At the beginning of 2025, the number of DDoS attacks surged across many regions—and MENA was no exception. We recorded a 274% increase in attacks compared to Q1 2024.
What’s driving this explosive growth, and how has the threat landscape changed across MENA countries? Find the answers in our report.

The Big Picture
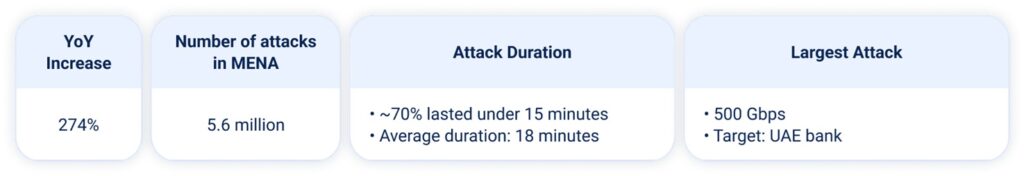
The number of DDoS attacks in the Middle East and North Africa (MENA) remained extremely high in the first quarter of 2025, continuing the sharp upward trend observed last year. The figures are striking: in just three months, we mitigated nearly as many attacks in the region (5.6 million) as we did throughout all of 2024.
Most attacks targeting StormWall clients were short-lived—70% lasted under 15 minutes, with an average duration of 18 minutes. Attackers increasingly rely on hit-and-run tactics, leaving defenders with little time to respond.
730% Surge in DDoS Traffic During Ramadan
According to StormWall’s analytics, the volume of DDoS attacks during Ramadan 2025 skyrocketed—spiking by 730% compared to the monthly average from the previous quarter.
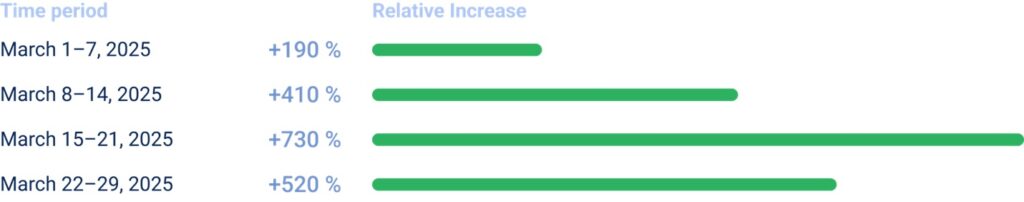
Notably, more than 78% of this traffic originated within the MENA region—a sharp contrast to the usual trend, where most DDoS traffic comes from international botnets.
This shift, combined with the fact that retail saw nearly double the attack growth rate of other sectors, suggests that unfair competition was likely the main driver behind this spike.
API Attacks Up by 140%
In Q1 2025, attackers increasingly targeted exposed API endpoints—especially those that were unauthenticated, poorly secured, or not performance-optimized. Most of these attacks originated from residential proxy networks and low-cost VPS services, rotating through hundreds of IPs per hour to avoid detection.
One notable incident involved a public government API in North Africa that was bombarded for 48 hours straight, reaching up to 1.8 million requests per hour. The attackers varied parameters across requests to bypass detection thresholds and fragment traffic signatures.
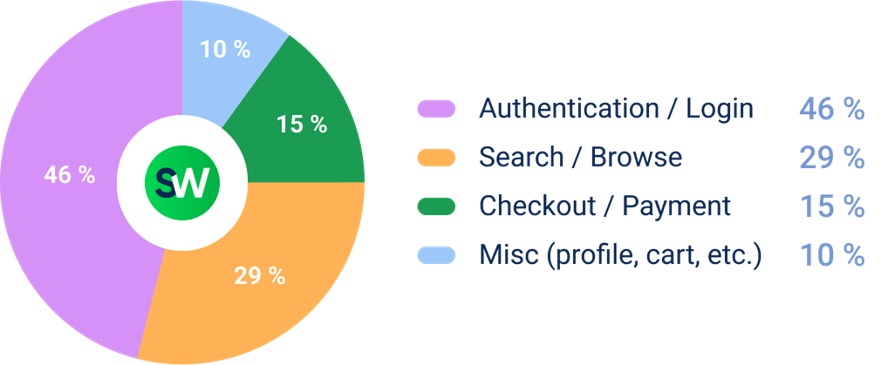
API-layer DDoS attacks are particularly difficult to defend against because they:
- Mimic legitimate traffic
- Match expected formats and usage patterns
- Target high-resource endpoints that are critical to application stability
In 90–95% of cases, these attacks go unnoticed due to their low per-IP request rate and wide distribution. Yet they can silently degrade performance—or even crash the application entirely.
A 61% Increase in Multi-Vector Attacks
In one notably aggressive campaign, attackers executed a continuous 14-day assault, rotating through SYN floods, Mirai botnet waves, SSDP amplification, and other methods. Each phase lasted from 30 minutes to 3 hours before switching tactics—making detection and response far more difficult.
When attackers shift between L3/L4 volumetric floods (like SYN or UDP) and L7 overloads (such as HTTP GET/POST), or blend direct attacks with amplification techniques (e.g. SSDP, NTP), signature-based defenses quickly lose effectiveness. The result is a dynamic and evasive threat that requires behavioral detection and real-time adaptation to stop.
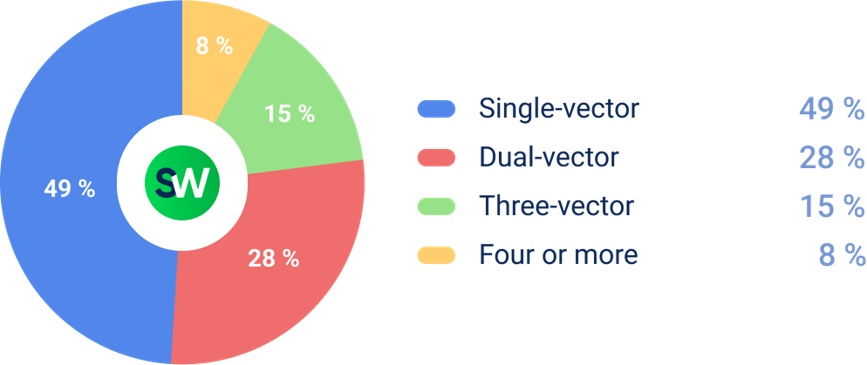
More than half of all DDoS attacks now involve multiple vectors. The more techniques employed, the harder and costlier they are to detect and mitigate.
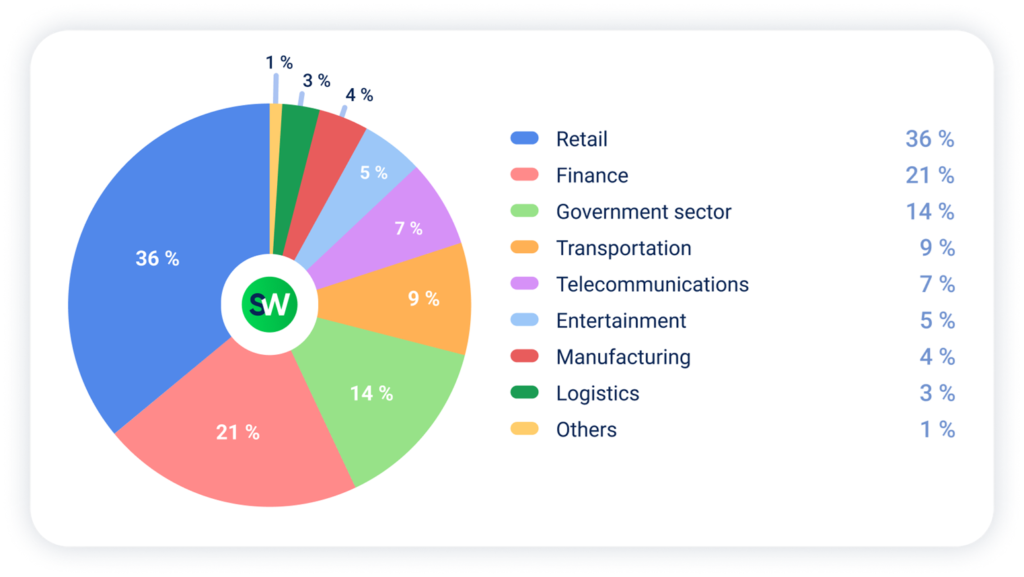
Industry Breakdown
Let’s take a closer look at how DDoS attacks were distributed across different sectors in MENA during Q1 2025:
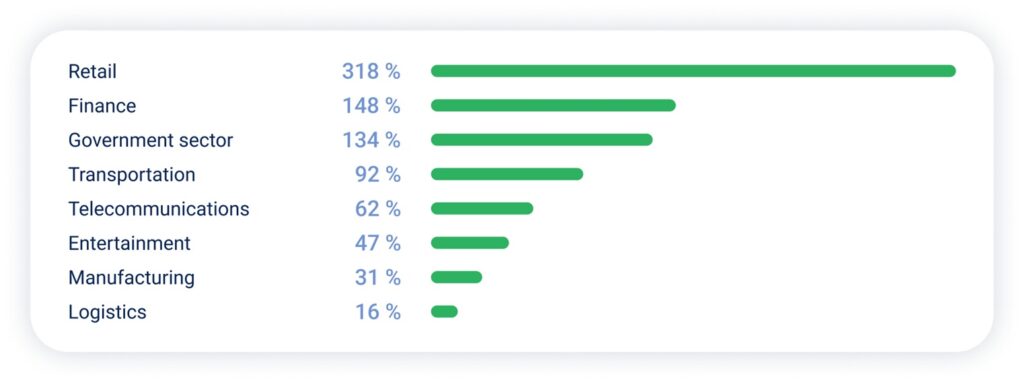
Industries with highest YoY growth in DDoS attacks:
DDoS Relative Risk
Which sectors face the highest risk of being hit by DDoS attacks? The table below shows the relative likelihood by sector based on attack distribution in MENA during Q1 2025:
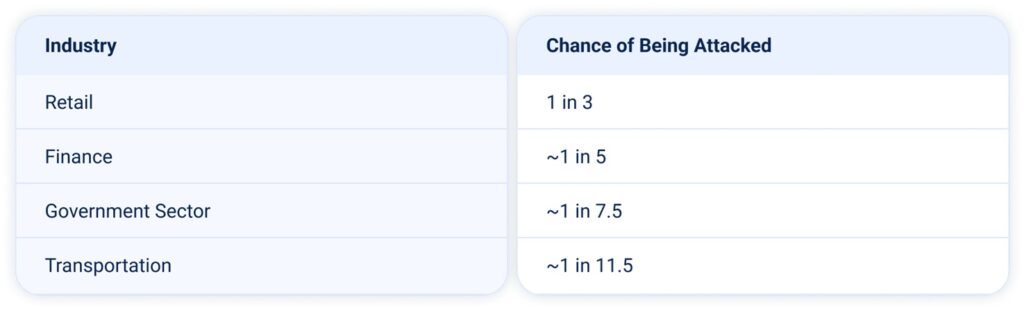
Note: This reflects relative risk within the MENA region, based solely on observed attack distribution. Actual risk also depends on exposure, security posture, and attacker intent.
Top 3 Most Attacked Verticals
Retail

Retail came under heavy fire, especially during the Ramadan sales period (February 14–March 16). Many of the targets were mid-sized online stores. API-based attacks dominated the landscape.
Attackers primarily focused on login pages, checkout flows, and payment APIs. One notable case targeted a major Saudi electronics retailer with a sustained API attack on its mobile checkout platform, peaking at 750,000 requests per second for three hours.
Finance

Compared to a year ago, attacker focus has clearly shifted. While government services absorbed 34% of attacks (mainly hacktivist) in Q1 2024, this pressure eased by Q1 2025. Financial platforms became a primary target, signaling a shift back to financially motivated attacks following the politically driven surge tied to late 2024’s Gaza conflict.
As the conflict subsided, politically motivated attacks on government entities slightly decreased in Q1 2025, while financially driven campaigns gained momentum.
In essence, the DDoS landscape in early 2025 mirrors what we saw in late 2024: large-scale, profit-motivated attacks targeting businesses have become more frequent than hacktivist campaigns—a notable shift from early 2024, when geopolitical tensions fueled a surge in ideologically driven attacks.
Government Sector

The key trend is the growing international scope for attackers and targets, particularly evident in government DDoS campaigns. Global botnets frequently target MENA government services, while MENA-based attackers increasingly retaliate against other regions.
During Q1 2025, malicious traffic targeting MENA government sites originated from countries like Indonesia, India, and Bangladesh. At the same time, hacktivist groups based in the MENA region launched outbound attacks on government infrastructure in Europe and Asia.
Top Inbound Sources of DDoS Traffic to MENA:
- Indonesia – 22%
- India – 19%
- Bangladesh – 15%
- Russia – 12%
- United States – 10%
- Eastern Europe (various) – 8%
- Other (global) – 14%
Top Outbound Sources from MENA Targeting Other Regions:
- Saudi Arabia – 28%
- UAE – 24%
- Egypt – 18%
- Algeria – 11%
- Iraq – 9%
- Other MENA (combined) – 10%
This cross-border escalation highlights the evolving nature of DDoS threats in the public sector and the increasingly global dimension of regional conflicts.
DDoS Attacks by Country
Let’s break down how DDoS attacks were distributed by country in Q1 2025:
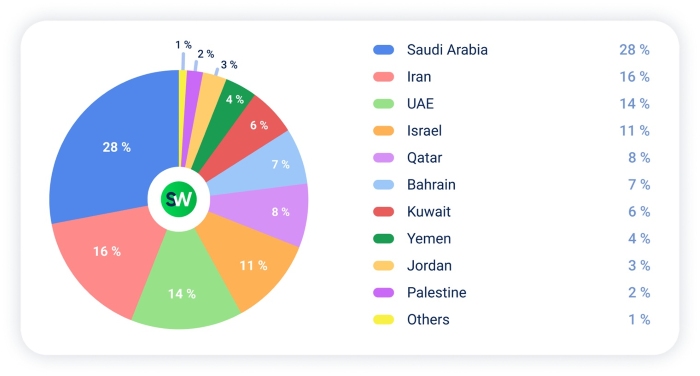
Compared to Q4 2024, Saudi Arabia became the most targeted country in the Middle East in Q1 2025, with its share of DDoS attacks YoY rising sharply from 16% to 28%.
In total, 5.7 million attack events were directed at Saudi digital infrastructure during the quarter—nearly three times the volume recorded in the previous period. The majority of these attacks were at the network layer, accounting for 1.4 million incidents. Common vectors included SYN floods, DNS floods, UDP reflection, and other multi-vector techniques.
Although 85% of the attacks were short (under 10 minutes), many high-impact bursts lasted just 30 to 45 seconds—too fast for some traditional defenses to react effectively.
Notably, emerging DDoS vectors gained traction:
- CLDAP reflection attacks surged by 3,400% quarter-over-quarter
- ESP-based amplification methods increased by 2,300%
Attack motivations varied:
- 39% linked to commercial competition
- 17% attributed to state-affiliated actors
- 11% due to extortion campaigns.
Meanwhile, the UAE’s share of attacks dropped significantly, from 31% to 14%. Iran saw increased targeting activity, doubling its share from 8% to 16%, while Israel continued its downward trend, slipping from 14% to 11%.
Other notable country-level shifts from Q4 2024 to Q1 2025:
- Qatar: 3% → 8%
- Bahrain: 4% → 7%
- Kuwait: 10% → 6%
- Yemen: 2% → 4%
- Jordan: 5% → 3%
- Palestine: 6% → 2%
In Summary
DDoS attacks in MENA surged to unprecedented levels in Q1 2025—driven by local competition, evolving attacker tactics, and ongoing geopolitical tensions. The rapid rise in multi-vector and API-layer attacks, combined with shorter, more intense bursts, shows that threat actors are becoming faster, smarter, and harder to detect.
As attackers shift toward business disruption and financial gain, organizations in the region must respond just as strategically. Traditional defenses are no longer enough. It’s time for companies to adopt adaptive, layered DDoS protection—especially at the application and API levels—if they want to stay ahead of this increasingly dynamic threat landscape.

DDoS Protection for Websites
- Activate protection in 10 minutes
- 24/7 technical support




















