This report provides an analysis of DDoS attacks against our clients during H1 2025, focusing on the attack patterns, sources, and evolving trends we observed.

The Big Picture
In the first half of 2025, DDoS attacks in the APAC region surged by 116% compared to the same period in 2024.
A major driver of this growth was a sharp rise in hacktivist activity. Many attacks were linked to well-known hacktivist groups involved in conflicts between India and Pakistan. Others were retaliatory strikes triggered by closer diplomatic ties between Russia and China, as well as escalating tensions between China and Taiwan.
Attacks using botnets rose by 74%, with the average size of a botnet quadrupling—meaning attackers now have four times more power at their disposal than a year ago.
Even more striking was a 3,500-fold increase in probing attacks—a reconnaissance tactic where hackers scan networks for vulnerabilities before launching a full-scale DDoS assault.
The most frequently targeted industries were:
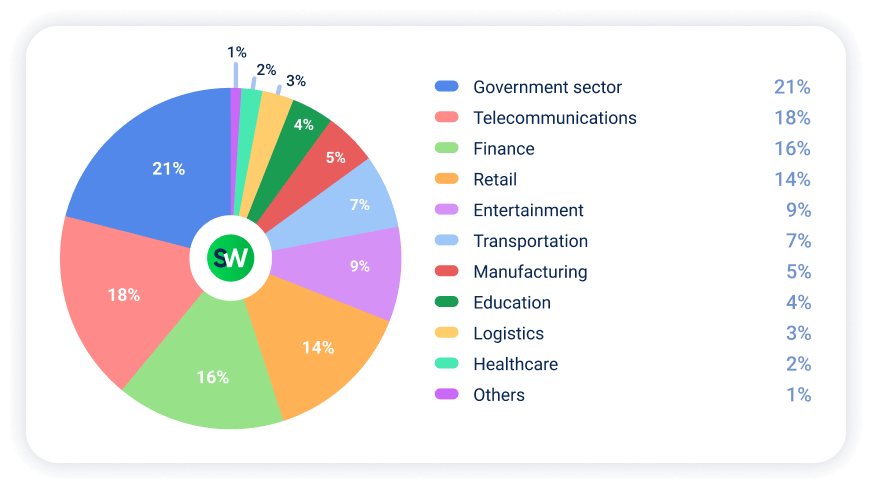
- Government (21%)
- Finance (18%)
- Telecommunications (16%)
Finally, API-targeted attacks also spiked, with a 63% increase compared to the same timeframe last year.
Let’s cover some of these trends in more detail:
The Majority of Attacks Now Tied to Hacktivism
Just a few years ago, most DDoS attacks were financially motivated—essentially attempts to extort businesses. But in 2025, the landscape has shifted dramatically. Today, most attacks are carried out by hackers driven by political agendas or backed by entities with geopolitical interests.
While this shift is a simplification of a complex trend, the practical impact is significant. It changes both the nature of the attacks and the targets our clients are defending.
In the Asia-Pacific region, many attacks are tied to rising tensions between countries—notably between China and Taiwan, India and Pakistan, and Russia and Japan. As a result, much of the world’s malicious internet traffic originates from or is directed toward these regions.
Probing Attacks Up 3,500×
In the first half of 2025, probing attacks—the reconnaissance phase of many DDoS campaigns—surged by 3,500 times compared to the previous year.
These attacks are designed to scan networks for open ports, active services, and vulnerabilities—essentially mapping out the weakest points before launching a full-scale strike.
Key facts about probing activity:
- Most probes lasted under 15 minutes, with an average duration of just 2.8 minutes
- On average, each probe generated only 1.2 KB of traffic per target
- It took as little as 0.5 seconds to scan a single port
API Attacks Up 63% in H1 2025
Attacks targeting APIs surged by 63% in the first half of 2025. These attacks are particularly dangerous because they often mimic legitimate user behavior, making them harder to detect and stop.
Key insights:
- 80% of API attacks were launched using botnets
- 55% lasted less than 15 minutes, making them short but impactful
- Despite being highly effective, L7 (application-layer) attacks used around 70% less traffic than attacks on other OSI layers
How to Protect Your API from DDoS Attacks
Attacks by Industry
Now, let’s break down the distribution of DDoS attacks by industry in APAC in H1 2025:
Industries with highest YoY growth in DDoS attacks in APAC in H1 2025:
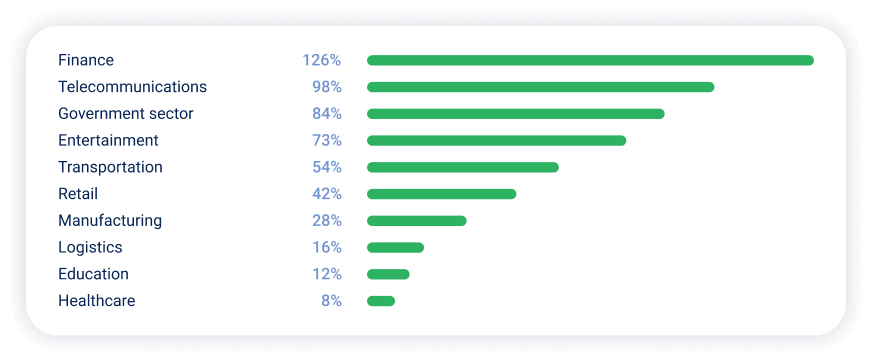
In the first half of 2025, finance and telecommunications saw the largest year-over-year increases in DDoS attacks. While the government sector remained the top target overall, its lead has narrowed (21% vs. 28% last year).
Key trends to know:
- Retail nearly doubled its share of attacks, rising from 8% to 14%.
- Telecommunications increased from 15% to 18%, moving from fourth to second place.
- Government sector remained the top target, though its share decreased from 28% to 21%.
- Entertainment dropped significantly, from 17% to 9%.
- Transportation attacks decreased from 11% to 7%.
- Manufacturing remained steady at 5%.
Who Is at Most Risk for a DDoS Attack?
What vertical is most likely to be attacked and what vertical is least likely to be attacked? The table below shows the relative likelihood by sector:

Under the Magnifying Glass: Top 3 Most Attacked Verticals
1. Government Sector
While the government sector remained a top target, its share of DDoS attacks dropped from 28% to 21% in H1 2025 compared to the same period in 2024. This shift is mainly due to faster growth in attacks across other industries.
Still, several high-profile government-related attacks took place, particularly across Asia:
- Taiwan: Pro-China nationalist hackers launched intense DDoS waves against government institutions. These attacks averaged 600–900 Gbps and lasted for 1–2 hours, flooding systems in short, high-impact bursts.
- Japan: The “DDoSia” botnet, linked to pro-Russian actors, repeatedly targeted government and industry websites. The botnet leveraged compromised IoT devices and cloud servers to generate massive volumes of malicious traffic.
- India–Pakistan: Regional hacktivist groups waged tit-for-tat DDoS attacks against each other’s public sector websites. Most incidents ranged between 50 and 100 Gbps, often timed to coincide with key political events.
Despite the relative drop in share, these attacks show that government networks remain high-value targets, especially in geopolitically tense regions.
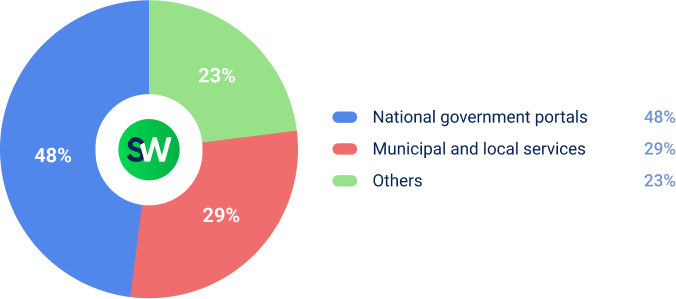
Attacks on government infrastructure focused on services that the public uses, with the most activity targeting national government websites:
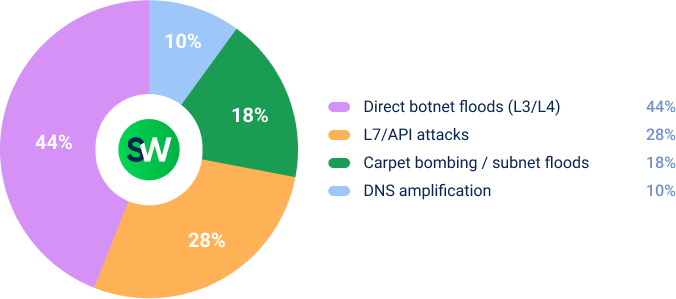
The most common way for hackers to attack was botnet floods, which were often combined with application-layer attacks targeting public APIs and authentication systems.
2.Telecommunications
In the first half of 2025, telecom companies were among the most heavily targeted industries—and suffered some of the most intense and sustained DDoS attacks of the period.
- The largest recorded DDoS attack reached 2.3 Tbps, targeting a Chinese data center provider.
- The longest continuous attack lasted 11 days, averaging ~850 Gbps, and was directed at a telecom provider in Taiwan.
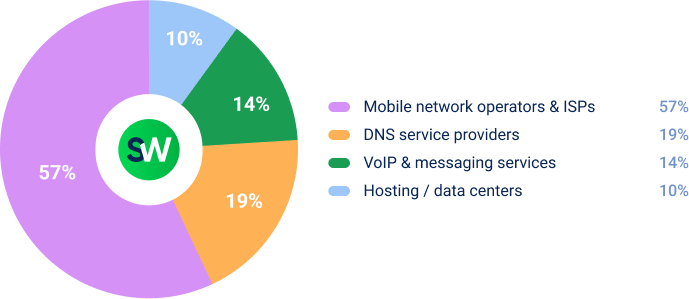
Mobile operators and ISPs were hit the hardest:
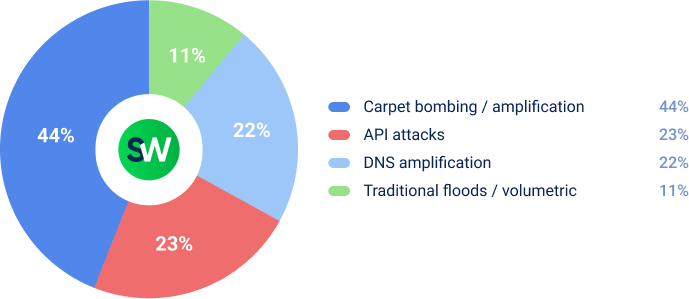
In terms of attack methods, amplification attacks were the most common alongside carpet bombing:
Telecom companies are prime targets because when their networks are disrupted, it affects entire regions.
3. Finance
The finance sector was heavily targeted in H1 2025, with payment gateways absorbing a staggering 72% of all attacks in the industry.
Some of the most powerful DDoS attacks of the first half of the year hit financial services:
- A 1.2 Tbps attack struck a Singapore-based company.
- The longest attack lasted 8 days, sustaining traffic levels of around 350 Gbps.
- However, the majority of attacks were short bursts, averaging just 10 minutes in duration.
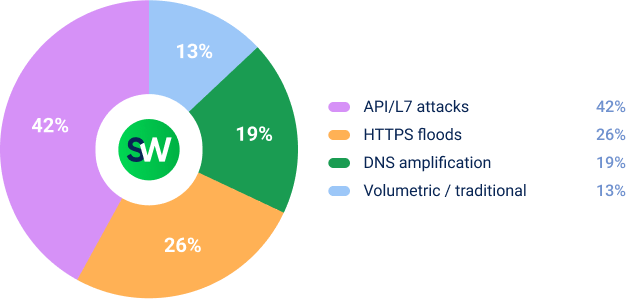
Looking at attack methods, attackers focused on disrupting payments and login systems:
DDoS Attacks by Country
Let’s take a closer look at how DDoS attacks were distributed across countries in H1 2025:
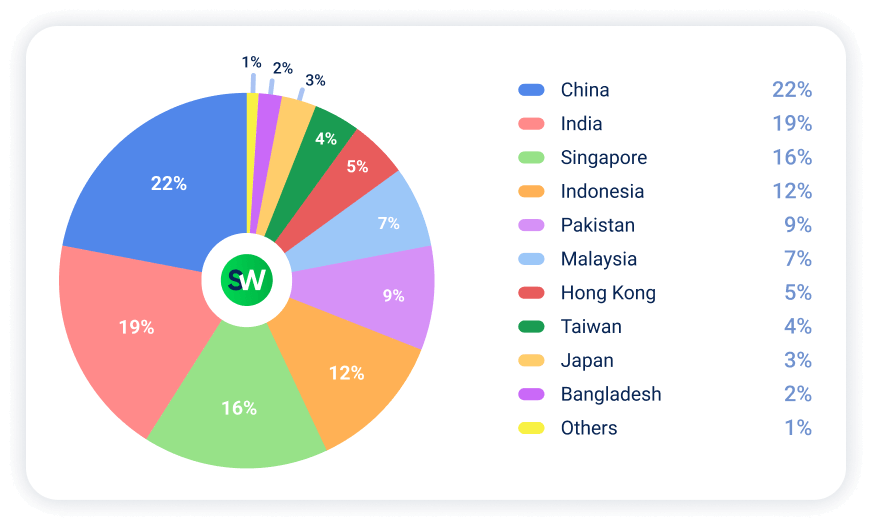
Looking at the distribution of DDoS attacks by country, China overtook India as the most targeted country, while Indonesia and Pakistan saw big increases. China’s attack share rose from 20% to 22%, pushing it ahead of India, which dropped from 20% to 19%.
Indonesia had the biggest shift, going from 7% to 12% of attacks and moving into fourth place. Pakistan also grew significantly, rising from 7% to 9%.
Other changes from H1 2024 to H1 2025:
- Singapore (+): 14% → 16%
- Taiwan (–): 9% → 4%
- Japan (–): 7% → 3%
- Hong Kong: stayed at 5%
South Korea dropped out of the top 10 completely, falling from 2% to under 1%. Malaysia and Bangladesh stayed the same at 7% and 2%, respectively.
More attacks are hitting Southeast Asian countries like Indonesia and Pakistan, while traditional targets like Taiwan and Japan saw fewer attacks.
Quick Highlights
Let’s recap the main trends:
- Overall, DDoS attacks in the Asia-Pacific region (APAC) increased by 116% year-over-year.
- In H1 2025, the three most targeted verticals in APAC were government (21%), telecommunications (18%), and finance (16%).
- API attacks increased 63% year-over-year.
- There was a 3,500× increase in probing attacks. On average, probing attacks lasted 2.8 minutes.
- The average number of botnet devices increased fourfold compared to the previous year.
- The three countries that were attacked the most were China (22%), India (19%), and Singapore (16%). Indonesia saw the biggest rise, from 7% to 12% of attacks, while Taiwan dropped significantly from 9% to 4%.
That’s how the DDoS scene looked in H1. The momentum keeps surprising even us. We’ll keep our eyes on it and keep you informed. Stay sharp—and stay protected with StormWall!

DDoS Protection for Websites
- Activate protection in 10 minutes
- 24/7 technical support




















