Transparent DDoS protection settings, more useful features and attention to detail – since the end of last year, StormWall has added a number of new features to the StormWall Portal. Let’s take a closer look.
DDoS protection for websites
DDoS protection for websites is performed at all levels of the OSI model with full access to real-time analytics in the StormWall Portal. In this section you can set the security parameters applicable for their project.
Greylist
The ability to configure Greylists has been added to the existing standard White- and Black- lists in the StormWall Portal and through the API. The IP addresses and networks included in this list can be checked by the following mechanisms: Redirect, JS validation or CAPTCHA.
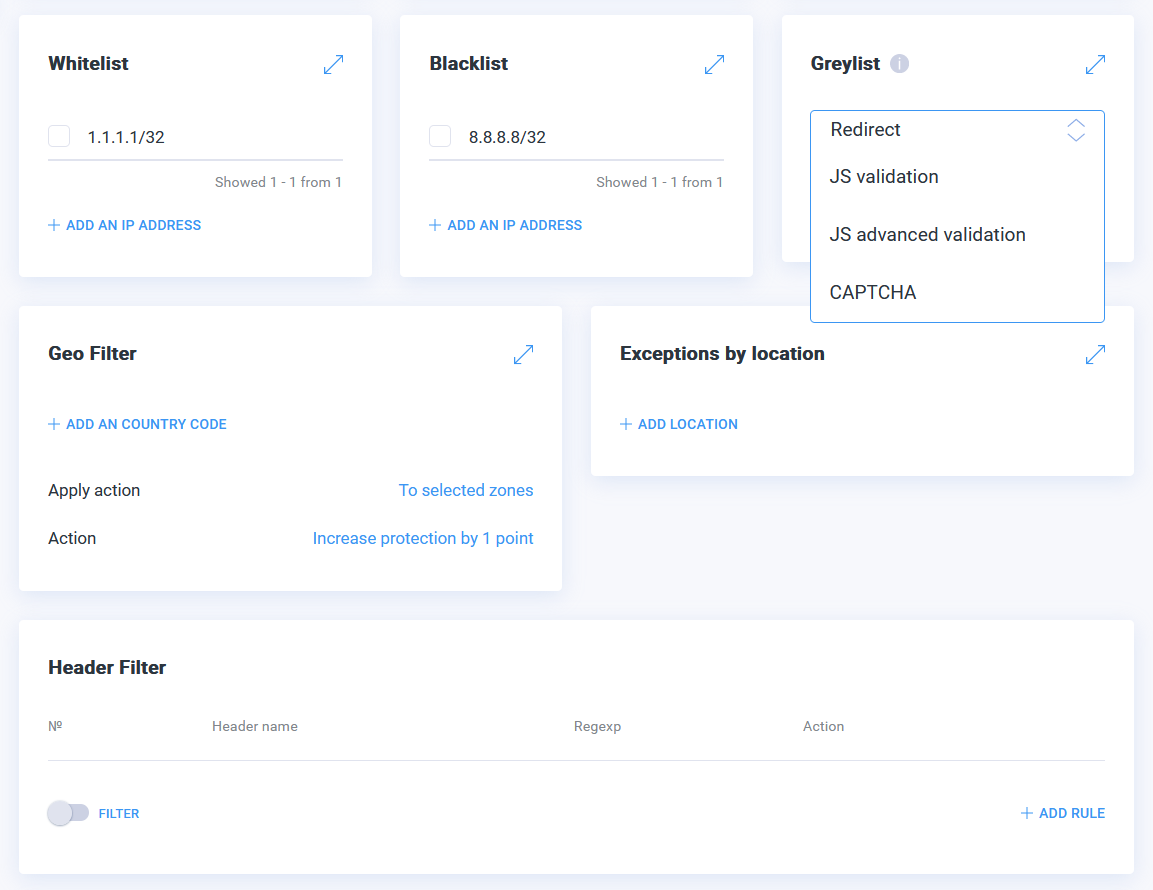
Examples of the Greylists option use:
- suspicious IP addresses, if there are no serious reasons to block them;
- test the protection level without enabling protection for the whole website (for example, you can add tester’s IP to Greylist without changing protection mode for the whole website).
Location Filters
A handy counter for specific locations of the (URL) domain, allows you to determine the number of requests with specific methods for a specified period of time and perform a specific action when this limit is exceeded. Allows you to precisely set the allowed number of requests to specific site URLs.
This addition will help block bots even if they have full browser stack and can bypass other protection mechanisms. This means that, for example, if bots receive the 403 error a certain number of times they will be banned.
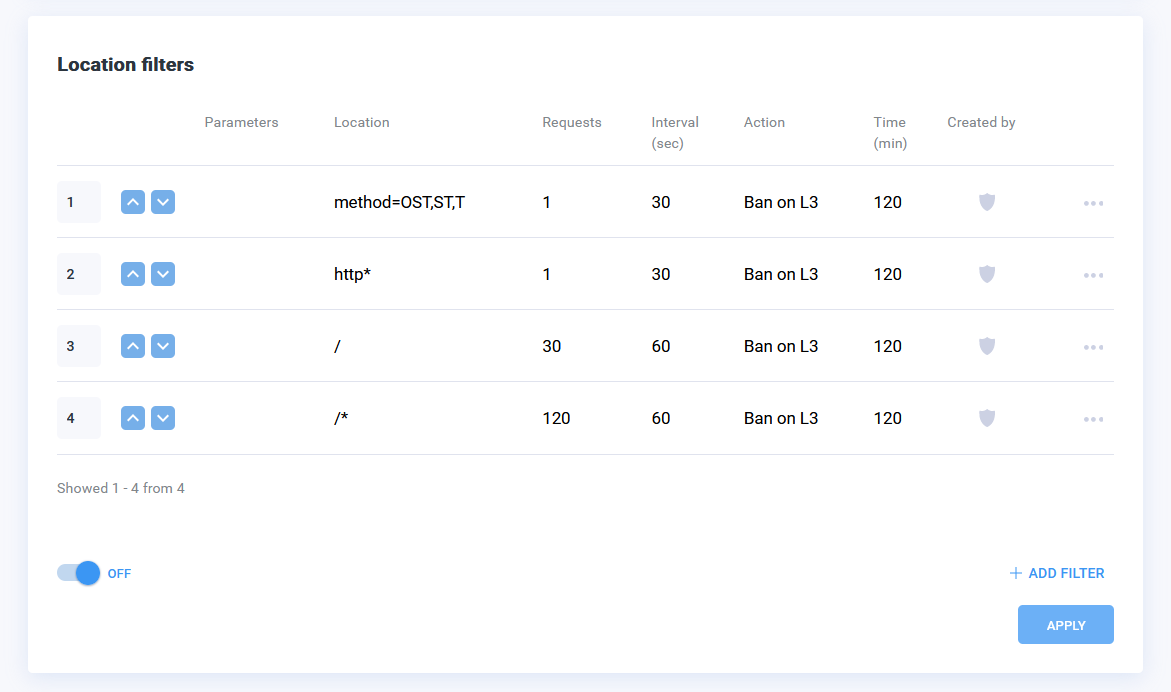
Examples of the Location Filters option use:
- protection against bruteforce (hacking of accounts by guessing passwords);
- identifying requests from bots or people from anti-CAPTCHA services by specifying the maximum number of requests for a long period of time;
- blocking access to the website management system.
Additional functions of location filters:
- API support, the ability to configure automation, filtering by content type, http methods;
- the subject of the calculation is the uid (a unique identifier assigned to the user by the system) and the IP address of the request initiator.
Actions that can be applied in location filters are banning the visitor or logging his requests.
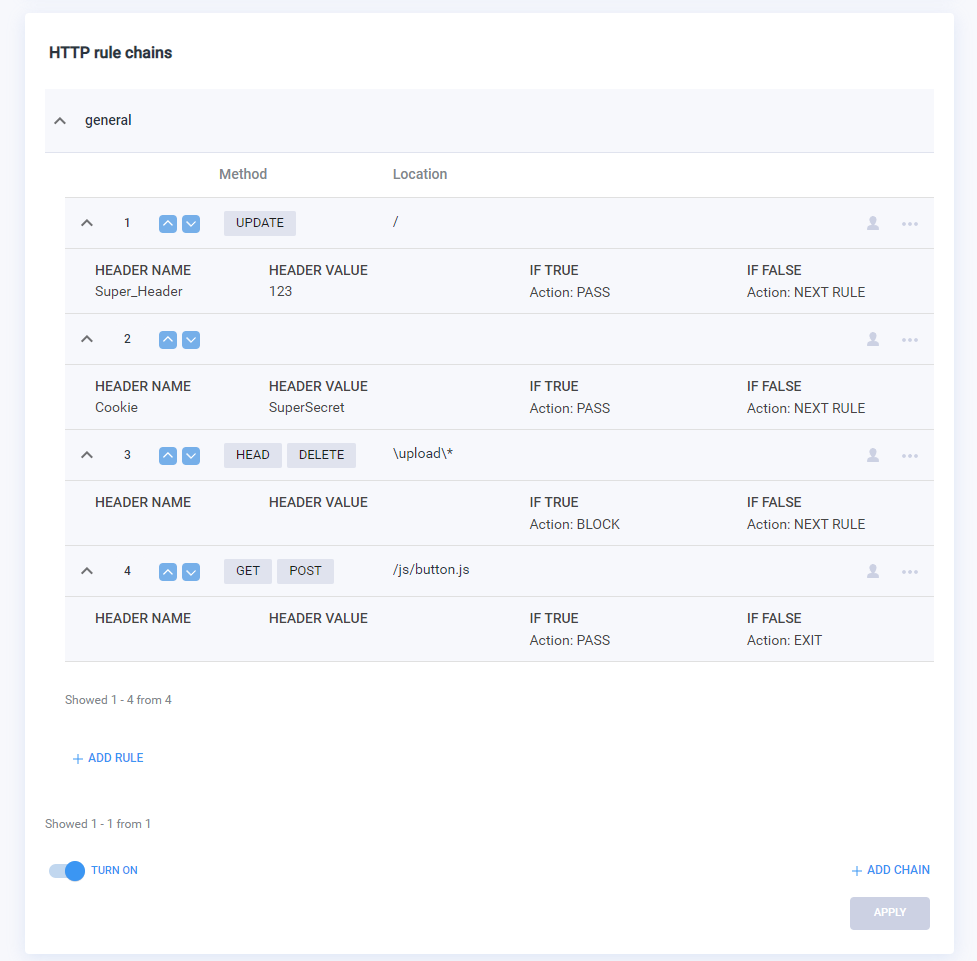
HTTP Rule Chains
The new StormWall Portal feature*, previously available only in WAF solutions, allows an entire constructor of rules to be created over the HTTP protocol – with multi-level checks that take into account headers, locations, and the number of requests in a given time period.
HTTP Rule Chains work as follows: requests are passed through a chain of rules, where you can choose what actions are performed on the request, both when the conditions are met and when the conditions are not met: skip, block, or process in the next chain. With such a tree-like structure, you can create more reliable protection against bots, parsers, and automation tools to bypass the protection.
*Please note that this feature is only available in the Enterprise plan.
Protection of TCP/UDP and BGP network services: setting up black-/white lists
Edit the lists of allowed/prohibited IP addresses or networks: for example, add the IP addresses of partner systems, remote offices for VPN users from specific addresses to the protection exceptions.
All new options listed in the StormWall Portal user can change (set up) on his own or with the help of technical support. It is possible to automate functions and work with the backend of applications and services using the StormWall API.
StormWall is constantly improving the DDoS filtering platform and developing the service towards detailed analytics and maximum manageability. Thus, we plan to increase the volume of network cleaning, add the ability to configure protection against other types of bots – and much more. Follow the updates on the official website and social networks.




















