The year 2025 set new records — both in the number and power of DDoS attacks, as well as in the activity of emerging botnets. This report brings together all key figures, trends, and analytical insights.

Key DDoS Trends in 2025
DDoS Attacks Tripled
In 2025, the total number of DDoS attacks worldwide increased by 198% compared to 2024. Over the year, StormWall mitigated 19.4 million DDoS attacks, up from 6.6 million in 2024.
According to our analysts, attack activity grew steadily throughout the year:
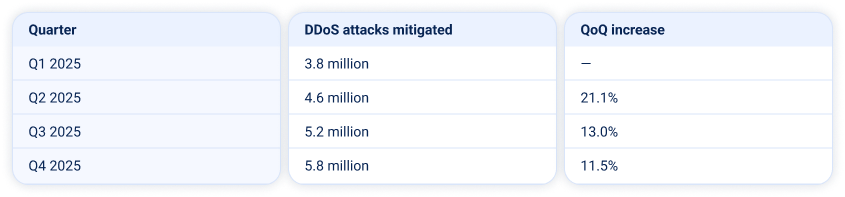
At the same time, the average duration of DDoS attacks rose to 31 minutes — 8 minutes longer than in 2024.
The most powerful DDoS attack mitigated by StormWall in 2025 peaked at 2.1 Tbps.
Multi-Vector DDoS Attacks Up by 83%
In 2025, attackers increasingly combined multiple vectors when launching DDoS attacks. From January to June, multi-vector attacks accounted for 29% of all incidents mitigated by StormWall.
The most common DDoS method combinations we observed in 2025 included:
- DNS amplification attacks combined with HTTP flooding
- Volumetric attacks combined with application-layer attacks and the exploitation of protocol vulnerabilities
“Carpet Bombing” Attacks Continue to Rise
Attackers increasingly distributed malicious traffic across wide IP address ranges and subnets instead of concentrating on individual attack vectors. This trend has been gaining momentum for several years, highlighting the effectiveness of so-called “carpet bombing” attacks within the modern DDoS landscape.
In 2025, most carpet bombing attacks were carried out using the UDP protocol. The number of such attacks increased by 231% compared to 2024. On average, attackers simultaneously targeted approximately 15,000 ports.
In most cases, parallel strikes were delivered using packets that varied randomly in both content and volume. The largest carpet bombing attack recorded in 2025 reached a peak power of 4.8 Tbps and lasted 69 seconds.
Probing: Up 300% YoY
Probing is a technique in which attackers test a target’s defenses by sending small amounts of malicious traffic to uncover weaknesses before launching a full-scale attack. This type of reconnaissance has tripled year over year, indicating a higher overall level of attacker sophistication.
In the financial sector, for example, approximately 45% of attacks mitigated by StormWall involved probing. Across all industries, the figure was closer to 25%.
APIs Back in the Crosshairs
Over the past year, the number of DDoS attacks targeting APIs increased by 43%. The primary driver of this growth remains the insufficient protection of API infrastructure, which continues to be a widespread issue across many regions.
Most incidents continued to affect the banking and retail sectors. These industries rely heavily on APIs, and their availability directly impacts revenue and transaction continuity.
In most cases, attackers used botnets to target API endpoints. In 2025, the number of automated DDoS attacks against APIs surged by 138% compared to 2024. The majority of bot traffic was directed at online banking APIs and payment systems.
Botnets in 2025: New Names Emerge
In 2025, the average power of botnets increased 2.5 times. New players entered the threat landscape, capable of launching DDoS attacks on an unprecedented scale. The most notable among them were AISURU and Kimwolf.
AISURU emerged as the most significant botnet of the year. According to various estimates, it controls 1 to 4 million infected devices, including routers, CCTV cameras, video recorders, and other IoT devices. It is also known that the botnet is distributed in Brazil as a subscription-based service, which can be used to launch targeted DDoS attacks.
AISURU has already been responsible for attacks reaching 11 Tbps and 22.2 Tbps (using more than 404,000 infected devices), as well as a carpet bombing attack peaking at 29.7 Tbps. The consequences of this botnet’s activity were experienced by the KrebsOnSecurity website, as well as the resources of internet providers AT&T, Comcast, Verizon, and other well-known companies.
Another large-scale botnet discovered in October 2025 was Kimwolf. Most attacks involving this botnet occurred toward the end of the year. Around the same time, researchers revealed both the difficulty of detecting these attacks and the scale of the threat: the botnet includes at least 2 million compromised tablets, set-top boxes, and other devices running Android TV OS worldwide.
In addition, throughout 2025 we observed increased activity from several other botnets, including Eleven11Bot/RapperBot, Broadside (primarily targeting the maritime logistics sector), Murdoc, PumaBot, and BadBox 2.0.
Evolution of AI-Powered DDoS Tools
In 2025, the rapid development of AI has made launching DDoS attacks easier than ever. “DDoS-as-a-Service” platforms now often include built-in functionality based on tools like WormGPT and FraudGPT, which are widely used to generate attack scripts.
Some malicious applications have introduced AI-powered assistants. These tools allow attackers to describe a target in plain human language — removing the need for deep technical knowledge or a specialized background.
AI-driven malicious systems are increasingly capable to monitor traffic patterns in real time, identify weaknesses in a target’s defenses, and dynamically adjust attack parameters to avoid detection or strike at the most effective moment — such as during maintenance windows or peak load periods.
DDoS Attacks by Industry
In the first half of the year, the growth of DDoS attacks was driven primarily by political events, with most incidents linked to hacktivist activity, StormWall analysts note. However, in the second half of 2025, attackers increasingly shifted toward financially motivated goals. During this period, we recorded a noticeable rise in DDoS attacks related to extortion and competitive conflicts between businesses.
This shift in attacker motivation directly reshaped the distribution of DDoS attacks across industries. In the first half of the year, the public sector and critical infrastructure organizations were targeted most frequently. In the second half, attackers predictably shifted their focus toward financial services and the entertainment industry.
Overall, the global distribution of DDoS attacks across industries in 2025 was as follows:
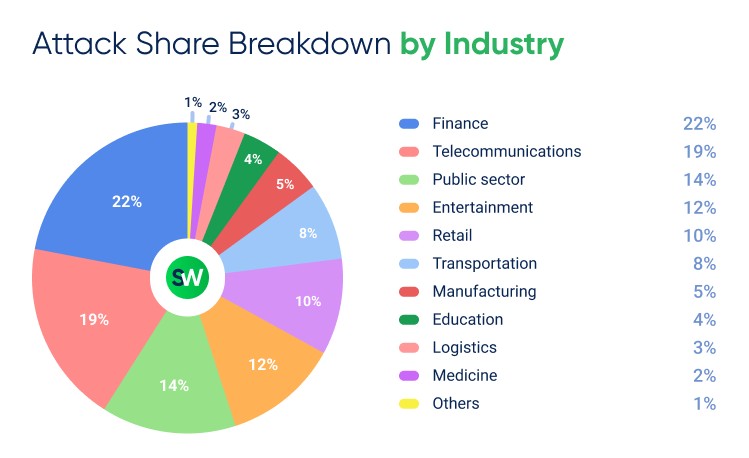
For the second year in a row, the financial sector topped our ranking, accounting for 22% of all DDoS attacks worldwide. Telecommunications ranked second place with 19%, followed by the public sector at 14%.
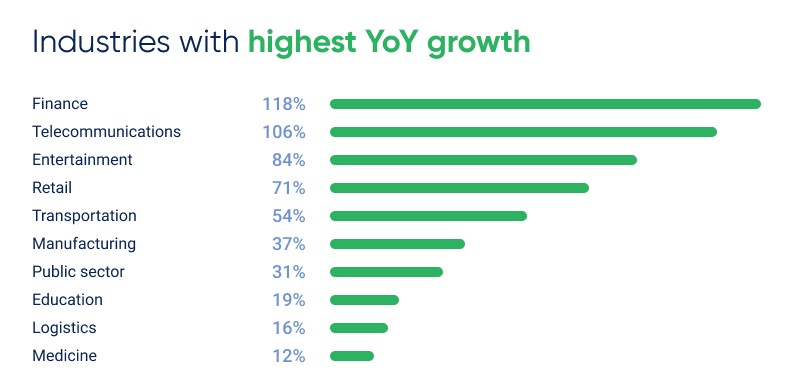
The financial sector also recorded the highest year-over-year growth rate in the number of DDoS attacks, with an increase of 118% compared to the previous year. Telecommunications ranked second (+106%), followed by the entertainment industry, where attacks grew by 84% year over year.
Growth by industry in 2025:
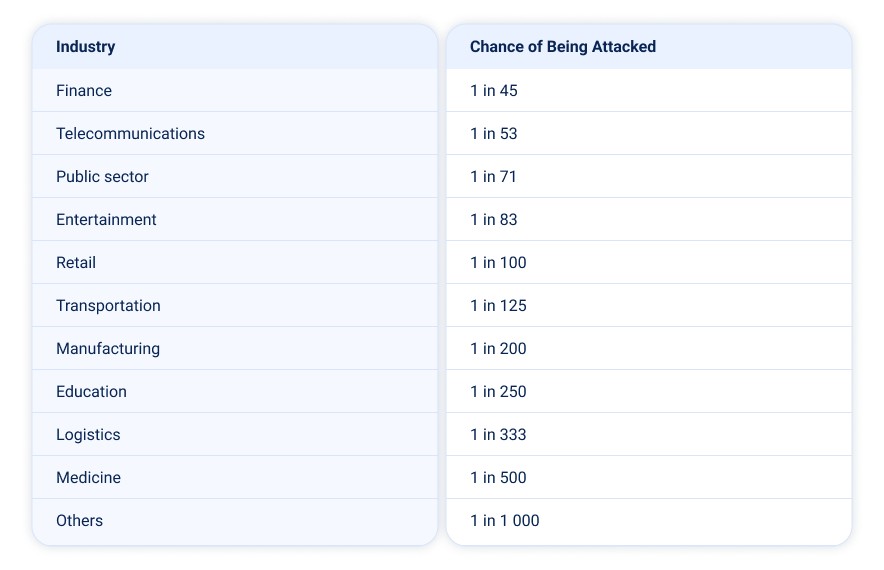
As part of the study, we also identified industries that faced the highest likelihood of DDoS attacks. The probability of an organization being targeted in each sector is shown below:
Next, let’s take a closer look at the industries most frequently targeted by DDoS attacks worldwide.
1. Financial Services
As noted earlier, this sector has maintained the top position in our ranking for the second year in a row. In 2025, according to our data, approximately one in five DDoS attacks worldwide targeted financial-sector resources (22%).
Around 68% of attacks were aimed at online banking platforms and payment systems. This targeting strategy is logical: disruptions to such services result in immediate financial losses and rapidly erode customer trust. As a result, affected organizations are often under significant pressure to restore services quickly — including, in some cases, paying ransom demands.
More than 90% of DDoS incidents targeting the financial sector involved volumetric attacks, with the following distribution:
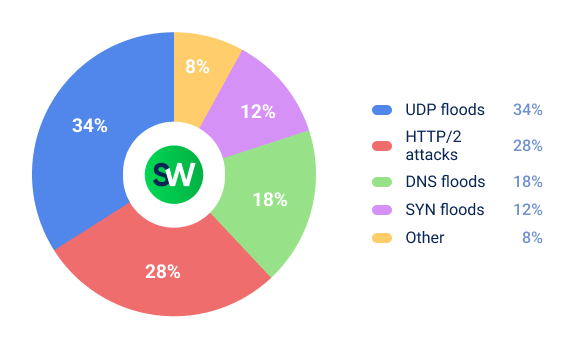
In approximately 45% of cases, attackers employed probing DDoS attacks. These techniques were used to assess whether the target had specialized protection in place and to evaluate its current level of vulnerability. After gathering this information, attackers often proceeded with full-scale attacks to achieve their objectives.
2. Telecommunications
For telecom operators, cloud providers, and other telecommunications companies, 2025 proved to be no less challenging than 2024. The industry once again ranked among the top three most targeted sectors, with its global share of DDoS attacks rising to 19%. For comparison, in 2024 telecom accounted for 16% of all DDoS attacks recorded by StormWall.
Attackers primarily focused on traditional attack vectors. Partly for this reason, around one third (33%) of all network-layer DDoS attacks targeted the telecommunications sector. This trend is further reflected in the common DDoS attack types observed within the industry:
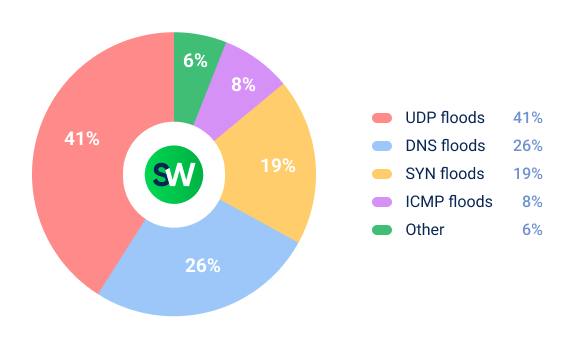
3. Public Sector
As noted earlier, politically motivated DDoS attacks were more prevalent during the first half of the year. Overall, in 2025, hacktivist groups were responsible for 20% of all public sector incidents, with 91.5% of those incidents involving DDoS attacks.
At the same time, the number of politically motivated incidents continued to grow. In the first half of 2025, such attacks increased by 62% compared to the same period of the previous year, while in the second half they rose by an additional 31%.
Most often, attackers directed malicious traffic at government websites. This is also reflected in our analysis of the most common types of DDoS attacks targeting the public sector:
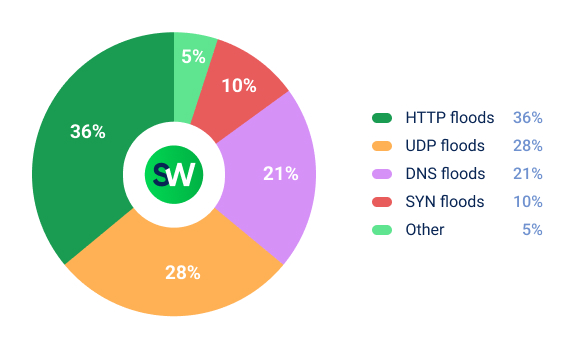
Countries and DDoS Attacks: The 2025 Ranking
According to our analysts, the top three countries by the number of DDoS attacks in 2025 were China, the United States, and India. These same countries also held the top three positions in 2024.
However, while the United States was the undisputed leader in 2024 with a share of 14.3%, this year it has ceded the top position to China, which accounted for 16.2% of all DDoS attacks worldwide. The 2025 leader increased its share from 12.8% to 16.2%, largely driven by ongoing geopolitical tensions in Asia.
The United States moved to second place in the ranking, while India retained its third position. All three leading countries increased their share of the total volume of DDoS attacks. In 2024, the top three countries accounted for 37.3% of all DDoS attacks, while in 2025 their combined share rose to 43.6%.
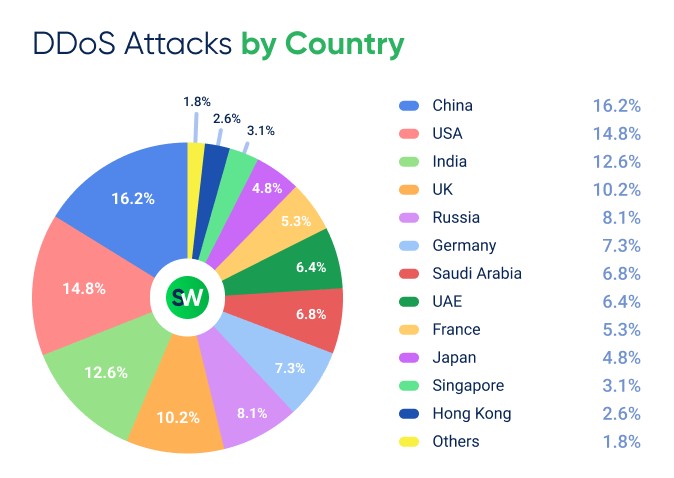
We also recorded a sharp decline in attacker activity targeting European countries. Last year, increased activity in the region was largely driven by elections in the United Kingdom, France, and Germany. In 2025, however, Europe saw far fewer major political events, and hacktivists shifted their focus to other regions.
At the same time, Saudi Arabia entered our top 10 ranking for the first time. The country’s share of DDoS attacks nearly doubled year over year — rising from 3.8% in 2024 to 6.8% in 2025. By contrast, other Middle Eastern countries recorded a decline. For example, the share of the United Arab Emirates declined from 8.1% to 6.4% over the year.
Significant changes were also observed across Asia. Singapore, the primary DDoS target in the region in 2024 (6.8%), saw its share drop to 3.1%. At the same time, Japan (4.8%) and Hong Kong (2.6%) entered our ranking in 2025. Both appeared in the list for the first time.
Primary Sources of DDoS Attacks
The leading source country of DDoS attack traffic was Indonesia. Compared to 2021, the volume of HTTP flooding traffic originating from Indonesia increased by 32,000%. Other major sources of attacks included Argentina, Ukraine, and Russia.
In the largest DDoS attacks, IP addresses from 147 countries were involved. In many cases, the geographic origin of the attack did not match the location of the target. This is expected: attackers increasingly rely on globally distributed compromised devices, making DDoS attacks a truly global phenomenon.
What’s Next?
If the current DDoS trends continue, StormWall is expected to mitigate up to 58 million attacks in 2026 — three times more than in 2025. Moreover, most of these attacks are likely to be larger in scale and more difficult to detect and respond to.
That’s why at StormWall we always stay one step ahead of emerging DDoS threats. We continuously expand our global scrubbing infrastructure, enhance the capabilities of our protection solutions, and closely monitor changes in the cyber threat landscape.
Today, readiness for modern DDoS attacks is no longer a recommendation — it’s a mandatory requirement for business continuity and growth. Professional DDoS protection has become a critical component of any infrastructure. And if you’re currently looking for a reliable DDoS protection solution, contact us to discuss how we can improve your security posture.




















