It’s no secret that DDoS attacks are a major disruptor of online services and can cause significant business losses. As attacks grow in power, the situation is becoming increasingly dangerous, and by 2024, DDoS could threaten the Internet itself.
You’re reading StormWall’s global DDoS Attack Report. We’ve compiled data on attacks targeting customers connected to our global network of scrubbing centers worldwide. Our network filters 4500 Gbps of traffic during peak periods. These are real-world denial of service campaigns that have impacted businesses in a wide range of sectors, and the strongest attack we mitigated in Q1 2024 reached 1.4 Tbps. This data allows us to share trends and insights you may not have previously known about the worldwide state of DDoS attacks.
DDoS Attacks in Q1 2024: An Overview
Overall, Q1 2024 was characterized by the impact of election campaigns and elections on DDoS activity. In 2024, 64 countries will hold or have held elections, including Taiwan, Bangladesh, Azerbaijan, Senegal and Russia. We see a direct correlation between election periods and the increase in attacks. Overall, the geopolitical situation continues to influence DDoS attacks and its impact is evident in the list of most targeted industries. Attacks on government institutions dominate, accounting for 34% of all incidents.
Hacktivists also continue to target active geopolitical actors and conflict parties. For example, politically motivated DDoS attacks have occurred in the US, Russia, India, Indonesia, Israel and other countries.
DDoS Attacks in Q1 2024: Key Trends
Below we’ve summarized the key trends we’ve seen in the first quarter of the year. As a reminder, these trends follow a record-breaking 2023 in terms of both attack volume and sophistication, following a 118% year-on-year increase in multi-vector attacks.
- The average number of devices in botnets increased fivefold from 4,000 to 20,000 devices in Q1 2024. Botnets are now powerful enough to threaten the security of the internet globally, for example by targeting DNS services, the internet’s address book that links IP addresses to human-readable domains. DNS outages can result in requests to websites across entire regions, states or countries no longer being resolved.
- There’s a strong, ongoing influence of geopolitics on the DDoS landscape. This is manifested in the fact that a large proportion of DDoS attacks fall on countries involved in ongoing conflicts.
- We’re feeling the effect of elections. 2024 can be described as an election year, with some 64 countries, 17 of them in the first quarter of the year, electing key government officials. This had a direct impact on what industries are impacted by DDoS attacks, resulting in government and telecommunications services being heavily targeted (attacks on government services accounted for 34% of incidents, and attacks on telecom industry — 14%).
- The proportion of hacktivism is increasing. The proportion of attacks launched by hacktivists relative to incidents launched by for-profit DDoS criminals is steadily increasing.
- In Q1 2024, we saw an increasing number of DDoS attacks targeting web applications and APIs. These attacks mostly affect the retail, transport and logistics industries.
- Carpet bombing attacks are becoming more common. In carpet bombing attacks, hackers choose multiple targets in an attempt to overwhelm the entire network, rather than focusing on a single IP address. We’re tracking an increasing number of carpet bombing attacks in Q1 2023.
How Elections Impacted the Global DDoS Landscape
Hackers tend to follow major events, whether political or commercial. In Q4 2023, we saw this with Black Friday, which manifested itself in a 127% increase in attacks on the retail sector, making it the second most targeted industry that quarter. Overall, wherever there is public attention and a need for services to function without fault, there is an opportunity to disrupt, cause chaos and extort.
The biggest event in Q1 2024 was undoubtedly the elections that took place in several countries, and against the backdrop of the elections, we saw an increase in DDoS attacks, mainly on government services and election campaigns.
What’s the impact?
The government sector remains the most targeted vertical at 34%, up 62% from last quarter and 47% year-on-year.
How many elections were held in Q1 2024 to cause this to happen? Let’s recap. January saw parliamentary elections in Bangladesh, Bhutan and Tuvalu. Finland and the Comoros Islands held presidential elections. Taiwan held both parliamentary and presidential elections. In February, Cambodia, Pakistan and Belarus held parliamentary elections, while Senegal, Mali and Azerbaijan elected new leaders. Finally, parliamentary elections were held in Iran and Portugal in March. Russia held presidential elections from 15 to 17 March.
Important elections took place in Taiwan, Russia, Azerbaijan, Bangladesh and Senegal. In each of these regions, we can clearly see the profound impact of elections on the number of DDoS attacks. If we break it down country by country, here’s how much malicious traffic increased in Q1 2024:
- Taiwan: 148% increase.
- Russia: 126% increase.
- Azerbaijan: 114% increase.
- Bangladesh: 84% increase.
- Senegal: 71% increase.
DDoS Attacks in Q1 2024 by Industry
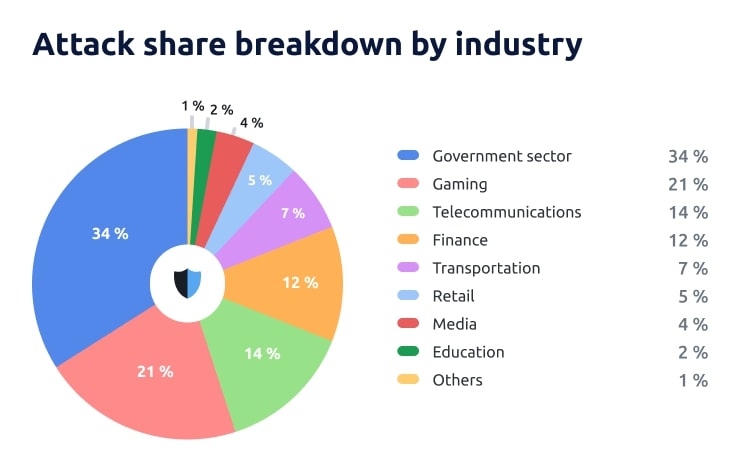

Here are the main trends to highlight this quarter:
- Attacks on the gaming sector were widespread — this category didn’t warrant its own highlight in Q3 2023, but this year it saw a staggering 83% increase in attacks, becoming the vertical where the most new attacks occurred.
- Also noteworthy are the attacks on the government sector (34% share, 47% growth year-on-year), which are rising sharply from last quarter and steadily year-on-year.
- As a warning to companies in the media vertical, there were similar DDoS campaigns designed to prevent the free flow of information. As a result, the media sector is now a separate category in the list of most attacked sectors, with a 4% share. This activity takes place in the context of elections.
- Retail saw a reverse trend. The shopping season is over and we see this reflected in the overall decrease in attacks compared to other sectors. There is a modest overall growth of 18% year-on-year, which is the result of an overall increase in DDoS attacks, but this is comparatively small compared to the 127% growth we saw last quarter.
Government sector
The share of DDoS attacks targeting the government sector is 34%, an increase of 47% year-on-year. This is up from 21% in the previous quarter, due to elections in several countries.
In particular, elections in Taiwan, Bangladesh, Azerbaijan, Senegal and Russia painted targets on the back of government infrastructure involved in election campaigns in those regions.
In total, 64 countries in Europe, Asia and the MENA (Middle East and Africa) region have held or are due to hold elections this year. This means that government agencies in these regions are at high risk of falling victim to a DDoS attack.
Gaming
Gaming was the second most attacked vertical in Q1 2023, with a 21% share and the highest growth we saw at 83% year-on-year.
For example, DDoS attacks hit Minecraft servers. Minecraft has a player base of over 500 million registered users, of which 166 log on monthly, meaning the attack affects more people than the population of the US.
Learn how to protect gaming services against DDoS attacks.
Why hackers target games?
The reasons for attacks on games vary. In some cases, they are initiated by competitive players facing a stronger opponent. They try to gain an advantage by creating a higher ping. In other cases, the attackers aim to disrupt the gaming experience: preventing players from logging in, increasing loading times, and generally making the game unplayable. This leads to damage to reputation and loss of player numbers, which the attackers can use for extortion.
Telecommunications
In third place by attack share (14%), is the telecomunicatiosn industry. In this vertical, we saw a 29% increase of attacks YoY. Overall, the position of the telecom industry in the list remains similar to last quarter — both in share and increase of attacks.
Attackers target this industry because of its massive attack surface. Downtime at a communications service provider (CSP) means that all of its customers experience outages because the infrastructure they rely on is down. Telecommunications companies are targeted by hackers looking for blackmail, by political actors, and even by those looking to practice an attack on a larger target.
Finance
The financial sector accounted for 12% of DDoS attacks, an increase of 26% year-on-year. In particular, financial services in the Middle East continue to be heavily targeted. This is a result of the Israeli-Palestinian conflict, which began in October 2023 and is still ongoing.
Attacks in this vertical were prevalent in the MENA and APAC (Asia-Pacific) regions, with some exceeding 800 Gbp/s.
Transportation
It accounted for 7% of attacks in Q1 2024, and saw the third fastest growth rate at 38%. Interestingly, it’s in the transport sector that we’ve seen DDoS actors favour attack strategies that, while not necessarily new this quarter, are gaining popularity. Namely, attackers are focusing on overloading web applications and APIs.
For example, modern seaports use vessel management software that integrates with accounting systems and weather data. This software communicates with external services via APIs, and it’s operators can interact with it via a web application. By disabling these components, attackers can freeze a port’s operations. This can cause significant financial damage.
Attacks of this nature are not only profit-driven, taking advantage of the need for transport hubs to resume operations, but also stem from hactivism, as transport and logistics services play a vital economic role.
Retail
The retail industry is taking a bit of a breather compared to the last quarter of 2023, in terms of attack growth and share. In Q1 2024, attacks grew by a staggering 127% in that quarter — this quarter they grew by just 18%. Attack share is also down to 5%, compared to 17% in the last period.
The nature of the DDoS landscape in 2023-2024 is such that modest growth looks like a period of calm, but this impression is false. After all, after the 127% increase in attacks in Q4 2023, volume stayed at that level and still increased slightly, so it’s important to remember that this industry’s slide to lower positions in terms of overall share is relative to faster growth in other sectors.
Learn how to protect your online store from DDoS attacks.
Media
The media sector saw an increase in DDoS attacks of 4% and 16% respectively. Attacks on this vertical were related to political elections, which took place in more than 15 countries in Q1 2023. The reason for the attacks is hacktivism. Media websites are, of course, important platforms for political candidates. It can be advantageous for rivals to disrupt sources of information, especially to suppress unfavourable stories.
The takeaway is that despite the modest 4% share of attacks, the increase in attacks on the media is significant. It illustrates how DDoS is becoming a source of disinformation on a global scale.
Education
In the education sector, there were 2% of attacks, accounting for an 11% share of the total. Although the number of attacks decreased by 50% from Q3 2023, the growth rate remains consistent. During the last period, we recorded a 12% YoY growth, only 1% higher than in Q1 2023. Similar to the retail sector, when holiday seasons see DDoS activity skyrocket, attacks on education often peak during specific periods such as admissions, and are carried out by both hacktivists and students attempting to disrupt exams.
DDoS Attacks in Q1 2024 by Country
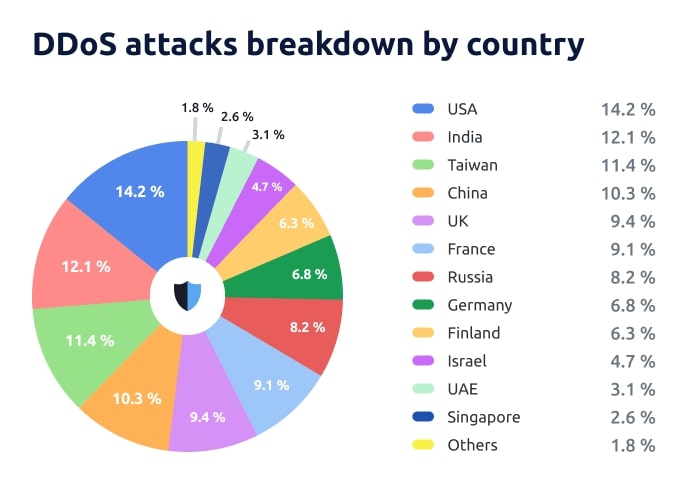
Looking at how DDoS attacks were distributed across countries in the first quarter, we continue to see the effect of elections. Taiwan, for example, ranked third in the number of attacks (11.4%), which we have never seen before. Usually, the top three countries are the United States, India, and China, with their positions shuffling within the top three. Attacks in Taiwan were particularly notable for their complexity and strength, with China being one of the main geographical sources of the attacks.
Interestingly, Russia (8.2%) and Finland (6.3%) also appeared in the top ten most attacked countries. In Russia’s case, the country returned to this position. Here, the effect of the recently held elections can also be traced. For the first time, Russians could vote on online platforms, and hackers took advantage of this, making these platforms their target. The services were disrupted on March 15th, at least once. In total, about 12 million DDoS attacks took place during the elections in Russia.
On the other hand, the number of attacks decreased in Israel (3.1%), and Singapore’s attacks halved compared to Q4 2023 (currently 2.6% against 6.3% in the previous period).
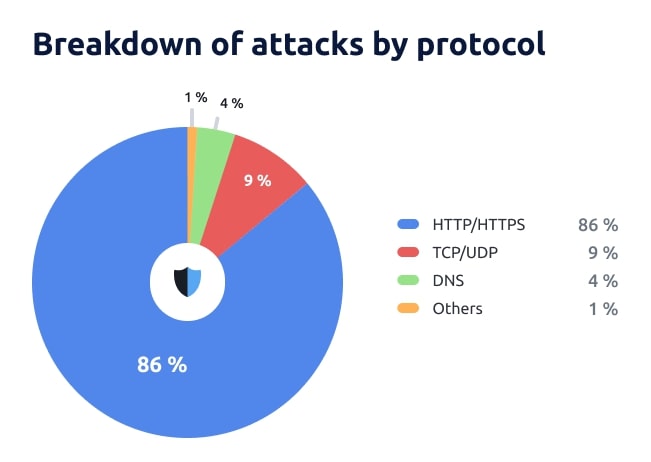
DDoS Attacks in Q1 2024: Breakdown by Protocol
When we look at the different types of attacks, the majority (86%) target HTTP and HTTPS protocols. TCP and UDP protocol attacks come in second (9%), though they’re not nearly as common. DNS attacks (4%) rank third in terms of popularity.
Conclusions
As we summarize the DDoS attack trends for Q1 2024, several key points stand out:
- The geopolitical landscape, particularly elections in 64 countries including Taiwan, Bangladesh, Azerbaijan, Senegal, and Russia, had a significant impact on the DDoS attack landscape. Government services were the most targeted, accounting for 34% of all incidents, a 47% year-on-year increase.
- Hacktivists played a prominent role, targeting active geopolitical actors and conflict parties in the US, Russia, India, Indonesia, Israel, and other countries. The proportion of hacktivism-driven attacks relative to for-profit DDoS attacks is steadily increasing.
- The gaming industry saw the highest growth in attacks at 83% year-on-year, becoming the second most targeted vertical with a 21% share. Attacks on gaming servers, such as Minecraft, affected millions of players globally.
- DDoS attacks targeting web applications and APIs are on the rise, particularly affecting the retail, transport, and logistics industries. These attacks can cause significant financial damage and stem from both profit-driven and hacktivism motives.
- Botnets have grown in power, with the average number of devices increasing fivefold from 4,000 to 20,000 in Q1 2024. They now pose a threat to the security of the internet globally, potentially targeting critical infrastructure like DNS services.
As botnets continue to grow in power, it’s more important than ever for organizations of all sizes to have strong DDoS protection in place. We can’t stress this enough. Making sure your defenses keep up with the capabilities of attackers is key to reducing the risks that DDoS attacks pose in the near future, ensuring that your business is safe and running smoothly.

DDoS Protection for Websites
- Activate protection in 10 minutes
- 24/7 technical support




















