In Q2 2024, DDoS attacks increased by 104% YoY. Europe received more DDoS attacks than the US, which is highly unusual.

We’ll get into the numbers later in the report. For now, let’s discuss what exactly happened in Q2 2024 that broke the mold in terms of the geographic distribution of attacks.
- The biggest reason is the historic EU parliamentary election — the first since Brexit that doesn’t include the UK. As voters in the EU’s 27 member states went to the polls on June 6–9, hacktivists (hackers who don’t seek profit but political goals) and state-sponsored APTs (organized hacking units, typically endorsed by a state) targeted government websites.
- As a side effect, our data shows that 31% of attacks were in the government vertical, and compared to the previous quarter, the amount of bad traffic in this vertical increased by 183%.
- At the same time, in Q2 2024, Europe had local elections in several member states. The Belgian Prime Minister resigned and this caused such a stir online that Belgium became the most attacked country — this small state accounted for 14.8% share of global DDoS attacks.
- In Q2 2024, we’ve seen more DDoS attacks hitting web applications and APIs. These attacks are mostly going after the finance, telecom and retail industries.
The Biggest Trend this Quarter
The U.S., India, and China are the largest targets for DDoS attacks — this is what all DDoS reports typically show and what our previous DDoS reports have shown.
In the first quarter of 2024, for example, these three countries accounted for about 37% of global DDoS traffic, while in Europe we saw about 30%. That was the usual state of things — until this quarter happened.
Suddenly, 50.4% of all malicious traffic went to targets in EU territories. On a global scale, the US, China and India now account for only 23.8% in Q2 2024.
What caused this? What’s the impact? And what is likely to happen next? We’ll try to answer these questions in today’s report.
Welcome to the Q2 2024 DDoS Threat Report, global edition. This report covers DDoS attacks against StormWall’s customers in Q2 2024 as observed through our traffic filtering network.
How Elections Affected Legitimate and DDoS Traffic in the EU
During election periods, there were two distinct traffic patterns: legitimate traffic dropped by about 10% on the days when people went to the voting booths, and then increased by about 20% above normal when the election results were announced. This is a side effect of people’s habits, but what about malicious traffic?
According to our data, bot traffic in the EU has increased by 1100% during elections. DDoS activity peaked on June 5, one day before the EU parliamentary elections began, and continued to peak until June 6. From there, the DDoS traffic began to subside until June 9, when the elections ended.
We saw something very similar in Q1 2024 in the APAC region, when Taiwan was attacked so much during the elections on January 13, 2024 that it became the second most attacked nation in all of Asia.
There are multiple takeaways from this:
- First, whenever something politically significant happens, such as an election, it will inevitably cause a spike in DDoS attacks, and hackers will target government services in particular — governments are now the most targeted by DDoS and they need to prepare accordingly.
- Second, the majority of DDoS traffic now comes from state-sponsored APTs or hacktivists — they’re highly organized, well-funded and sophisticated criminal entities. What we’re seeing in DDoS today is very similar to the rise of US crime syndicates in the 1920s. You could say that gangs like Killnet and HackNeT are the modern equivalent of Al Capone and Meyer Lansky — they’re very very powerful.
Attack Share Breakdown by Industry
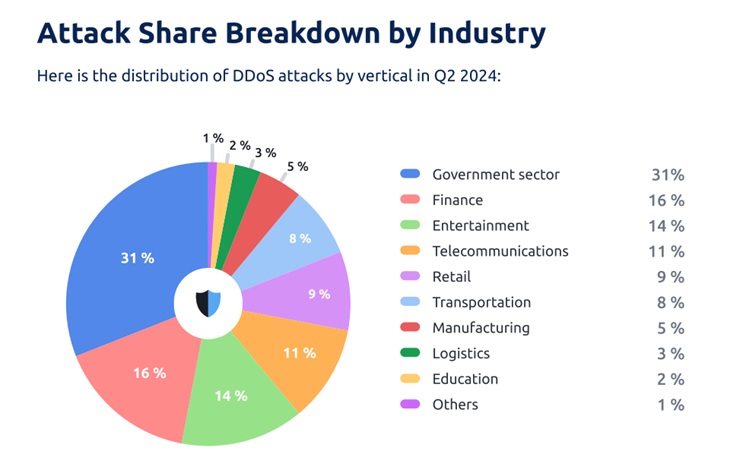

Here are the main trends to highlight this quarter:
- DDoS actors absolutely slammed government services in Q2 2024. StormWall saw a 31% share and 183% year-over-year growth in this vertical.
- Attackers also started to focus more on financial services, whose share increased from 12% last quarter to 16%. The growth here is almost as strong – 126% YoY.
- Another industry where we saw a significant increase in DDoS traffic was the entertainment industry, which saw an 82% increase in DDoS traffic.
- Telecom providers were also hit hard by DDoS attacks. According to our data, the share of attacks on telecom operators is 14%, with an increase of 43% year-on-year.
Let’s break down each of these verticals in a little bit more detail.
Government sector
Overall, the government sector saw 31% of attacks, and we saw a 183% year-over-year growth in this vertical.
The majority of government infrastructure attacks were directed at targets in the EU, South Korea, and North Korea — countries that held elections in April and June 2024.
On June 5 and 6, malicious traffic spiked in the Netherlands. Another major attack targeted the German Christian Democratic Party, bringing down parts of its infrastructure.
There was another attack we’d like to discuss. It’s an incident that affected and brought down French government websites in March.
The French Prime Minister’s Office reported that “several government departments have been the subject of cyber-attacks whose technical methods are conventional but whose intensity is unprecedented,” limiting access to online government resources.
This means that the hackers didn’t use advanced techniques, but instead were able to overwhelm protection through sheer volume of requests.
The reason it’s worth mentioning here is because we’ve been tracking an alarming trend: a very rapid growth of botnets.
We previously reported that the average number of devices in botnets grew from 6,000 in Q2 2023 to 18,000 in Q2 2024 — meaning that, on average, botnets grew 3 times size. This was enough to generate attacks in excess of 1 Tbit/s. The largest attack we mitigated in Q2 2024 reached 1.5 Tbit/s.
Botnets form when devices hijacked by an attacker are connected to a network that the hacker controls from a central control server — that’s exactly the type of threat capable of generating this much malicious traffic. We’re now seeing what it looks like when these botnets are deployed.
Finance
We saw 16% of DDoS attacks in the Financial industry, and recorded a YoY growth of 126%. Finance was both the second biggest vertical by attack share and by rate of growth.
Banks were attacked in Europe, MENA, and APAC. The attacks on banks were targeted and showed typical signs of APT activity, meaning that the banking sector is being actively targeted by organized groups of hackers and politically motivated actors with ideological agendas.
Entertainment
The entertainment sector experienced 14% of DDoS attacks and 82% growth, placing it third in terms of sheer number of attacks, ahead of telecommunications. But what’s behind this?
Threat actors focus on events that attract a lot of attention. This is true whether they are looking for profit or have a political agenda — it means they can make the biggest splash possible. The two high-profile events that started in Q2 2024 were, of course, the European Parliament elections and UEFA Euro 2024.
The UEFA began on June 14 and will run until July 14, 2024, and we immediately noticed increased DDoS activity. On Sunday, June 16, we mitigated an attack against a sports streaming service that reached 650 Gbp/s and lasted for 3 hours, slightly longer than the actual match. We also saw several smaller attacks on sports streaming, betting, and news sites that peaked during the games.
Telecommunications
In the telecom sector, we saw 11% of attacks and a relatively modest growth of 43%. Telecom operators are always in the high-risk zone when it comes to DDoS attacks. Large providers have a large footprint and process personal data for millions of customers – if a breach occurs, it is sure to make headlines. While DDoS attacks don’t directly cause data breaches, criminals use them as a distraction while they attack other vectors – it’s called smokescreening.
The largest attack we have seen against a telecom client reached over 1000 Gbit/s and targeted a customer in APAC. StormWall successfully migrated the attack and the customer felt no impact. Telecom attacks were some of the longest lasting: they averaged 5 hours in April, 8 hours in May, and reached 16 hours in June 2024.
DDoS Attacks By Country
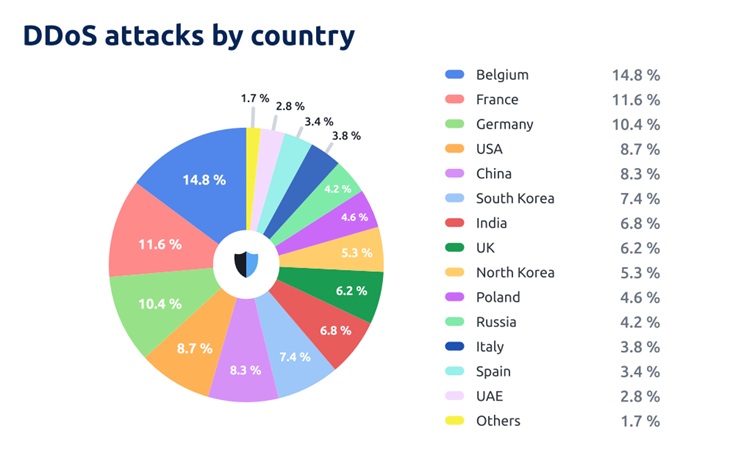
DDoS Attacks Follow Elections
You’ve probably heard that people are calling 2024 the election year — 64 countries are electing their leaders, and there’s also an election for the EU Parliament. Where there are elections, DDoS attacks increase dramatically — that’s the trend we’ve seen since the beginning of the year. It continues through Q2 2024. Let’s break down the table above.
The biggest surprise in terms of the geography of the attacks is that Europe is getting hit the hardest this quarter, which isn’t something we’ve seen before.We’re feeling the effects of the parliamentary elections in the UE and local elections that took place in June in Belgium, and Iceland.
As a result, 14.8% of DDoS attacks were in Belgium — that’s slightly more than the US had last quarter. France, in second place (11.6%), was attacked about as much this quarter as the second most attacked country last year, which was India. Germany, in third place, accounts for 10.4% of DDoS traffic.
Also note the unusually high positions of South and North Korea in the table:7.4% and 5.3% respectively. Elections were held in both Koreas in April, and this is the effect.
Conclusions
In the second quarter of 2024, 50.4% of all malicious traffic went to targets in EU territories. Geographically, the US was the second most attacked region after Europe. Asia – third. Hackers followed after political events as if on a leash, with the majority of attacks in Europe occurring just before, during or after various elections.
Perhaps since the start of the war in Ukraine, we have seen malicious traffic from hacktivists start to overshadow that from hackers looking to make a profit. This quarter underscored just how true that is — hacktivism is now what truly defines DDoS attacks: it dictates where they happen, how they happen, and why they happen.
The line between geopolitics and cybercrime has not just blurred — it has vanished.

DDoS Protection for Websites
- Activate protection in 10 minutes
- 24/7 technical support




















