Discovery
Researchers at SIDN Labs, (.nl domain zone), InternetNZ (.nz domain zone) and the University of Southern California (Institute of Information Sciences) publicly disclose tsuNAME, a vulnerability in DNS resolver software that could be exploited to launch DDoS attacks on authoritative DNS servers. Key Internet infrastructure of the national level could be at risk, according to researchers and practitioners.
How It Works
To understand the nature of the attack, you need to understand how DNS services work. Let’s say the network has a client device, a recursive DNS server, and an authoritative DNS server. Recursive DNS servers simply forward client requests to authoritative DNS servers.
Authoritative DNS servers are controlled by large organizations, which operate large – at the national level – segments of the internet. Authoritative DNS is maintained, configured and protected by qualified personnel, and attackers most likely will not be able to attack them through unpatched vulnerabilities. However, as it turned out, there is another way: to exploit the vulnerabilities of recursive DNS servers. After that, recursive DNS servers increase the number of requests to authoritative DNS servers hundreds and thousands of times, thereby leading to their failure.
In the advisory published by the researchers the simplest example of a circular dependency is given, which can serve as a trigger for sending a huge number of requests from a recursive DNS to an authoritative one:

As you can see from config_1, when accessing essedarius.net, the DNS service calls ns1.example.nl
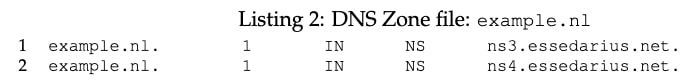
However, ifin the config_2 file of the domain zone of the site there is a dependency on essedarius.netexample.nl, thus a circular dependency arises, and the recursive DNS server starts constantly polling the authoritative DNS server.
Recursive DNS servers are much easier for attackers to exploit. They can generate such a volume of traffic that no authoritative DNS server can handle.
Who is at risk
As the experts note in their report the following DNS servers are exploited:
- Which cannot detect the cycle and start a continuous cycle between cyclically dependent records;
- Which do not cache cyclically dependent records.
Illustrative Case
On February 1, 2020, authoritative DNS servers in the .nz zone experienced an increase in total traffic of about 50%, from 800 million to 1.2 billion daily requests. During the investigation, experts determined that the cause of this traffic spike was due to a configuration error in only two domains. This mistake resulted in daily requests for these two domains increasing from 35K to an average of 269M per day! The problem was fixed only 16 days later, when the circular dependency was removed.
Just one malicious error in the configuration of the two domains resulted in a 50% increase in traffic to authoritative DNS servers. You can imagine what would happen if hackers wanted to replicate this type of attack using hundreds or thousands of domains.
How to protect yourself?
To mitigate the risks of TsuNAME-related attacks, network security experts recommend that operators of authoritative DNS servers detect and remove cyclic dependencies from their zones. To do this, they released open-source CycleHunter software — a tool that reads zone files and checks configs in search of cyclic dependencies (https://github.com/SIDN/CycleHunter).
However, experts also point out that dns records can change any time, and there is no permanent solution – you cannot perform such a check just once. This is why CycleHunter is recommended to be used on a regular basis, for example, as part of the process of registering a new domain name.




















