Products & Services



Not sure which product is right for you?
Request a Call
Resources 
Partners
Under Attack?
Home Page / Resources / How StormWall Works
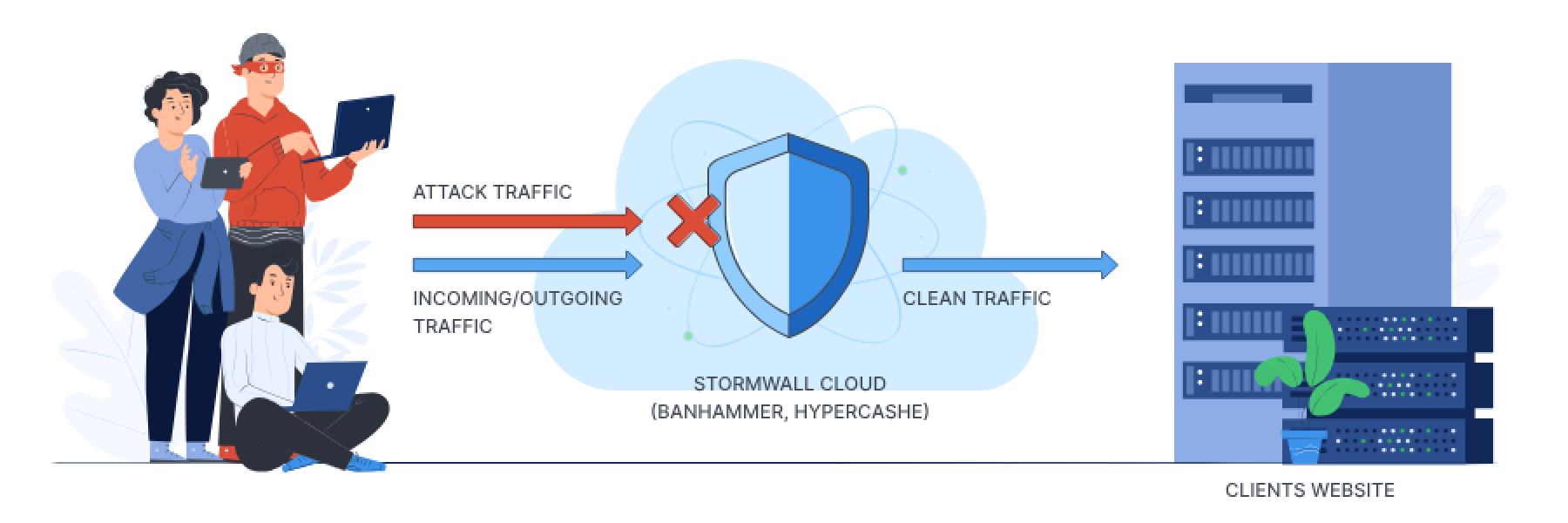
Website protection
You redirect your DNS record (yourself or with our help) to the protected IP
We proxy traffic from the visitors of your website, redirecting to your server only clean traffic saving real visitors’ IPs in HTTP header.
You can read more about what DDoS attacks are and how you can protect yourself in the article “What is DDoS (Distributed Denial of Service)“
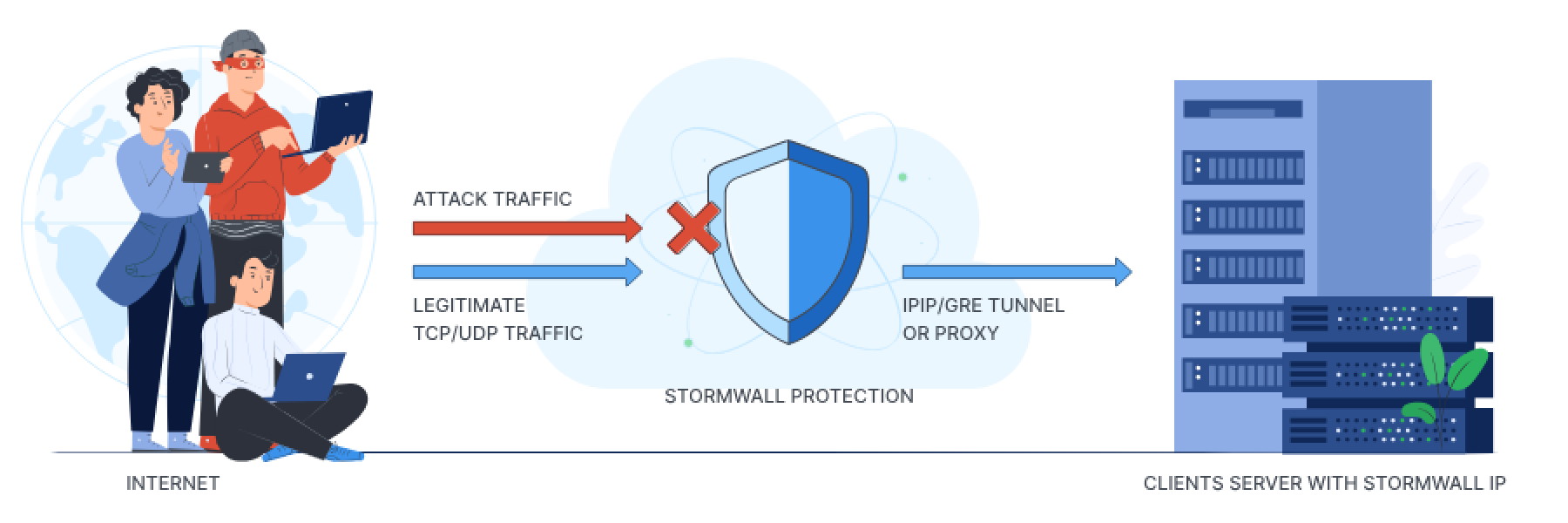
IP protection (TCP/UDP)
Connection is established with GRE/IPIP tunnel or using proxy.
IPIP/GRE tunnel is possible if you are using *nix system (Linux, FreeBSD) or specialized router (Cisco, Mikrotik etc.). In this case we «teleport» protected Storm IP to your equipment and you use it for your clients.
When you use OS Windows on your server, proxy is used. In these cases all the requests from your clients will come from one IP address.
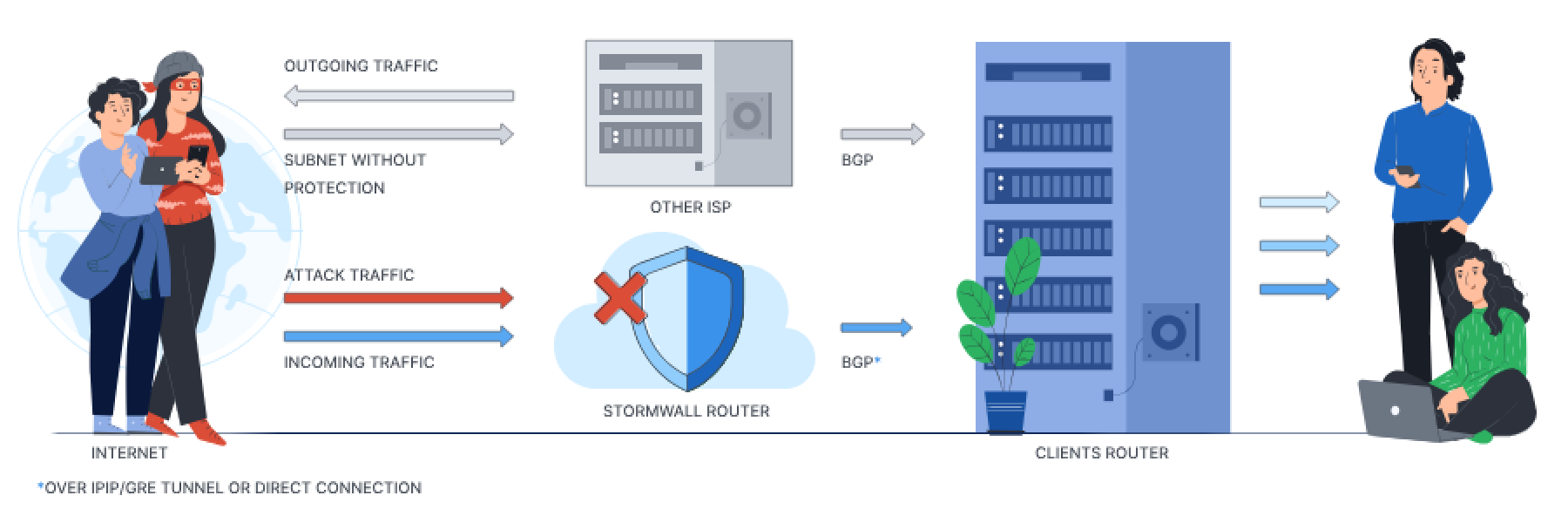
Network protection (BGP)
We establish GRE/IPIP/MPLS tunnel or physical connection with you on one or our connection points
We set up a BGP session which you use to announce your IP prefixes
We accept your announcement, filter all the traffic and deliver only legitimate traffic to your router
You can divert all traffic through StormWall or only incoming traffic, depending on your needs. You can use protection service always or activate it yourself only in case of attack.
Points of Presence
> 5 000Gbit/s
Filtering Capacity
Kazakhstan (Almaty)
Coming 2025
China (Hong Kong)
hkg.stormwall.network
Equinix HK1
Indonesia (Jakarta)
id.stormwall.network
jak.stormwall.network
Cyber Building - JKT with IDCloudHost
Singapore
sg.stormwall.network
Equinix SG3 with IDCloudHost
UAE (Dubai)
ae.stormwall.network
SmartHub Fujairah
Bulgaria (Sofia)
sof.stormwall.network
Telepoint Center

Brazil (São Paulo)
Coming 2025
USA (Washington D.C.)
was.stormwall.network
Equinix DC3
Germany (Frankfurt am Main)
fra.stormwall.network Equinix FR5
fra2.stormwall.network e-Shelter FR1
Scrubbing Centers
Offices
Console Connect Locations
> 5 000Gbit/s
bandwidth without connection inspection (stateless) - processing IP packets on ACL/FlowSpec level without TCP connection check (blocking TCP/UDP amplifications)
User's manual
You can download the user manual from this link



















