StormWall continues to closely monitor the evolving cybersecurity landscape globally—and we’re pleased to share the latest insights from our analytics center.
This time, we present the key DDoS trends observed in the first quarter of 2025. Enjoy the read!
Key Highlights
By early 2025, the number of DDoS attacks had reached unprecedented levels. Let’s take a closer look at the data and what’s driving this surge.
API Attacks
In Q1 2025, there was a sharp increase in Layer 7 DDoS attacks. According to our data, the number of application-level (L7 OSI) incidents globally rose by 74% YoY. In most cases, attackers flooded APIs with large volumes of seemingly legitimate HTTP/HTTPS requests, aiming to disrupt them.
Read more: L7 DDoS Protection Guide: How to Stop Application Layer Attacks
Many of these attacks were powered by large botnets, responsible for about 70% of all HTTP flood incidents. Attackers also increasingly use evasion techniques—such as emulating legitimate browsers or interspersing valid requests—to bypass basic filters.
Botnets
Botnets continue to grow in scale, largely due to vulnerabilities in IoT devices. A clear example is Eleven11, which made headlines in Q1 2025. It consists of over 86,000 compromised IP cameras and DVRs. These devices are capable of generating malicious traffic at volumes reaching hundreds of millions of packets per second (PPS).
Notably, 96% of the devices in Eleven11 do not spoof their IP addresses. This means the botnet relies on direct, non-amplified traffic from real infected devices—making it harder to detect and block.
Read also: What Are Botnets and How Are They Used in DDoS Attacks?
DNS Attacks
DNS Amplification and DNS Water Torture remain two of the most widespread DDoS techniques targeting DNS services. The number of such attacks increased by 90% year-over-year in Q1 2025.
Water Torture attacks are showing especially rapid growth. They work by flooding a target’s DNS server with a massive number of requests containing random subdomain prefixes. This prevents effective caching, as each query is treated as new. As a result, the DNS server becomes overloaded and unavailable to legitimate users. Over the past three years, the volume of such queries has surged by around 500%, putting immense strain on targeted DNS infrastructures.
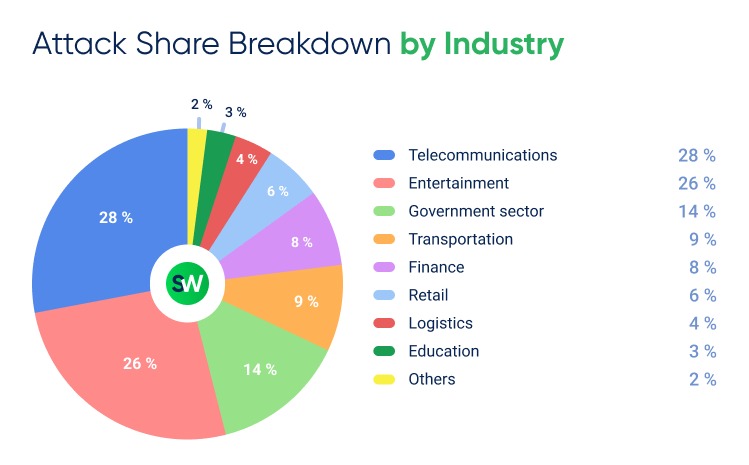
Top Industries by Number of DDoS Attacks
Key industry-specific developments:
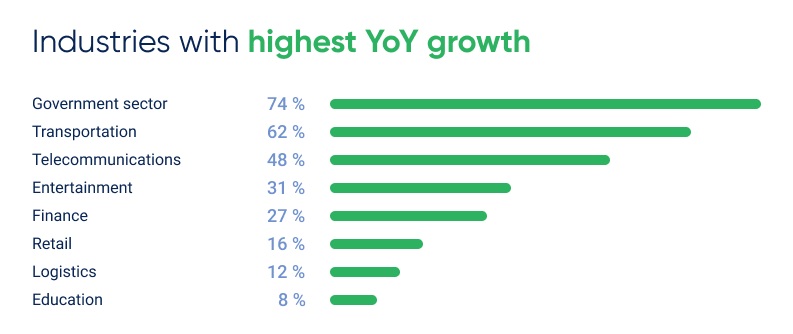
- The telecommunications sector faced the highest number of attacks, accounting for 28% of all global DDoS traffic. Compared to the same period in 2024, the number of incidents in this sector increased by 48%.
- In second place globally is the entertainment industry, with 26% of all attacks, followed by the government sector at 14%. The significant number of incidents affecting public sector organizations is largely due to a series of politically motivated cyberattacks. In particular, government websites in Spain, the UK, and Belgium were targeted in Q1 2025. Additionally, there was a noticeable rise in attacks on Georgian government web services ahead of the vote on the controversial “foreign agent” law.
- The finance sector saw a sharp drop in DDoS activity—falling from 28% of all attacks in Q4 2024 to just 8% in Q1 2025.
- Meanwhile, the transportation sector continued its upward trend. It accounted for 9% of global DDoS attacks in Q1 2025, with the total number of incidents rising 62% year-over-year. The increase is linked to the rapid digitalization of logistics and supply chain processes, along with a high number of vulnerabilities in sector-specific systems.
Which Countries Were Targeted Most Frequently?
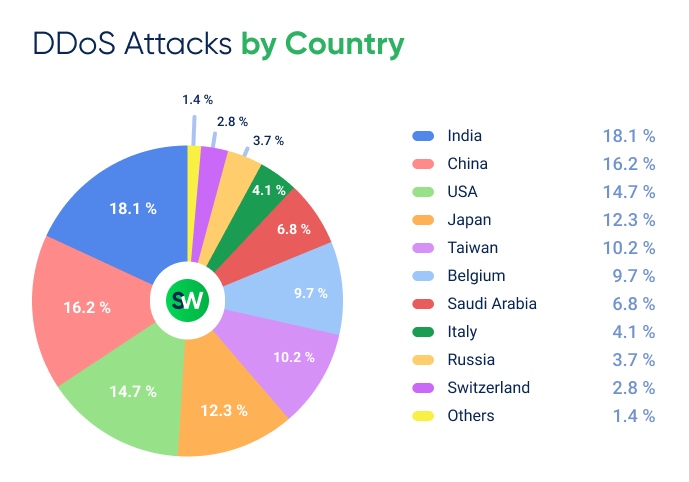
- The Asia-Pacific (APAC) region now dominates the global DDoS map. Notably, India, China, Japan, and Taiwan ranked among the top five most targeted countries this quarter. Taiwan faced an average of 2.5 million cyberattacks per day, with at least 46 Japanese organizations—including major banks and public institutions—affected by targeted attacks. Many of these attacks coincided with regional elections and other political events across APAC.
- Belgium stands out as well. Previously, its share of attacks was so small that it didn’t make it into our rankings. However, in Q1 2025, Belgium was hit by 9.7% of all global DDoS attacks. This sudden spike is linked to targeted campaigns against major websites including MyGov.be and the Walloon Parliament.
- In the Middle East, hacktivist groups became more active. In Q1 2025, government and financial websites in Israel were subjected to massive DDoS attacks by pro-Palestinian actors. International platforms were affected too—most notably the social network X (formerly Twitter), which was taken offline for several hours in March due to a powerful DDoS campaign. A pro-Palestinian group claimed responsibility for the incident.
One Conclusion: Be Prepared
What can we learn from the current state of the cyber threat landscape? If you’re part of a SOC team, the key recommendation is to take a broader view of DDoS attacks—reinforce your defenses at both the DNS and application (L7) layers.
For business leaders, there’s one especially important takeaway: the tools and tactics once used in large-scale politically motivated DDoS campaigns are now accessible to a much wider range of attackers. It’s critical that your DDoS protection solution is capable of countering such threats—not tomorrow, but starting today.

DDoS Protection for Websites
- Activate protection in 10 minutes
- 24/7 technical support




















