In 2024, StormWall analyzed and mitigated DDoS attacks across Asia-Pacific, uncovering critical trends that impact businesses. This report highlights the most targeted industries, emerging attack vectors, and key insights drawn from real-world data collected at our global scrubbing centers.

These findings are based on real-world data from StormWall’s scrubbing centers worldwide, including our facility in Singapore. Our network is designed to withstand massive traffic surges, handling sustained attacks exceeding 5 Tbps.
Our infrastructure is built to handle extreme traffic surges, mitigating sustained attacks exceeding 5 Tbps. With a strong presence in APAC, including our Singapore facility, we continuously monitor evolving DDoS threats. By sharing these findings, we aim to provide security teams with timely, actionable intelligence to strengthen their defenses.
You might also want to read our global 2024 DDoS report.
A Breakdown of DDoS Attack Trends in APAC in 2024
DDoS attacks in Asia surged by 92% in 2024 compared to the previous year (see our 2023 DDoS report for APAC). This sharp rise coincided with elections in 17 Asia-Pacific countries—such as India, Indonesia, South Korea, and Taiwan—leading to a spike in hacktivist activity.
By Q3, hacktivist attacks had escalated to the point where Hong Kong and South Korea saw higher volumes of malicious traffic than China and India—historically the region’s most targeted countries.
A Closer Look at These Trends
- Attack targets shifted throughout the year. While the government sector was the most attacked overall, the focus changed each quarter. Government websites were the primary targets in Q1 and Q2, coinciding with major elections across APAC. However, in Q3 and Q4, e-commerce platforms faced the most attacks.
- Geopolitics played a major role in cyber attacks. Countries with political or economic ties to Russia—including Indonesia, India, and China—were heavily targeted. Regional rivalries also fueled attacks, with malicious traffic flowing between Pakistan and India. This marks a key shift: over the past 2–3 years, global attack patterns have been driven more by geopolitical tensions than by financial extortion.
- Telecommunications providers endured escalating attacks. The sector climbed from the fourth most targeted industry in Q1 to third in Q2, eventually ranking as the second most attacked sector in both Q3 and Q4.
Let’s take a closer look at the most notable DDoS attack trends in the APAC region in more detail:
Political Events Drive Attack Patterns Across the Region
In 2024, major political events influenced the distribution of DDoS attacks across APAC.
- South Korea emerged as the primary target in April, absorbing 26% of all malicious traffic in the region during its legislative elections.
- Japan experienced a 300% surge in DDoS traffic ahead of the G7 summit (May 19–21), with attackers focusing on the Cabinet Office’s public relations infrastructure.
Overall, the government sector in APAC bore 27% of all DDoS attacks, a 108% year-over-year surge. However, attack volume on government targets declined in the second half of the year.
Government Attacks Declined in the Second Half of the Year
The shift began in September, with attacks on government targets dropping by 74%. As political targets saw less activity, attackers redirected their efforts to the financial sector.
Singapore, a key financial hub in APAC, exemplified this trend—DDoS attacks surged by 166% between September and October, with banks and payment processors being the primary targets.
Rise in Layer 7 and API-Targeted Attacks
In 2024, Layer 7 and API attacks surged by 85% and 76%, respectively. This increase closely followed the rise in attacks on the financial sector, the second most targeted industry.
Financial services, which depend heavily on API-driven platforms and web applications—especially for payment gateways and trading systems—are prime targets for these sophisticated attack methods.
DNS Attacks Showed Distinct Regional Growth in APAC
DNS attacks followed a unique pattern in APAC. While they accounted for just 4% of global incidents in Q1 2024, the region experienced a significant rise.
Although less frequent than HTTP/HTTPS attacks, DNS-based attacks in APAC grew by 54% year-over-year, with the telecommunications sector, the third most targeted industry, absorbing the majority of this increase.
Multiple Attacks Exceeding 1 Tbps Mitigated
In 2024, StormWall successfully mitigated multiple DDoS attacks exceeding 1 Tbps across the APAC region. These large-scale attacks impacted various industries, with financial services, telecommunications, and entertainment being the most affected.
Breakdown by Industry in 2024
Here’s how DDoS attacks were distributed across different sectors:
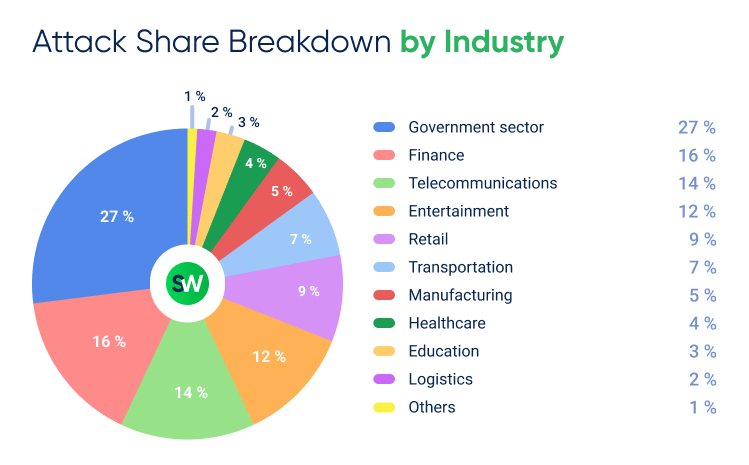
Industries with highest YoY growth in DDoS attacks in 2024:

Let’s unpack the top-3 most attacked verticals in more detail:
1. Government Sector
The government sector was the most targeted industry in 2024, accounting for 27% of all DDoS attacks in APAC—more than triple of its 8% share in 2023. It also saw the sharpest year-over-year growth, with a 108% increase in attack volume.
This surge was closely tied to key elections across the region:
- Taiwan: Government services faced double the usual attack volume in the days leading up to the January 13 elections, with over 800 incidents recorded on election day alone.
- Bangladesh: DDoS attacks spiked 71% during its parliamentary elections.
- South Korea: The most powerful government-targeted attack of the year hit 1.5 Tbps in Q2. The longest sustained attack lasted three days, maintaining a consistent load of 700 Gbps.
These attacks underscore how political events have become key drivers of cyber threats, with adversaries increasingly targeting government infrastructure during moments of national significance.
2. Finance Sector
The financial sector was the second most attacked industry, accounting for 16% of all DDoS attacks in APAC. It also experienced a 92% year-over-year increase, highlighting its growing vulnerability.
Election-Related Attacks on Banking
Political events directly impacted the financial sector. During Taiwan’s January 13 elections, Taiwanese banks faced a surge in DDoS attacks, with 89% of all financial sector attacks targeting banking operations. The majority of malicious traffic originated from China.
Shift Toward Profit-Driven Attacks
The nature of attacks changed in the second half of the year. As hacktivist activity declined in Q3 and Q4, attackers pivoted toward profit-driven targets.
A key factor was the sector’s increasing reliance on APIs:
- Over 1.3 billion banking API calls were recorded in 2024.
- API attacks surged 138% in Q3 alone, exposing vulnerabilities in financial services’ digital infrastructure.
This shift underscores how attackers adapt their strategies, initially exploiting political instability before refocusing on financial gain.
3. Telecommunications Sector
The telecommunications industry was the third most targeted sector, accounting for 14% of all DDoS attacks—an 86% increase from 2023.
DNS Attacks Exploited Telecom Infrastructure
Telecom providers rely heavily on DNS for routing calls, messages, and data, making them especially vulnerable.
- DNS-based attacks were a major threat, with DNS Amplification and DNS Flood attacks making up 45% of all telecom-related incidents.
- Both attack types exploit UDP protocol vulnerabilities, overwhelming servers with requests for non-existent domains.
- Essentially, attackers leveraged the industry’s dependence on always-on DNS services as a critical point of exploitation.
High Complexity and Multi-Vector Attacks
Telecom DDoS attacks became more complex:
- 85% of attacks used multiple vectors, making mitigation more challenging.
- The most common pattern involved simultaneous attacks across 5 to 8 different vectors.
This trend highlights how attackers are evolving their methods, using layered, multi-vector approaches to overwhelm telecom infrastructure.
DDoS Attacks in APAC: Country Breakdown
Here’s how DDoS attacks were distributed across APAC countries in 2024:
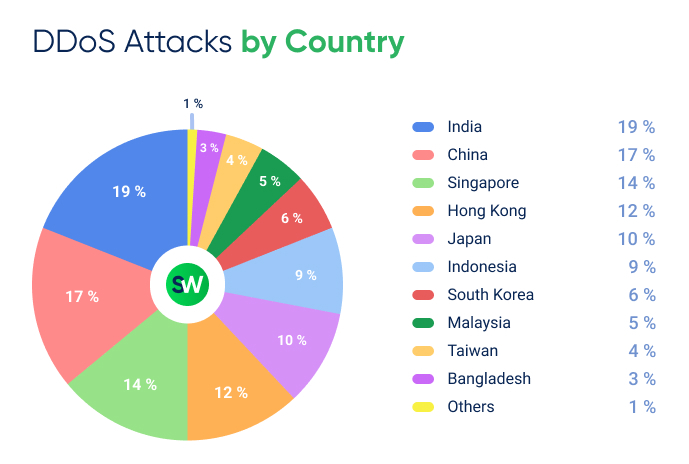
The attack landscape in APAC underwent notable shifts in 2024, with key countries experiencing both surges and declines in DDoS activity.
China experienced the biggest drop, with its attack share falling 9 percent from 26% to 17%—a nine-point decline that pushed it from the top spot to second place. This shift allowed India to take the lead, despite its slight decrease from 19% to 18%.
Japan saw the most dramatic increase, jumping from 4% to 10%. This six-point rise moved the country up four positions in the regional ranking.
Attacks on Indonesia and Singapore also increased, with Indonesia rising from 6% to 9% and Singapore climbing from 12% to 14%, reinforcing its position as a key financial and digital hub under attack.
In contrast, Malaysia experienced a notable drop, with its share declining from 9% to 5%. Meanwhile, Bangladesh entered the top 10, rising to 3% and replacing the Philippines, which held 2% in 2023.
Smaller shifts occurred elsewhere: Hong Kong dipped from 14% to 12%, South Korea edged up from 5% to 6%, and Taiwan increased slightly from 3% to 4%.
These changes highlight how geopolitical tensions, economic factors, and evolving attack strategies continue to reshape the cyber threat landscape in APAC.
Conclusions
As we analyze DDoS attack trends in APAC for 2024, key findings include:
- The government sector was the most targeted, accounting for 27% of all attacks with a 108% year-over-year increase. Attacks surged in the first half of the year but declined in the second half.
- Attackers shifted focus to financial services in the second half of the year, particularly in Singapore, where attacks rose 166% in September-October, primarily targeting banks and payment processors.
- Layer 7 and API-targeted attacks escalated, growing by 85% and 76%, respectively, aligning with higher attack volumes on financial institutions, where API-driven services are essential.
- India became the most attacked country, accounting for 19% of all attacks, while China’s share dropped by 9 percentage points to 17%.
- Japan saw one of the most significant shifts, with its share of attacks rising from 4% to 10%.
- DDoS activity followed two distinct phases: The first half of 2024 was dominated by election-related attacks and hacktivism, while the second half saw a return to profit-driven attacks, focusing on banks and telecom providers.
- Financial services and telecoms are expected to face the highest DDoS traffic in 2025, as attackers continue to target critical infrastructure for financial gain.
StormWall will continue to monitor these trends and support organizations in strengthening their defenses against evolving cyber threats.

DDoS Protection for Websites
- Activate protection in 10 minutes
- 24/7 technical support




















