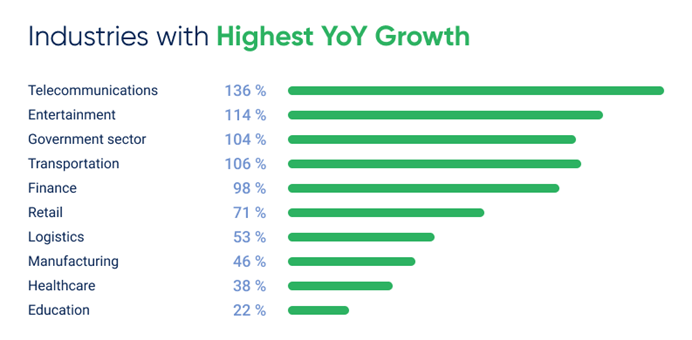
Five industries saw a twofold—or nearly twofold—increase in DDoS attacks year over year. Interestingly, attack share drops by roughly half as you move down from the most targeted sectors.
Here are the key trends:
- Telecommunications became the top target in APAC in Q1 2025, with 136% YoY growth. Attack volume nearly doubled quarter-over-quarter, rising from 16% to 31% of all incidents.
- Entertainment: Up 29% from the previous quarter and +114% year-over-year.
- Government sector: Rose 71% QoQ, moving into third place in attack volume. Compared to Q1 2024, the number of attacks here increased by 104%.
- Transportation: Saw a 67% QoQ rise and doubled its YoY growth to 106%.
Unexpected Shifts:
- Finance, previously the most attacked sector, dropped from 31% to 8% quarter-over-quarter, falling to fifth place despite a YoY increase of +98%.
- Retail: Attack volume halved (from 12% in Q4 2024 to 6%), though annual growth remained high at +71%.
Infrequent Targets:
- Healthcare and education consistently account for just 2–3% of all DDoS attacks. Unless attacker motivations shift significantly, these sectors are unlikely to drop below that baseline.
Drivers Behind the Trend
Telecom and government sectors represent critical infrastructure, where DDoS attacks are especially disruptive.
The surge in attacks on entertainment and transportation may be seasonal—linked to holiday activity and increased demand for services.
The sharp drop in attacks on the financial sector warrants further analysis. It’s possible that organizations have significantly strengthened their defenses, or that attackers have shifted their focus to other sectors.
Relative Risk of DDoS Attacks
Which industries are most likely to be targeted by DDoS attacks—and which are relatively safer? The table below outlines the risk levels by sector:
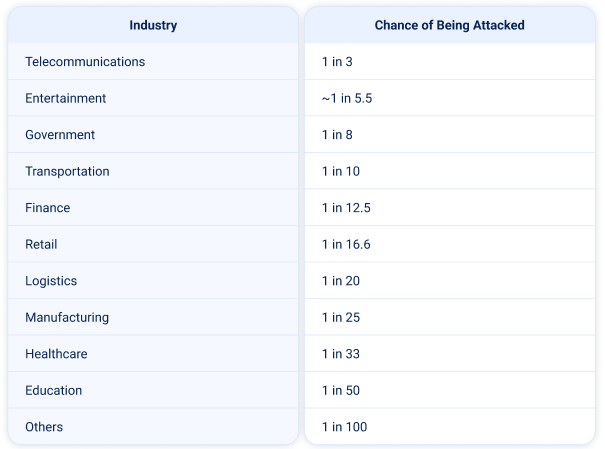
Note: this is a relative risk within the APAC region and only based on the observed distribution of attacks. Real-world risk also depends on exposure surface, security posture and threat actor interest.
Top 3 Most Attacked Verticals
Telecommunications

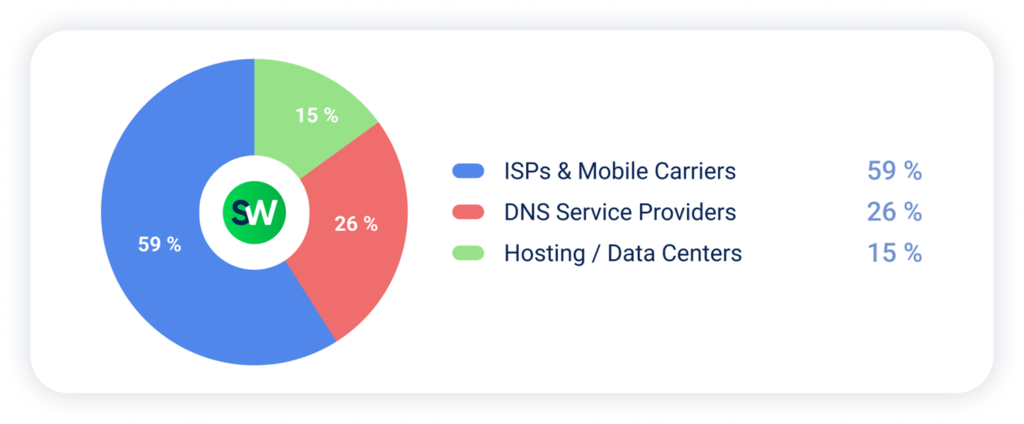
Telecom networks and DNS servers faced a surge of carpet bombing DDoS attacks, with the majority of incidents aimed at ISPs and mobile carriers:
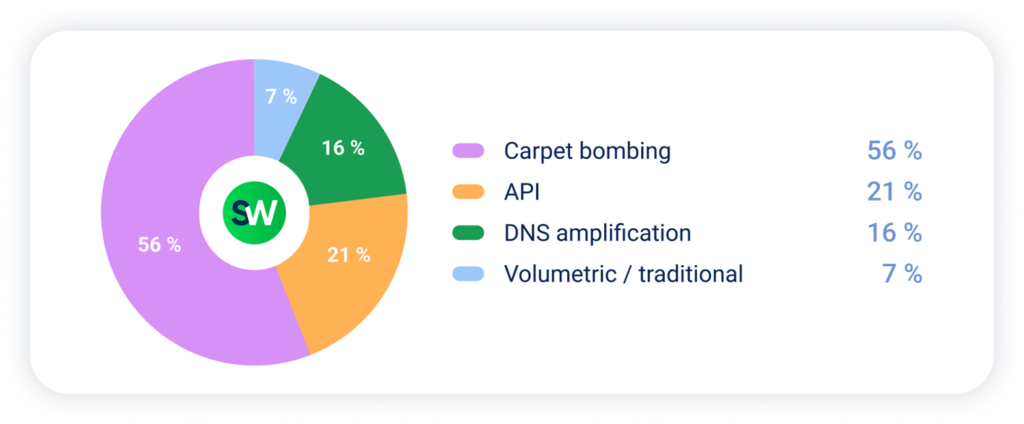
Alongside carpet bombing, L7/API attacks were widespread, followed by DNS amplification. Traditional volumetric attacks—being the least sophisticated—were also the least common:
The largest DDoS attack in Q1 2025 mitigated by StormWall peaked at 2.3 Tbps and targeted a data center provider in China. The longest-running attack was also telecom-related—it lasted 11 consecutive days at around 850 Gbps, hitting a telecom service in Taiwan.
The largest DDoS attack in Q1 2025 mitigated by StormWall peaked at 2.3 Tbps and targeted a data center provider in China. The longest-running attack was also telecom-related—it lasted 11 consecutive days at around 850 Gbps, hitting a telecom service in Taiwan.
Entertainment
Entertainment targets include online multiplayer games, esports platforms, video streaming services, and media broadcasters.

These platforms face DDoS attacks for several reasons. Some attackers—especially younger hackers or users of DDoS-for-hire services—see taking down gaming servers as a way to gain notoriety or simply as an act of digital vandalism. In other cases, attacks are driven by competitive sabotage, where rivals attempt to knock competing players or platforms offline.
Gaming is a massive industry in Asia—China’s gaming market alone exceeds $60 billion—making it an appealing target for extortion. Attackers sometimes threaten to launch DDoS attacks on popular games unless a ransom is paid. Gaming-related sites and infrastructure in China, India, and Korea have been especially frequent targets.
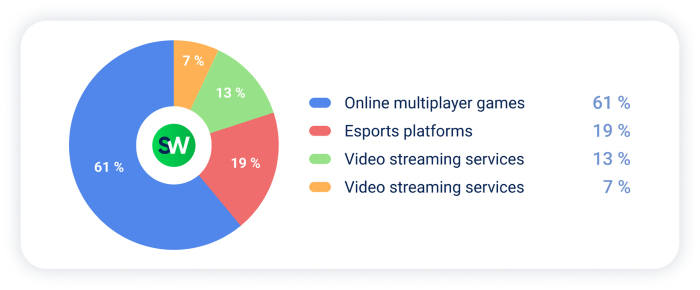
Most of these attacks were aimed directly at gaming infrastructure:
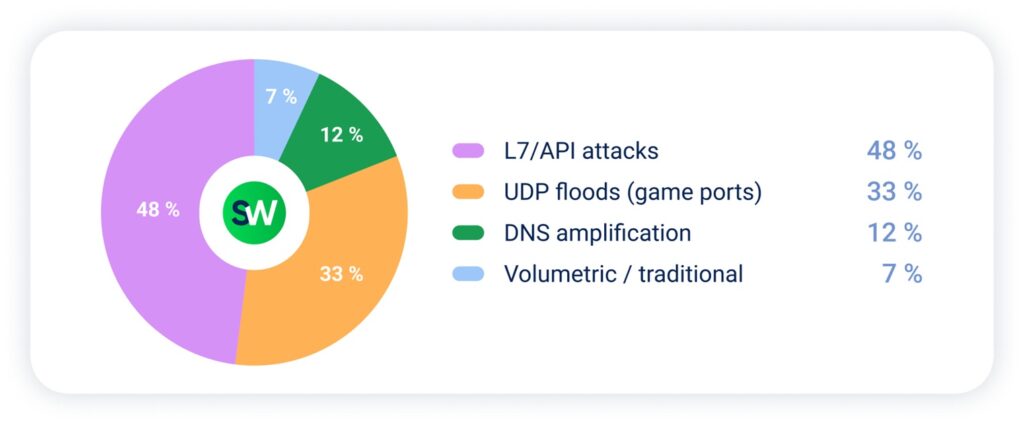
Attack techniques in this sector often target latency-sensitive environments, as the goal is to make the gaming experience worse:
Government Sector

In Q1 2025, multiple large-scale DDoS campaigns targeted government infrastructure across APAC. Notably:
- Taiwan: Chinese nationalist hacktivists launched DDoS attacks targeting government offices. These attacks were short but highly intense, averaging 600–900 Gbps in bursts lasting 1–2 hours.
- India–Pakistan: Regional hacktivist groups engaged in tit-for-tat DDoS activity, mostly small-scale floods (50–100 Gbps) targeting government portals and regional infrastructure, often timed with political events.
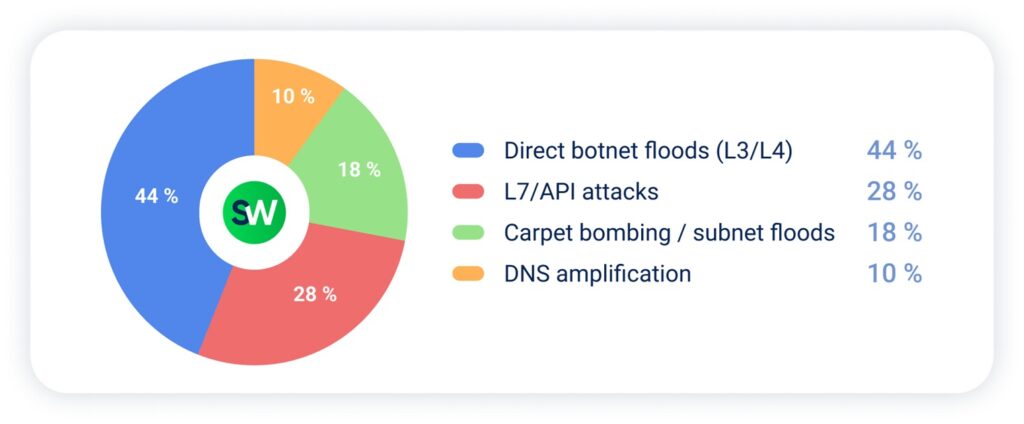
Direct botnet floods were the most popular attack method, sometimes combined with L7 attacks aimed at public APIs and login portals:
DDoS Attacks by Country
Let’s break down how DDoS attacks were distributed across APAC region in Q1 2025:
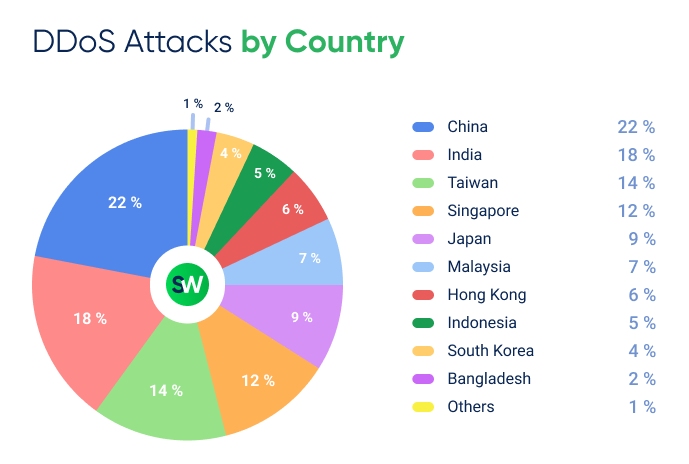
Compared to Q4 2024, China emerged as the most targeted country in the APAC region in Q1 2025, with its share of attacks rising from 18% to 22%. Meanwhile, India experienced a slight decline, dropping from 21% to 18%.
Taiwan, despite its small size, faced an unprecedented surge in DDoS attacks—its share jumped from 2% to 14% quarter-over-quarter. This spike was largely driven by coordinated campaigns from Chinese hacktivist groups.
Other notable changes between Q4 2024 and Q1 2025 include:
- Singapore: dropped from 16% to 12%
- Japan: 7% → 9%
- Malaysia: 3% → 7%
- Hong Kong: 9% → 6%
- Indonesia: 12% → 5%
South Korea, Bangladesh, and other smaller markets remained relatively stable, with minor changes in attack share compared to the previous quarter.
Key Takeaways from Our Report
Attack tactics are becoming more sophisticated. API floods and carpet bombing are growing faster than traditional volumetric TCP/UDP attacks, pushing companies to adopt smarter, more flexible defenses.
At the same time, rising geopolitical tensions are driving a surge in attacks on government systems and Taiwan—highlighting increased activity from hacktivists and state-sponsored threat actors.
Legacy protections like rate-limiting are no longer enough. Modern threats call for behavioral traffic analysis and security at the application level.
Organizations across APAC need to quickly evolve their cybersecurity strategies. This requires combining robust network-layer defenses with deep packet inspection, alongside AI-driven analysis of API traffic, to stay ahead of emerging DDoS threats.

DDoS Protection for Websites
- Activate protection in 10 minutes
- 24/7 technical support




















